Being certain that most readers will have noticed the levels of successful cyber-attacks carried out against public services such as Government, and in particular the scattered Local Authorities who have been put on notice by the U.S. Department of Homeland Security (DHS), Federal Bureau of Investigation (FBI), and the UK’s National Cyber Security Centre (NCSC) who released a Joint Technical Alert about malicious cyber activity. According to the alert, the targets of such malicious cyber activity are primarily government and private-sector organisations, critical infrastructure providers, and Internet Service Providers (ISPs) supporting these sectors, so I guess with that in mind you would expect some action to take place to secure the front door Security Posture – right? In fact, as far back as 22018, the Big Brother Watch published a paper title Cyber Attacks in Local Authorities which can be found at the URL below:
https://bigbrotherwatch.org.uk/wp-content/uploads/2018/02/Cyber-attacks-in-local-authorities.pdf
Yet, notwithstanding the on-going notifications, alerts and advisories that have been distributed, it would seem they may be finding on deaf ears, with the likes of the Lincolnshire Local Authority falling foul of a Ransomware attack which in the hands of a Third Party Outsource Provider. And add this type of imposition a report issued by the insurance broking firm Gallagher, who reported that Local Councils across the UK faced as many as 263 million cyber-attacks in the first half of 2019, averaging around 800 cyber-attacks every hour (Freedom of information (FOI) requests revealed).
The real concern here of course is, it is not just the UK who suffer from such adverse interest, and when one considers the aspirations of the strive to deliver Digital Transformation, and Smart Cities such as the NEOM Project in Saudi Arabia, one may only assert that in such security implicated deployments as these, somehow they have surmounted the insecurity issue, and are building their deployments within an overarching, and underpinned by a robust security structure – but I do have my doubts!
With the known-known data and intelligence in mind, I commenced on a small research venture to evaluate, though Open Sources, the overall security posture of a sample of 10 + 1 Local Authority Domains, plus a Local Parish Council who have just undergone a major upgrade to their web deployment.
My overarching concern here is, with Local Authorities, Government Agencies, and those evolving Transformed Smart Cities do, and will have a significant custodianship of data on their local populous, and as such the risk is thus increased by a factor of the local domain’s public digital presence!
So, selecting a sample of the 10+1 domains at random, they were evaluated against a number of criteria which are shown below – and the results are, or should be of great concern to any resident who falls within their area of data capture, and can only suggest or infer for all those who have not been evaluated what the level of insecurity is expected to be.
HAMPSHIRE
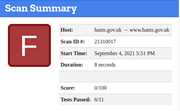
5,621 – Compromised Accounts
128 – Breaches
38 – Pastes – 5 Sensitive
14,498 – Data Leaks
5,360 – Compromised Passwords
Privacy
No tracking detected.
SOUTH DUBIN COUNTRY COUNCIL
0 – Compromised Accounts
0 – Breaches
0 – Pastes
0 – Data Leaks
0 – Compromised Passwords
Privacy
1 x Ad Trackers associated with the Domain.
GLASGOW
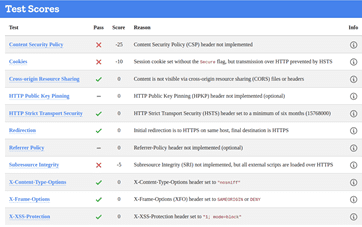
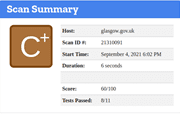
1,427 – Compromised Accounts
59 – Breaches – 1 Sensitive
8 – Pastes – 5 Sensitive
3,654 – Data Leaks
1,358 – Compromised Passwords
Privacy
No tracking detected.
BIRMINGHAM
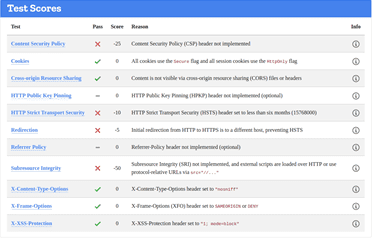
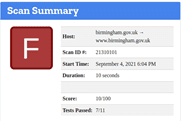
https://www.birmingham.gov.uk/
2,873 – Compromised Accounts
93 – Breaches
18 – Pastes – 5 Sensitive
8,339 – Data Leaks
2,622 – Compromised Passwords
Privacy
3 x Third Party Cookies detected.
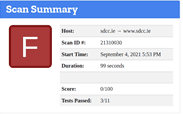
LINCOLNSHIRE
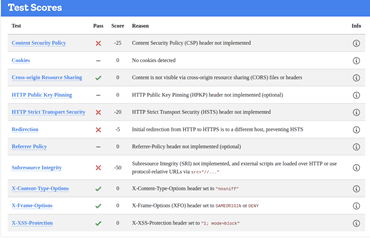
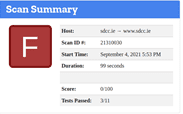
https://www.lincolnshire.gov.uk/
1,550 – Compromised Accounts
63 – Breaches
14 – Pastes – 2 Sensitive
3,931 – Data Leaks
1,453 – Compromised Passwords
Privacy
The following were detected which were associated with the Domain:
2 x Ad Trackers discovered
2 x Third Party Cookies discovered
Google Analytics discovered to follow visitors across the Internet
LEICESTER
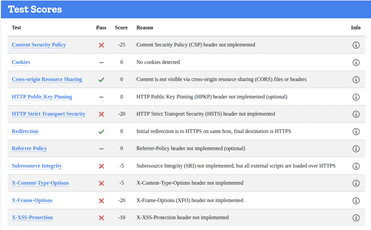
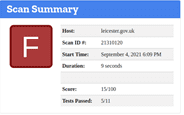
2,635 – Compromised Accounts
17 – Breaches
13 – Pastes – 5 Sensitive
6,874 – Data Leaks
2,537 – Compromised Passwords
Privacy
The following were detected which were associated with the Domain:
1 x Ad Tracker
There is an indication that this website could be monitoring keystrokes and mouse-clicks.
NOTTINGHAM
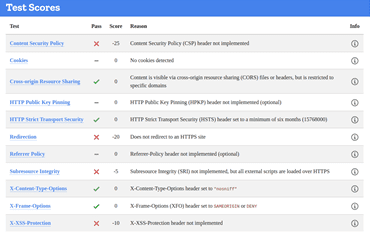
http://www.nottinghamcity.gov.uk/
1,747 – Compromised Accounts
18 – Breaches
14 – Pastes – 4 Sensitive
4,796 – Data Leaks
1,585 – Compromised Passwords
Privacy
The following were detected which were associated with the Domain:
4 x Ad Trackers discovered
There is an indication that this website could be capturing user keystrokes.
This site tells Facebook of user visits to site.
Google Analytics discovered to follow visitors across the Internet
BELFAST
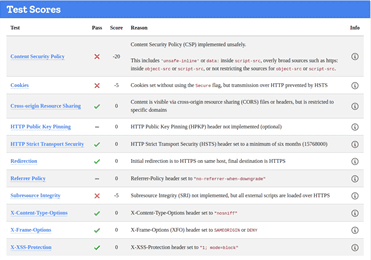
https://www.belfastcity.gov.uk/
1,710 – Compromised Accounts
50 – Breaches
7 – Pastes – 4 Sensitive
2,798 – Data Leaks
1,064 – Compromised Passwords
1 x Third Party Cookie discovered
NORWICH
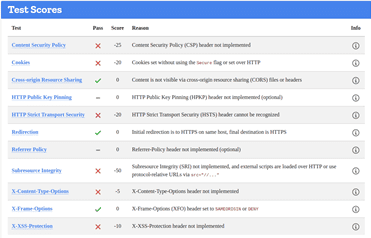
https://www.norwich.gov.uk/site/
287 – Compromised Accounts
33 – Breaches
4 – Pastes – 2 Sensitive
725 – Data Leaks
273 – Compromised Passwords
No discoveries.
LIVERPOOL
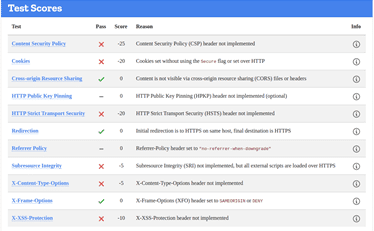
2,910 – Compromised Accounts
61 – Breaches
12 – Pastes – 3 Sensitive
7,166 – Data Leaks
2,865 – Compromised Passwords
No discoveries.
DEEP DIVE OSINT INSPECTIONS AND DISCOVERIES
Out of the above domains, two (Lincolnshire and Nottingham) were selected for additional Open-Source inspections and discoveries, and the finding were similar, and also concerning, with the following results:
Lincolnshire: The Lincolnshire domain was hosting the following discovered vulnerable points on their deployment:
13 HIGH Risk areas of security exposure
28 MEDIUM …………………………….
73 LOW ……………………………….
3 INFO ………………………………….
These included discoveries relating to Unencrypted Password Pages, entities which were considered Malicious, and Certificate issues. Added to this was several Leak Site entries Blacklisted IP Addresses, and 223 Co-hosted sites, and multiples of Hacked Email Addresses e.g., as per the below redacted example:
xxx_planningenquiries@lincolnshire.gov.uk
Nottingham: The Nottingham domain was hosting the following discovered vulnerable points on their deployment:
9 HIGH Risk areas of security exposure
15 MEDIUM …………………………….
79 LOW ……………………………….
Local Parish Councils
Whilst conducting this research project, I also considered all of those scattered Local Parish Councils which serve their local communities and being aware my own had just undertaken a web upgrade, I used that as an example to put into the sample. Here we are inspecting a Domain which services around 7,000 residents with information relating to their community, and as such it is not in any way considered to be critical – but the points of consideration are:
- Should such a Domain be asserted to be secure?
- Should it be deployed in such a posture it cannot be used for any other jump point purpose?
- Should the Domain consider the potentials of takeover, and misinformation?
- Should we expect those who develop such deployments to inbuild security?
Post a very short duration of an OSINT Technical Inspection, the updated site was discovered to be hosting 508 points of security exposure and vulnerability:
493 HIGH
4 MEDIUM
11 LOW
No discoveries.
The discoveries were made up of a range of insecure areas, from unencrypted web pages that captured use passwords and credentials (see below image), poorly configured web technologies, multiple open unencrypted TCP/UDP Ports, Outdated and vulnerable SSH Protocols, through to Digital Certificate security issues.
Unencrypted web passwords and credential input pages
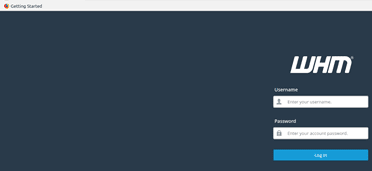
The question that arises here is, in an age in which many people suffer compromise, data leakage and other forms of Digital Abuse, is it ethical to allow such community focused sites to be evolved in a totally insecure state; or should be anticipate better from those who develop such sites on behalf of their trusting, paying clients?
Note on HTTP SCANS
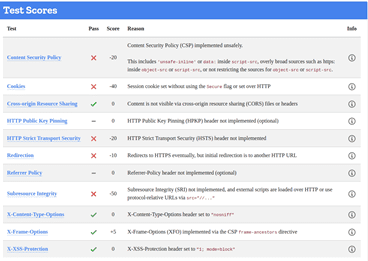
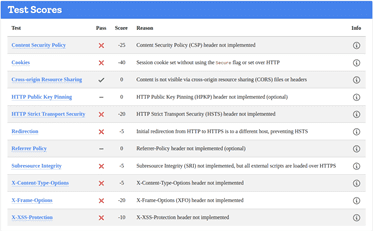
Whilst a site is discovered to be based on an underperforming security posture, when examined at the SSL level only, it can give a false sense of security – in the case on the Lincoln Domain which failed the HTTP examination, QUALYS SSL LABS report and A Rating, whilst hstspreload.org report an insecure entity (see below):
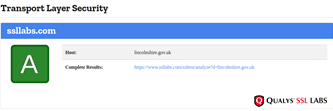
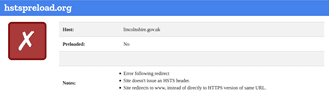
HTTP Scan Scoring: The notified grade is based on a scoring system out of 100 points, in which every security flaw the tool identifies will dock you a certain number of points – some issues are weighed more than others! For example, no Content Security Policy – 25 points. Subresource Integrity not implemented? -50 points etc!
CONCLUSION
To conclude, we need to keep focus on the fact that this is just a snapshot taken from a sample of live sites deployed in the UK to service their local public, and as such that whilst the findings in some cases are slightly encouraging, the majority are of very real concern, as we are global residents in the age of Cyber Toxicity. Such concerns of course are heightened by the fact that the overall profile of threat is realised, and has been notified by global agencies, including our own NCSC, but still, we encounter the lacklustre security profile of exposure.
What I really find irksome is the fact that there is a wide proliferation of Open-Source Tools available which may be used by anyone, from Researchers to Cyber Criminality, State Sponsored Actors, though to bedroom-based Script Kiddies who are looking to spread their wings into the world of, potentiality lucrative cyber-crime. The open question I am left with is, if such tools are available, which they are, then why are Local Authorities and Developers using them to test their own security profile and posture, which upon their own discoveries they can act on to secure their own deployments? – just a question







