Phishing is a business, much like any other, that’s designed to make money. And because the bad actors are keenly aware of how current technologies are trying to catch them, they have developed new techniques for not getting caught and staying in business.
Today the hackers are capturing valuable personal information and quickly moving on to evade detection. One of the most dangerous trends involves web page domains and URLs which change so fast that standard blacklist-based engines can no longer keep up. The life-span of a phishing website URL has decreased significantly since 2016 (see diagram below). In fact, our threat intelligence feeds are now showing an average URL life-span of just 40 to 50 minutes, while the median time for the first user to click on a phishing URL is a mere four minutes.
To camouflage their intentions, these malicious URLs are often hosted on compromised sites that have good domain reputations. Of the tens of thousands of new phishing sites that go live each day, the majority are hosted on compromised, but otherwise legitimate, domains. These sites would pass a domain reputation test, but they’re still hosting the malicious pages.
People innocently click on such pages and within a few minutes the bad actors have collected all the data they need before moving on to the next site. By the time the security teams have caught up, that attack is already long gone and being hosted somewhere else.
The Fleeting Timeline of a Phishing Attack
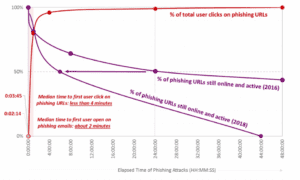
Source: Reducing the Risk of Phishing Attacks: The Race is On (Aberdeen Group, December 2018)
Approximately 90 percent of the phishing URLs detected by our threat feeds are either hosted on a compromised domain, or hosted on legitimate cloud services such as SharePoint, GoDaddy, and Amazon AWS. Bad actors know that blacklisting Amazon or SharePoint isn’t feasible, so any online services that provide HTML hosting are prey for these types of attacks, as the bad actors attempt to evade domain reputation engines.
Buying Phishing Data from Infected Machines on the Dark Web
As phishing attacks have become more sophisticated, they have also become easier to pull off. This is because most targeted attacks stem from bad actors buying their data on the dark web, the hazy part of the Internet that is intentionally hidden from search engines, uses masked IP addresses, and is accessible only with a special web browser.
Gone are the days when hackers or nation states had to actually send out targeted phishing emails and work hard to penetrate an organization. Now any bad guy can just go to the dark web and buy infected machines from the provider of their choice.
Nearly every organization today has some infected features and employees with compromised information. All the hackers need to do now is pay a middleman to gain access. They don’t have to scam someone themselves, because the compromised machines with malicious browser extensions or TeamViewer screens are already available for sale.
Our security researchers are seeing tens of thousands of new phishing sites daily on average, but it varies day-to-day depending on the activities of the bad actors. For instance, on weekends we might see volumes decrease by 50 percent because the hackers take weekends off too – phishing is a business, after all. But by Sunday morning Pacific time, we usually see the volumes pick up again, and by Monday and Tuesday it’s back to full speed ahead.
What’s needed to address this problem is a new approach to threat intelligence that is more automated, with higher levels of accuracy. By evaluating many more characteristics of each site in the cloud, such a platform can immediately render a definitive verdict: Malicious or Benign. This approach is much different than legacy threat feed approaches that only offer a probability of being malicious and suspicious. By taking a binary Yes/No approach, new security strategies can provide a blocking threat feed with a continuously updated list of zero-hour phishing URLs, domains, and IPs, including indicators of compromise to stop attacks before they begin.
A real-time threat intelligence feed instantly sifts through all the dynamic data collected from multiple proprietary sources and proactive threat hunting. Another major benefit of a real-time threat feed for instant blocking is the output of near-zero false positives, which helps protect against blacklisting legitimate websites.
In the fast-changing world of phishing security, speed really matters because these sites are here today, gone today. If a feed is just 45 minutes late, there’s a 90% chance the attack has already disappeared. A better approach combines live data streams without any manual intervention to provide the blazing speed required to protect organizations from being phished in real-time. Otherwise, detecting phishing URLs after two hours or more becomes useless because bad actors have already obtained the information they want and moved the attack elsewhere in search of new business.






