With multi-layer cybersecurity defenses improving, hackers are going to the human attack surface with social engineering and phishing attacks like never before. According to industry reports, over 90 percent of breaches start with phishing. And it shouldn’t be a surprise. With stronger defenses, direct network and machine exploits are less common. Hackers need an easier way in and that’s people, your organization’s employees.
Today, hackers are preying on human fallibility with an expanding array of sophisticated phishing attacks both within email and beyond the inbox on the Web. And credential stealing remains one of their favored methods to gain entry into corporate networks.
Hackers now rely on a broad range of phishing attack vectors to trick users into giving away their credentials and data. These dangerous new phishing attacks might be carried out via deceptive and convincing pop-ups, ads, search results, social media, chat and IM applications, rogue browser extensions, and web freeware, and even “trusted” apps downloaded from app stores.
High-risk IP addresses continue to cycle between benign and malicious to avoid detection, and the top 10,000 IPs most often associated with malicious activity changed status an average of 18 times throughout the past year, according to the 2018 Webroot Threat Report.
Such attacks bypass existing defenses including firewalls, anti-virus protections, and secure email and Web gateways. They are file-less and look like innocent Web traffic that is specifically designed to elude defenses by delivering the malicious “payload” via HTML and JavaScript. Most phishing sites were only online for four to eight hours, according to Webroot, making it very hard to update defenses to block them before they’ve already moved on. Therefore, protecting against these attacks involves detecting and blocking them at the common Web delivery point, in near real-time, which can be a difficult task.
Recently, we uncovered an alarming type of phishing attack that is based on so-called replica sign-in pages for federated account log-ins. This type of attack works by playing into the human brain’s tendency to give priority to well-known visual icons, in which case the mind tends to “see” what it thinks it has seen, or rather what it expects to see.

Figure 1: Clicking on any of the above icons to access Dropbox pops up a new browser window that prompts the user to enter his or her credentials.
Replica phishing pages carefully duplicate the logos, colors and fonts from popular global brands such as Google, Microsoft, Dropbox and Yahoo. These imitations are often so realistic that they lure users into giving away their credentials. Some of these log-in pages come complete with a functional “Password Reset” option. Others include requests for secondary email accounts, mobile phone numbers, or one’s answers to security questions to ostensibly provide “enhanced security.” Talk about social engineering – the bad guys are banking on the user’s trust and familiarity with normal security procedures to finagle yet more user secrets!
To make matters worse, we are seeing more and more multi-brand phishing pages. With this tactic, attackers incorporate a fake web page that displays multiple brands simultaneously. In one example depicted above, the attacker displays a custom Dropbox phishing page, but the user can only gain access by entering personal credentials from a separate trusted, federated email log-in source of their choice.
Regardless of which pop-up credential the user selects, the form will submit the stolen information through a php script of the same name as the pop-up, all hosted on the same server. For each php, the attacker writes the code to forward the collected information to a specific repository email address.
In the Gmail example below, the attacker advances past the Dropbox log-in to coax out the victim’s Gmail recovery phone number and email address as well. Once the “Continue” button gets pressed and the credentials have been sent to the repository email address, the victim gets redirected to a Google Docs URL.
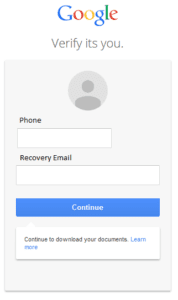
Figure 2: Even threat researchers can be fooled into giving away personal credentials through this highly realistic Gmail recovery popup.
Many security professionals try to offset the risk from these sorts of attacks by training their employees on how to identify and avoid such fake sign-in pop-ups and web pages. However, the attackers are creating more sophisticated and legitimate-looking phishing attacks every day, which can be quite hard to detect – such as in the examples above. And despite a growing focus on user awareness and training sessions, a distracted, multi-tasking workforce is still fallible, and will still make mistakes.
To detect these kinds of malicious phishing sites and protect employees from falling prey, phishing protection systems must be informed by real-time analysis and detection of zero-hour phishing threats on the Web. The system must make out the underlying context of the message and work backwards and forwards from the final attack screen to definitively identify phishing sites before a user can take the bait and share compromising info.
Training the workforce to protect itself against these new replica credential attacks is not good enough. For sufficient protection from these fast-moving and convincing phishing attacks, our phishing security systems need to imitate a humanlike mentality but with the speed and scale required to protect large organizations with lots of Internet traffic. This approach requires putting a contextual frame and real-time phishing site analysis in place to identify these latest replica sign-in pages.






