Magecart is back, and the operation is more elaborate than we thought, involving physical shipping companies with mules operating in the United States.
Credit card data is a hot commodity in the criminal underworld of the internet—stolen card data is readily available, and used to fund criminal enterprises of all kinds. But scammers, rippers, and carders aren’t the only ones in on the action—the data has to be stolen in the first place.
Typically, when people think of credit card theft, they think of skimming, point-of-sale devices infected with malware, and large-scale data breaches. But actors are utilizing much sneakier and more sophisticated means of collecting credit card data, such as those behind Magecart, a threat we profiled last October, which injects JavaScript code into e-commerce sites running outdated and unpatched versions of shopping cart software from Magento, Powerfront, and OpenCart. By logging consumer keystrokes, Magecart captures large quantities of payment card information from unsuspecting shoppers.
This stolen data can be packaged and sold as CVV dumps, on websites where transactions involving stolen credit card data take place. In a recent Krebs on Security blog post, which ties Magecart infrastructure listed in our original report to a credit card dump website known as “Trump’s Dumps,” we caught a glimpse of how those behind Magecart are monetizing their operations.
But RiskIQ’s follow-on report, Magecart Part II: From Javascript Injects to Reshipping for Financial Gain, shows that these actors actually have a well-diversified portfolio of rackets for making money from their plunder. Continued tracking of Magecart activity over the last few months gave us a rare look into the physical world operations of actors tied to digital threats: cashing-in by reshipping items purchased with stolen cards via a physical reshipping company operating with mules in the U.S.
How we found it
By pivoting on a domain related to known Magecart activity in RiskIQ PassiveTotal, the team found that the server behind its IP address, currently used for the injects of the Magecart script, also links to a domain for a reshipping company website falsely advertised as a freight/logistics provider, USLOGISTICEXPRESS.COM.
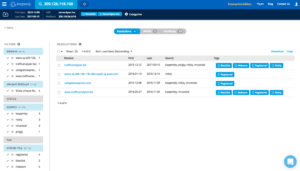
Fig-1 Pivoting on 209.126.118.168 in PassiveTotal
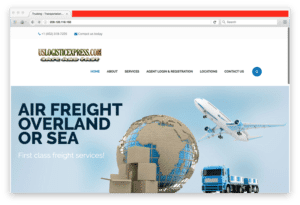
Fig-2 HTTP default virtual host on 209.126.118.168 exposes uslogisticexpress.com
If we look at this fake company name, we can find a registration of it online:
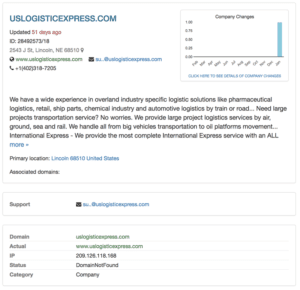
Fig-3 Company profile of “logistics provider” International Express (uslogisticexpress.com)
Via false employment ads on Russian job websites for U.S.-based job seekers, mules are recruited under the pretense of “transport agents,” tasked with receiving shipments of electronics and other goods bought with stolen credit cards to ship to an address in Eastern Europe. This technique is similar to more traditional schemes involving money mules, but rather than a direct transfer of funds, the actors behind Magecart transfer funds into higher priced goods, which can be shipped across borders without suspicion, then sold for a hefty profit.
Below is a very obvious reshipping request for U.S.-based residents to help out as mules. Both of the adverts were put up on websites advertising jobs for U.S. and Russian employees and employers:
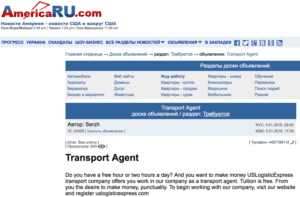
Fig-4 English language job posting for a transport agent on Russian/American news site
Why RiskIQ?
Online stores remain one of the easiest ways to capture payment card data, so we don’t anticipate threats like this to go away anytime soon. A lack of overall protection on many online stores and the level of ease by which criminals may gain access to vulnerable web applications lead to successful fraud operations like Magecart, supporting our belief that attackers are attempting to capitalize on this period before additional safeguards can be enacted in the ecosystem to heavily target online stores.
Because we have an outside-the-firewall perspective, RiskIQ sees what appears on e-commerce websites and mobile sites—just as it appears in users’ browsers. RiskIQ virtual users capture the DOM and find the dynamic links and changes made by JavaScript that could signify a potential attack. Our dynamic inventory system provides full visibility into the state of all the assets for which your organization is responsible.
Download the full report, Magecart Part II: From Javascript Injects to Reshipping for Financial Gain, for a deep dive into:
- The evolution of payment card theft
- Magecart infrastructure: what it looks like, and how to detect it, and how it’s evolving
- Why e-commerce sites and consumers are at risk
- The Magecart operators’ offline rackets and why they work
- Guidance for e-commerce site owners and why having a dynamic view of their digital footprint is key to defending themselves
Visit the Magecart Public Project in RiskIQ PassiveTotal to pivot on IOCs related to this threat.
[su_box title=”About Yonathan Klijnsma” style=”noise” box_color=”#336588″][short_info id=’102864′ desc=”true” all=”false”][/su_box]






