Proofpoint threat analysts have been tracking and analyzing the malicious macro attachment campaigns that have dominated the threat landscape. Through their continued evolutions, these campaigns nonetheless primarily targeted organizations in North America, and more specifically the United States. In a recent [1] post we described how known Dridex actors appeared to be shifting their targets to Europe, with the example of a campaign targeting Poland. At the time, Proofpoint researchers also detected a sudden, massive increase in activity targeting French organizations and warned that this could be the beginning of a sustained attack.
Additional monitoring and analysis have confirmed that this was indeed the case: after two weeks of sustained attacks, threat actors continue to target French organizations with more sophisticated later iterations of these malicious macro attachment campaigns, including the actors behind the prolific Dridex botnet #120, one of the earliest actors Proofpoint researchers analyzed in these campaigns. These campaigns are striking because they include many of the latest adaptations that were added over the course of months to US-targeted campaigns; as a result French organizations that have had little exposure to these threats are now facing their most sophisticated and effective versions, and the results can be seen in the high infection rates.
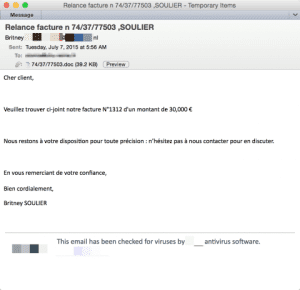
The campaigns feature a variety of lures, with the Dridex 120 actor using a straightforward “invoice template.”
 The messages are mostly text, with generally correct spelling and grammar. These messages are generated from a message template that is sent to a sending bot, similar to the example below from an English-language Dridex campaign.
The messages are mostly text, with generally correct spelling and grammar. These messages are generated from a message template that is sent to a sending bot, similar to the example below from an English-language Dridex campaign.
 Each message carries an attachment and the names are randomized (for example, “12/34/5678.doc” and “48_58_97830.doc”), with very high volumes of unique documents attachments resulting in a large number of hashes to distribute across the campaign, thus improving resistance to antivirus detection.
Each message carries an attachment and the names are randomized (for example, “12/34/5678.doc” and “48_58_97830.doc”), with very high volumes of unique documents attachments resulting in a large number of hashes to distribute across the campaign, thus improving resistance to antivirus detection.
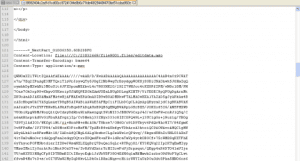
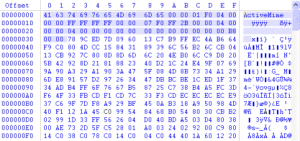
Like the campaign targeting Poland, this campaign employs a relatively recent innovation [2 and 3] in these malicious macro attachments, which is to create the Microsoft Word attachment as a MIME-formatted file that contains base64-encoded ActiveMime, which in turn contains a zlib-compressed Word file. It is the compressed Word document that carries the malicious macro code [4]. (Figs. 4-6) This technique causes the attachment to appear as a normal “DOC” file to the end-user while resisting analysis by automated tools that do not include the ability to read the MIME content. When the end-user opens the file it presents to the end user the Enable Content button that we have seen so much of late.
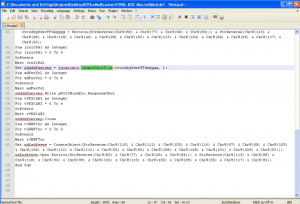 When the end-user opens the file it presents the Enable Content button that we have seen so frequently of late. Clicking the Enable Content button runs a macro that in turn downloads a VBScript from Pastebin. This is another relatively recent innovation, as attackers store more pieces of their code on remote servers for download during the infection process in order to improve evasion of string-matching defenses. Upon execution the VBScript then downloads the Dridex 120 payload.
When the end-user opens the file it presents the Enable Content button that we have seen so frequently of late. Clicking the Enable Content button runs a macro that in turn downloads a VBScript from Pastebin. This is another relatively recent innovation, as attackers store more pieces of their code on remote servers for download during the infection process in order to improve evasion of string-matching defenses. Upon execution the VBScript then downloads the Dridex 120 payload.
The primary function of the Dridex banking Trojan is to capture login credentials for online banking and other web accounts, and an extracted configuration of this Dridex shows that it has been tailored to target customers of three of the top-five French banks. Dridex also has the ability to download additional malware, creating the potential for further losses of data and misuse of the infected client.
This combination of techniques continues to yield dividends to the Dridex 120 actors, as infections for 1 July 2015 showed French systems again far outnumbering other countries: more than 13 times the total of the next ten top infected countries, and this for a single actor. This ratio has been relatively consistent since Proofpoint first began tracking this French campaign on 22 June, and actors will continue to aggressively target French organizations until they adopt the defensive solutions and strategies that initially drove attackers to shift their targets abroad.
To learn more about the new generation of malicious macros and how to combat them, read the recent Proofpoint research paper, “The Cybercrime Economics of Malicious Macros.”[su_box title=”About Proofpoint” style=”noise” box_color=”#336588″] Proofpoint Inc. (NASDAQ:PFPT) is a leading security-as-a-service provider that focuses on cloud-based solutions for threat protection, compliance, archiving & governance, and secure communications. Organizations around the world depend on Proofpoint’s expertise, patented technologies and on-demand delivery system to protect against phishing, malware and spam, safeguard privacy, encrypt sensitive information, and archive and govern messages and critical enterprise information.[/su_box]
Proofpoint Inc. (NASDAQ:PFPT) is a leading security-as-a-service provider that focuses on cloud-based solutions for threat protection, compliance, archiving & governance, and secure communications. Organizations around the world depend on Proofpoint’s expertise, patented technologies and on-demand delivery system to protect against phishing, malware and spam, safeguard privacy, encrypt sensitive information, and archive and govern messages and critical enterprise information.[/su_box]