In Part 1 published by Information Security Buzz 25th May 2022, the article considered aspects of historic threats posed by all forms of malevolence in the form logical, digital compromise, and looked back to the past encountered threats resulting from Malware and other more costly situations, such as the loss of Crypto Currency through some form of crafted attack; or maybe even by a Ransomware agent denying access to owned data. In Part 2, we will consider some other exemplified real-life attacks which led to compromise and the exposure of sensitive data-assets, and will seek to provision pragmatic, common-sense direction as to how mitigations may be applied to enhance the defensive cyber-posture.
2022 and beyond
Prior to getting into the devil of detail, let us remind ourselves what the future of Cyber Security may (will) hold for all users, be they Individuals, Corporates, Academic Institutions, Governments (both Central and Local) and of course Charitable Agencies – AKA, anyone who uses an IT asset to process data!
There are several lurking dangers which we need to appreciate and understand, the first of which is the threat posed by China who are a known known global digital adversary engaged in on-mass hacking and globalised levels of digital industrial espionage programs against any target, in particular the West, APAC and of course Taiwan. The second big hitter spills out of the Russian Invasion of Ukraine which, no matter the longer-term kinetic outcome, will result in an increased level of global digitised tensions and exploits targeting anything and everything to drive the Russian Mission. And of course, not forgetting all other State Sponsored Actors such as North Korea, and the everyday criminals looking to make a fast buck, say by employing Ransomware or other forms of evil logical mechanisms. So, in a nutshell of predictability, things are going to get potentially worse until they get better – so time to batten down the logical hatches and to enhance the Digital Security Posture. However, if more evidence is required, please see URL relating to Russian Cyber Attack’s:
Russian Cyber Warfare 2022
The Corporates World
As a reflection on a real-life example case – I recall when holding the position of Head of Operational Security for a large East Midlands based company. Whilst the CISO and I were out of office travelling internationally, the organisation was hit by a zero-day virus. To counter the threat, an anti-virus patch was required to be pushed out to around 10,000 endpoints. However, the permissions applied to the target machines would not facilitate that logical approach to be taken. In the convened Major Incident Review (MIR) meeting, it was decided between the Director of Change Management, and the stand in Junior Security representative, the permissions would be downgraded on the Domain Controller to allow every system to be enabled to FULL Read-Write permissions in order to deploy said patch, after which time the permissions would be reinstated – and that action was applied. All was well, until reports started flying into the Service Support Desk that any user could see any users’ local drives – in particular, the sensitive data resident of the Main Board Level HR Directors PC, who maintained his personal archives locally to assure a higher level of control. What had not been considered in the decision process was, whilst the permission could be downgraded and cascaded across the entire Domain, to revert the permissions back to a secure-state required a reboot! Thus, manifesting in a misguided action which created one of the biggest, self-inflicted events of insecurity the organisation had ever suffered.
Mitigation 1: Security Awareness and Skills: It is essential that those involved in the Cyber Security Tier have the anticipated, prerequisite skills and knowledge to fulfil their professional obligations.
Mitigation 2: Data Security: In this instance there was a strong case for the HR Director for storing data off-system on secure, encrypted removable media. This would have underpinned the expectation of security and privacy and would also have avoid any other potential logical attacks against the stored data objects – more on this later.
Fixed Non-Encrypted Drives
So, say you are using a laptop, upon which you store your every-day, and sensitive files – maybe work related, maybe personal. And you do so with the confidence that your data is safely tucked away, and secured by the system User Account and associated ultra-secure, complex Password – but think again, the easiest way to bypass such access controls to the on-disk secure data is to simply remove the target drive, then mount directly onto a PC, or in the case, as shown at Fig 1, imported to my iMac:
Fig 1 – Direct Access to Data (Information)
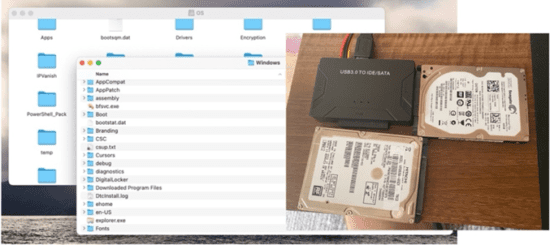
Here, the strong case for encrypting everything certainty does stand true!
Fixed Onboard Encrypted Drives
When working with Central Government Agency who processed high classification, Secret, Codeword data, to accommodate the required level of stipulated security safeguard Protectively Marked Data Assets, the department installed Flagstone Encrypted Drives – see Fig 2. However, whilst in essence secure, there are also several limitations when taking this approach. Which are as follows:
- Once the user is authenticated, the drive will always be mounted – this presents an exposure of data corruption by logical attack (again, more on this are of insecurity later).
- Data is stored on a single asset, thus is less flexible to collaboration across other platforms.
Fig 2 – Flagstone Internal Drive

Mitigation 3: Use Secure Removable Media: The proposed mitigation is to employ FIPS-140/2/3. This approach will enable more flexibility when using data assets between systems, agnostic to O/S, as well as securing the on-board data assets against attacks on the actual computer platform
FIPS-140/3
https://csrc.nist.gov/publications/detail/fips/140/3/final
FIPS-140/2/3 Secure Encrypted Drives
https://istorage-uk.com/product-category/encrypted-hdds-ssds/
Digital Attacks
We are now very aware of the circulated, ever-persistent threats posed by malicious objects in the form of Malware, Illicit Crypto Theft/Transfers, and Ransomware attacks which may arrive by email, over insecure connections, or via some other form of media interchange by an infected object.
For example, consider the overnight, potential theft of more than US$326 million (A$457.7 million) of Ethereum tokens from a cryptocurrency blockchain bridge; or theft from a Bitcoin users personal Wallet in the UAE – suspected to have been carried out by an intermediary Third Party. In another such attack, BitMart identified a large-scale security breach, resulting in the theft of approximately US$150 million (A$210.6 million) in crypto assets from Hot Wallets*.
*Hot Wallet: Because they store crypto online, they carry the increased risk of being hacked.
Mitigation 4: Store Crypto in Cold Wallets on Secure Removable Media
Below are the fundamentals of securing your Crypto Assets against compromise:
- Use a Cold Wallet: The security of a Cold Wallet is only as good as the way it is used (kept Cold)– thus, always ensure that the internet is disconnected (not forgetting WiFi) before attaching the Removable Media containing the Cold Wallet.
- Dedicate the use of the Removable Media to only the Cold Wallet – consider this your Bank Vault.
- Ensure your Crypto Wallet is maintained up to date.
- Create multiple backups of your crypto keys and wallets and store them in separate, secure locations – again, another reason why Removable Media is the best option.
- Use dedicated passwords/pins which are only associated with the Cold Wallet device – never reuse passwords/pins.
- Never expose your USB wallet to any public computer, or untrusted system.
- Use a FIPS-140/2/3 encrypted removable drive for additional security – secured by a pin between 9 and 15 numeric selections.
- Maintain a regular cross-device Backup Strategy.
The SME Cyber-Risk-Factor
As introduced in Part 1, it is the SME who represents the greatest number of targets, and thus are at daily risk of serious cyber exposure or compromise – reason being, they are usually weaker around their Cyber Security Posture, and of course tend not to have a robust accommodation of Cyber Security Skill sets, as one would expect to find in the corporate world. To evaluate the level of exposures (or not) related to a sample of SME’s located in the Nottingham area of the UK, 20 companies were selected at random, and their known security posture was submitted to discovery, again using the BreachAware platform – and the discoveries were telling. Overall, the average breaches associated with the sample ranged from 2 to 112, with data leakages averaging from single numbers up to 431 in one case. However, what was even more enlightening was, the companies carrying the most adverse security posture, were those located within the IT world of delivering solutions and consultancy. See Fig and Fig 4 below for two examples of SME insecurity.
Fig 3 – SME 1
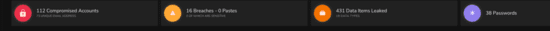
Fig 4 – SME 2
Granted, these are minor when compared to their lager corporate traders – but remember these are samples of SME’s with between 5 and 200 users, so by comparison, based on number these discoveries may be considered high.
Mitigation 5: Apply a Secure Posture
All SME’s who feel they may be exposed to Cyber Threats (and take it from me, they are all in such a position) – have a read of this article and start to evolve and enhance their cyber security posture of business, with a few easy to implement steps.
The Cyber Security Industry
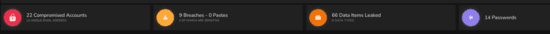
As we were reviewing the areas of Cyber Security Postures, out of curiosity, several on-line assessments were conducted of companies who provision Cyber Security Support Services and Consultancy, and whilst most stood up well to the evaluation, one stood out amongst their equals with a damming discovery – see Fig 5 below:
Fig 5 – The Security Posture of a Third-Party Security Provider

Note 1: The number of compromised accounts, breaches, data leaks and password security issues appear to be excessive, and thus may be related to the wide range of interconnected clints to whom they provision a service – again, we may further understand with this example the true implications of the Third-Party Risk.
Ransomware and On-Line Threats
We are aware of the everyday dangers of the multiples of Ransomware agents in the wild, which have the potential to deny access to data by either locking down the entire platform, or by locking down the actual on-board data by encryption. In my own experience, particularly when on international travels, this is the very worst-case scenario. Given, I am not particularly bothered about the actual platform O/S which can be replaced, or even the physical device which can again be quickly replaced at the swipe of a credit card– it is access to the stored data I require. Yes, granted, I could have this backed up on cloud, and I do. However, with the size of data assets, whilst I could wait for the downloaded to complete, I simply do not have the time to waste when dealing with multiple clients. Here I employ a long time, tried, and tested, just-in-case mitigation which provides a very robust solution against the anticipated threat.
Mitigation 6: Read-Only, Secure Removable Drives
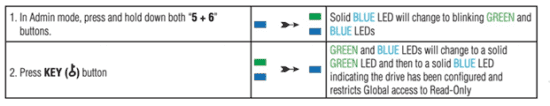
To protect valuable stored data, I always carry all my most up-to-date files on my M2 Encrypted Removable Drive, which satisfies both security and privacy, and meets the expectations of GDPR etc. However, I then go one step further, by enabling the loaded drive in Read-Only mode by applying the configuration as shown at Fig 6, which then, no matter the form of adverse logic which may attack my system, I have the assurance that my data is protected.
Fig 6 – Drive Set to Read-Only
Note 2: Watching a TV programme about Heathrow Airport this week, the topic of lost property was covered. One case was introduced which took my interest – the loss of a Cardiologist Laptop containing years of research data which had been left on an aircraft. Fortunately for the surgeon it was located and recovered. However, when you consider the potential loss of such valuable life’s work, of what may be irreplaceable data, it does tend to focus one’s mind.
Public WiFi
When on my travels, I like many other people often have need to utilise Public WiFi Hot Spots – on trains, in hotels, on aircraft, at the airport etc – you get the picture. However, I am equally aware of the levels of insecurity which may be associated with these open devices – so there is the ever-present danger that data is open to compromise or abuse.
As an real-world example, when attending a Cyber Security Conference at a Hotel situated in Marble Arch, London, my attention was drawn to some interesting looking areas, which implied that insecurity was close at hand – so, I decided to run an Audit against the Hotel Access Point, and the discoveries were alarming to say the least – See Fig 7 – a prime example of what is referred to as a Dark Hotel. This image represents only a part of the 32-page output of discovered insecurities, potentially exposing every user and hotel guest who connect though the AP – note some of the trojan applications which are associated such as Back Orifice:
Fig 7 – Dark Hotel Insecure Public WiFi Access Point

Note 3: It should also be appreciated that, depending on the attached end-point configuration, it can be possible over an insecure AP to access, view, copy, or change on target system data objects by use of an RDC client.
Mitigation 7: VPN
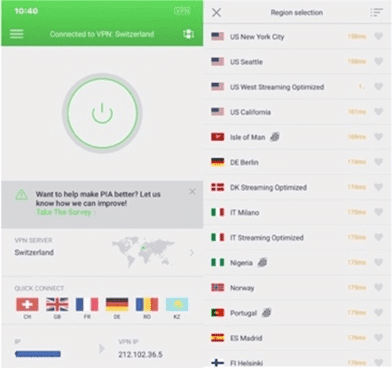
A very easy security fix to apply here – do as I do, and always utilise a quality VPN to secure the tunnel to encapsulate the session and any transactions – See my VPN at Fig 8.
Fig 8 – My VPN
Public Charging Points
When I (we) are on our travels, the need to reenergise our mobile assets can crop up on regular occasions – in the UK or International Airports, In-Air/Flight, or in a Public Place. The temptation to utilise one of those locker power point hubs, or other available facilities can thus become very tempting to keep our assets operational. However, these unknowns are also ideal portals to channel or infiltrate the connected device, and possibly load over a little more than just a battery top up.
Mitigation 8: My Best Practice
My own approach is to employ the blocking capabilities of the USB token at Fig 9. This is the PortaPow Data Blocker, allows the electrical circuit to interface with the connected device, and to deliver a charge, whilst blocking all other forms connectivity – a bit like Write Blocker.

Conclusion
In 2022, it may be sadly concluded that, no matter the entity, be it an individual, SME, Corporate, Government Agency, or any other user profile who have an online presence, or some form of Digital Footprint, they represent fair-game for cyber criminals, or any other actor in the guise of an online hostile.
With the backdrop of the risk, nevertheless, we may still encounter those who engage with the online world with a laissez faire attitude toward the dangers they are exposed to – dangers which will only increase year-on-year. By also adopting such a carefree approach to risk, they are also acting as subliminal agents of the criminal and hacker communities, as such carelessness also provisions the potential for an onward conduit into any other online or connected associates.
What I have attempted to tease out in Part 2 are some examples of the daily risks we may (and do) encounter and have attempted to open the conversation that, cyber security is achievable for all to evolve a more robust cyber security posture is in the reach at zero, or minimal cost. Hopefully, some readers who fall into the category of hosting exposure will rethink their approach and move forward into 2022 and beyond in a much-enhanced profile of Digital Hygiene. The opposite option of course is through caution to the wind and run with the exposed risk of compromise – the decision, as the game shows says, is ‘yours’.







