- Opportunistic Ransomware is generally on the decline
Ransomware worked well for so long because bad guys made money, and made money quickly from ransomware campaigns. Starting in 2017 and continuing to 2018 there has a been a steady decline in ransomware campaigns. The reasons for that are twofold, but interconnected:
- Exploit Kits (EK) have virtually disappeared. The EK market has always been volatile, but as one EK faded away there was generally another one to take its place. That has not been the case. As the big EKs of 2016/2017, Sundown, Neutrino, and RIG, have fallen off, no new EKs have stepped in to fill the void. This has occurred, in part, because there are fewer 0-day browser exploits to use in these EKs, rendering them less effective. Of course, this is somewhat of a chicken and an egg problem. The most popular 0-day exploits in years past were those targeting Adobe Flash. However, Adobe Flash installations are at an all-time low (https://www.bleepingcomputer.com/news/security/google-chrome-flash-usage-declines-from-80-percent-in-2014-to-under-8-percent-today/), so there is a much smaller attack surface, meaning even if there were a large number of Adobe Flash 0-Day exploits, there would be fewer victims to target. With fewer active EKs there are fewer delivery mechanisms for ransomware, forcing attackers to rely more heavily on phishing campaigns, which are becoming less effective.
- The EKs that are still around, such as RIG, have switched to delivering cryptocurrency miners rather than ransomware (https://www.bleepingcomputer.com/news/security/the-rig-exploit-kit-has-forsaken-ransomware-for-coinminers/).
In general, there has been a move away from ransomware to cryptocurrency miners, largely for the same reasons that lead to the rise of ransomware in the first place. At this point, cryptocurrency miners are more profitable than ransomware. They are also more difficult to defend against. Organizations have gotten better at securing their networks to prevent successful ransomware attacks, but blocking cryptocurrency miners is a much bigger challenge. Until the security community catches up, cryptocurrency miners will continue to be profitable for attack groups.
- There will still be some industries that are targeted
Some industries are still being targeted and will continue to be targeted by ransomware campaigns. Industries like healthcare, and more specifically hospitals, have continued to be lucrative targets by attackers. Figure 1 shows that hospital attacks have not abated recently, instead they continue to move along at a steady pace and continue to be effective.
This is part of the trend mentioned last year that has continued: “Ransomware will become just another tool in the hacker utility belt.” While overall cyber criminal based ransomware attacks are on the decline in 2018, ransomware is still used on a case by case basis rather than large scale ransomware campaigns.
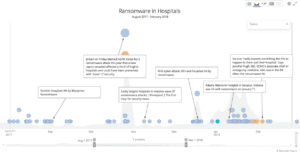
Figure 1: Ransomware attacks on hospitals continues to rise
- Boutique Ransomware campaigns will continue
While large-scale ransomware declined toward the end of 2017 the balkanization of ransomware continues to increase. There are ransomware campaigns happening, but they are reaching smaller audiences. At the end of January 2017 Recorded Future was tracking 635 different ransomware variants, while at the end of February 2018 we are tracking 1105 different variants. That is a 74% increase in the number of variants we are tracking in just 13 months.
2015, 2016, and early 2017 saw the emergence of a few, widely distributed, ransomware campaigns like Locky and Cerber. While these ransomware variants are still being distributed, albeit on a much smaller scale than in previous years, there has been a growth in other ransomware families that pop up for a few weeks or months and then disappear.
These new smaller campaigns are generally distributed to hundreds of thousands of potential victims, rather than tens of millions at a time. This trend will continue in 2018 as malware developers look to continue to add ransomware to newly discovered attacks techniques.
- The line between cyber criminals and nation state attacks will continue to blur
In 2017 I wrote “Similarly, there will not be a Mirai-style botnet installing ransomware.” I was partially correct. While there was not a Mirai-style botnet installing ransomware, 2017 did see the rise of the so-called ransomworm, with WannaCry, NotPetya and Bad Rabbit leading the way. These worms were interesting for two reasons:
- The sheer amount of damage and destruction they were able to cause in a very short period of time.
- They demonstrate the interplay between cyber criminal organizations and nation state actors.
WannaCry and NotPetya were not criminal campaigns, they were at best distraction campaigns and at worst destruction campaigns and both appear to have been launched by nation state actors using what had traditionally been cyber criminal tools. But, even in nation state style attacks, ransomware can be an effective tool in disrupting operations. While the nation state actors may not care about collecting the ransom, they certainly care that their targets are unable to access their files and that their workflow is disrupted for days, weeks, or in some cases months.
On the other hand, Bad Rabbit appears to have been carried out by a cyber criminal, using techniques learned studying the WannaCry and NotPetya campaigns. This doesn’t just apply to ransomware, it is happening across all types of cyber attacks. Cyber criminals are learning from nation state actors while nation state actors are learning from, and using the tools of, traditional cyber criminal activity. This trend will continue to grow in 2018 and beyond.
- Ransomware-as-a-Service (RaaS) will continue to be popular
The one area of ransomware that appears poised to remain popular is RaaS. RaaS allows attackers to rent ransomware infrastructure rather than develop it themselves. The attacker generally pays an upfront fee and the author of the RaaS keeps a small percentage of each ransom paid. Generally, the rentee is allowed to set the ransom price and build the attack campaign.
RaaS is attractive to less experienced attackers because it allows them to get into the ransomware game quickly and painlessly and, they think, they can start making money quickly.
But RaaS appeals to more experienced hackers as well because it guarantees them a revenue stream, selling the RaaS to inexperienced newcomers. In fact, the three most popular ransomware strains of 2018, GandCrab, Saturn and Data Keeper have all been RaaS ransomware families (see Figure 2). Because there are always people looking to make a quick buck and there are always those who are willing to take their money it seems like RaaS will continue to thrive through at least 2018.
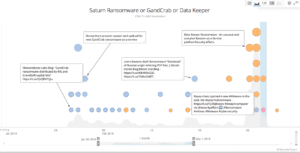
Figure 2: Mentions of GandCrab, Saturn and Data Keeper Ransomware Families
Conclusion
While it won’t be as big of a menace in 2018 as it was in 2016 and 2017, ransomware will continue to be a threat to both individuals and organizations. Some industries, such as healthcare, will continue to be heavily targeted by ransomware campaigns, but most industries should expect to see a drop in ransomware, overall. That being said, some of the tools developed by the actors behind ransomware, including fileless malware and encryption techniques, will continue to be used by those actors, as well as others, in different types of attacks. Don’t be surprised if there are more state-sponsored disruption campaigns in 2018 using tools originally designed for ransomware attacks.
[su_box title=”About Allan Liska” style=”noise” box_color=”#336588″][short_info id=’104126′ desc=”true” all=”false”][/su_box]






