Whilst the conceptual and academic discussions around dangerous forms of code have been on the agenda of decades past, it was in 1983 when the bright young student, Fred Cohen (who I think of as a distant friend) created the first prototype virus, followed in the mid-eighties when the Sunday Times ran a very small article on the dangers of these new computer viruses – a threat in ‘those’ times which was denounced as but a passing nuisance which posed no real dangers to the world of computing. However, what was not considered by that assessment was, society, business and more importantly Governments were moving away from the robust security imposed by the world of Mainframes and Supercomputers and were thus in a state of transition toward the lower-cost, COTS (Commercial-of-the-Shelf), cheaper, more cheerful, and what was certainly more user-friendly technology in the form of the Desktop PC, leading on eventually the interconnected architecture of Client Server environments.
It didn’t take long to realise that the assessment that these new computer viruses were, but a passing nuisance was flawed as the emergence of virial adversity started to appear on a regular basis, with several malicious objects active in the wild such as Elk Cloner (targeting Apple). However, it was the emergence of the first big hitter boot sector viruses to arrive on removable media which changed the opinion of risk, when in 1986 in the form of Boot-Sector infector tagged Brain, the work of brothers Basit and Amjad Farooq Alvi, who ran a computer store in Pakistan. Then quickly followed by mal-agents such as Jerusalem, Ping-Pong, AIDS, Michelangelo, and many, many others. But it was the creativity of the Computer Virus Community which would go on to demonstrate that this new logical danger was more than the, assumed passing nuisance, elevating encompass Macro Viruses and eventually the intelligent crafted code of the Worm – it was time to act.
Below at Fig 1 is a sample set from a database of thousands of viral objects I have collected over the years – giving an example of the patterns of enormous growth over the decades – and as can be seen at Fig 2, still active, and detectable today.




Getting up-to Date – 22022 and beyond
Moving up to the current day of 2022, the very same threats which plagued us back in those early of days of malicious software object are still with us, but in today’s complex environments are now cloaked in a much more challenging guise!
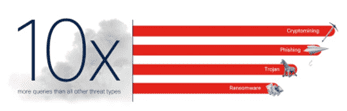
In 2022 the malicious opportunities have gone off the scale, when compared to the early days of malicious objects in circulation – threats ranging from Cryptomining, Ransomware, conjoined with the, what seems to be continuous incursions of Phishing attacks, and the circulation of Trojans – all of which are imposing adverse conditions on our important business, and personal data objects – See Fig 5:
Fig 5 – 2022 Threat Landscape
The Threat Landscape dictates that a solution beyond that of a tactical approach is required, with a robust strategic solution to provision a higher-level of robust defence for data at rest, and data-interaction – exchange on Removable Media.
As anyone who monitors cyber-researches will know, the current level of threats and the ingenious ways in which the attacker finds to infiltrate the local, and networked device security posture are a daily continuation of Active and Persistent Threats (APT) which are only limited by the imagination of the attacking assailant – see Fig 6 for one such example, out of a cast of many:
Fig 6 – active and Persistent Threat
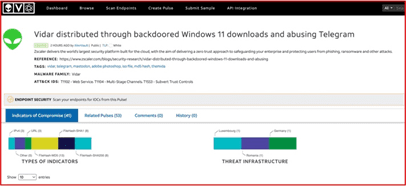
In fact, to understand the level of success the adverse incursion enjoys, you only need to refer to Fig 7 which provides the view ofprima facie insecurity of a big brand, global organisation.
Fig 7 – Successful Incursions on an Industrial Scale
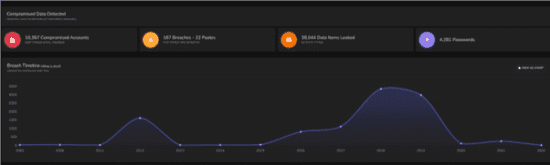
Looking at the output from the BreachAware scrape, here we have a very high-profile company who are situated in the Credit References tier; here we may conclude that they are also the custodians of the data of just about every subscribed UK resident, and beyond. Thus, where we note they have suffered a total of 10,367 security breaches, and have leaked 39,044 data items and objects, it is an assumption that such details (adverse intelligence) will go on to suffer secondary levels of abuse in the hands of their new, unauthorised custodians – here the implication is again, the end target cyber-exposure to abuse rises by a factor of the unknown.
The World of Cyber Security Has Moved On
Granted, the world of Cyber Security and defensive applications has moved on from the old days of malicious objects going into circulation in the wild – yet the levels cyber insecurity have increased, and have now reached a position which may suggest, digital-insecurity is out of control. For example, whilst it is not uncommon to find that the Operating System (O/S) of choice for Corporate, SME, and Government alike is of course Windows, it should be a grave concern that in 2022 at the Pwn2Own Vancouver Hacking Contest, Security Researchers were able to successfully hack this new shiny Flagship of Microsoft, Windows 11 O/S no less than three times using Zero-Day exploits. Here the world of cyber security may be exemplified as has not moving on far enough!
The SME Cyber-Risk-Factor
When looking toward the SME, compared to their larger corporate counterparts, they tend to be obviously lacking in the aspect of disposable budgets to invest in their Cyber Security Posture. Furthermore, with their smaller capacities in the areas of Human Resources and Skills, they are again, clearly behind the curve of their larger corporate communities, and are not thus as well equipped to defend themselves from the almost daily ingress cyber security threats.
SMEs are increasingly moving to e-commerce and digitising their business. Moreover, they are largely dependent on their phones to do business, whether it is sending emails or conducting online transactions, all of which expand their exposure to malware. Again, through what has been assessed as lower-levels of Security Awareness in the SME community, the likelihood of an increased threat posed by the existing potential ease of downloading malware secreted away by innocent-looking apps, emails, or an URL, the average SMEs are very exposed to all forms of cyber-compromise.
SME Managing Director Comment: ‘I don’t have time to over focus on Cyber Security – all my main resource is focused on producing goods, to generate income – I just hope that my small business does not fall to the attention of, what people call hackers’
Possibly, that sentiment is further demonstrated by the results of a CNBCI Survey Monkey survey taken from 2,000 SME, of which only 5% of owners considered cybersecurity to be a big risk (see URL below). However, it needs to be acknowledged that a Cyber Attack can cripple a small business, be that in the form of compromised data, reputational damage, the loss of clients, right down to a state in which recovery is beyond reach – endgame!
https://www.surveymonkey.com/curiosity/cnbc-small-business-q2-2022/
The Travelling User
Travelling Users and Executives are always a potential target. One Achilles heel can be the data that is being carried – maybe on a laptop with a hard drive storing data in open format, protected only by say a Windows User ID and associated password, or maybe on a USB key, or other form of storage. When it comes to physical aspects, such systems may be stored in the aircraft hold, or the overhead locker – and remembering that our user may be using forms of open public WiFi environment – add to this the need to charge their devices from public power charging portals, and the risk of potential insecurity to creep into the traveling experience increases to a commensurate level of multi-factored exposure.
The Corporates, Big Businesses and Others
Within the Corporate sector you would expect to discover more cyber-resilience, yet this is not always the case. To exemplify one such bad example, I look back to the big-name brand who own a chain of public houses (pubs to you and me) and a global coffee shop brand. The Cyber Security Team, from Manager down were aware that there was a dormant Ransomware agent residing on one of their servers, which they chose to ignore for two reasons:
- It was dormant
- The server we tagged for decommissioning, so why waste time?
What was not anticipated was, a wondering browsing user would discover this interesting looking file, and with one click lock down 7 servers in the logical path of the agent, some of which were critical – going on to takeout a POS (Point of Sale) system at a remote site located in the East Midlands (UK), at which point the Ransomware agent then disabled the local Anti-Malware/Virus application, and mailed out the stored user data, including personal and credit card details – again, being sent onto the potential of secondary level abuse.
Part 2 – Secure Operations and Enhancements
In Part 2, with a little creative imagination, we will be considering the methodologies which may be applied to not only secure the data objects from prying eyes and abuse, but will also be considering the application of technology we may already own to secure our precious data-objects from compromise and abuse by APT’s and other forms of dangerous logic such as Ransomware – and look to develop a strategy which may be embed the practice of developed operational robust security practices into the daily lifecycle of securing and protecting our data. It can be done, we just may have to accept a different approach to delivering, what may move one step closer to robust cyber resilience.







