As hard as it may be to accept, in 2014 there is an estimated 17,000 global financial crimes being committed every second, and when you assess the related impact on individuals, companies, and economies the sum calculates to a significant, and probably, what actually is an unknown number – but as Willie Sutton responded when asked why he robbed banks, his simple and eloquent answer was ‘Because that’s where the money is’. In our modern day of cyber-interconnection age of dependencies, I guess if you ask those engaged in CyberCrime why they do it, one should expect the same answer.
Today we are seeing a massive onslaught against Internet connected endpoints, be they personal, government, or commercial systems, they all offer the same profile to the ever-present attacker, with three potential surfaces of attack, which are:
1) They are connected to the Internet [Opportunity]
2) That they are being used by humans [Sociability]
3) They are running software [Exploitability]
It may be that all of these ducks are not always lined-up of course, but if you consider the huge number of connected targets the opportunities are massive. To quantify the potential exploitation factor, take a campaign involving the communication of 50,000 Malware, or Trojan carrying Spam’s targeting scattered end-points. The expected success rate here is around the 0.4% mark, representing just 200 machines – not many I agree. However, one of the earliest scams ran in 2004 in the early days of criminal-evolution netted $125 million. Now when that success rate is extrapolated into today’s sophisticated cyber-criminal activities, and aligned with the growth, and dependency on the internet, and computers, you may soon appreciate the rich pickings and the potential revenue-streams of illicit money – it is huge.
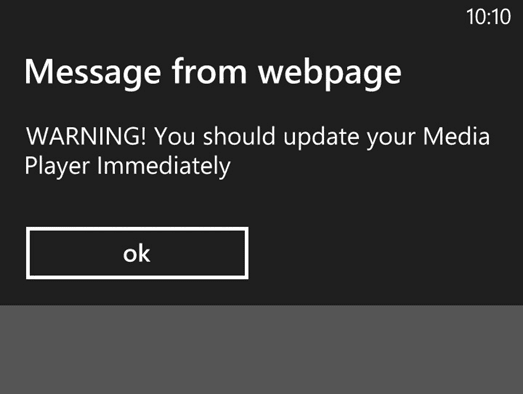
Now having set that past scene, to come right up-to-date I would like to share with you some results out of a mini Research Project I ran in March 2014. The initiator to this research was when using my Smart Phone’s small screen at the end of a long working day. The small surface of operation, linked to my comparative oversized digits, and the fact I was tired manifested in a number of frustrating mistypes, which meant I was either not loading a page to my mini-screen, or I was going to the wrong location – then a thought from the past, and my imagination started to run! What if I take a very well known, everyday URL, and drop the first character from the domain name, what would I find today? Bingo. The results on my Smart Phone were to present a black screen, with the notification warning that my media player required updating [right!], and gave the option of an ‘OK’ button to proceed [See Fig 1]. However, it was not possible to go back, forward, or to drop this screen – it was loaded, and staying there – my only exit option was to do hard-reset. I then attempted this same load three more times, and on each occasion it amounted to the same, with the requirement of a hard reset to get out of the logical trap. However it never stopped there as I also discovered that, taking into account the keyboard positioning of characters of this particular well-known domain name, a slip of the hand, hitting ‘ii’ instead of ‘oo’ internal to the URL results in the same, or similar misdirection – all angles covered as they say.
Fig 1.
The next step was to move over to a PC, and here through the more secure Aviator Browser, I ran some lookups on these convoluted domain names, and was surprised to see that every instance of popular extension was taken – registered in various parts of the world, by various users, one of whom clearly recognized the illicit potential value of this nonsensical domain name, and was offering it up for sale.
OK, so now it was time to move to the next stage of offering up a PC as a sacrificial lamb, and so the page was loaded – a white blank screen appeared, and some ‘other’ domain was called by our convoluted fake, and that was it – again nothing. However, after dropping the page it was soon evident that the purpose of the load had been to deposit its logical payload in the form of Malware on my fully patched, AV protected system – as they say, I had been compromised.
This type of subliminal attack is nothing new of course. However, with an increased vector of threat born out of the modern-age cyber payload, such a misdirection’s could manifest with any one of many invasions being communicated, ranging from compromising the local PC, to stealing sensitive credentials – old world meet new, but with a much greater opportunity of adverse impact.
This however did remind me of another past campaign which was run against a number of Experian users around 9 years ago, then in the form of the Tasmanian Devil-attack. This attack sent the user a URL, which upon load would place an animated image of Mr. T. Devil himself on screen, and that was it – nothing. However, when one delved into the simple code of the attacking-page, it could be seen that it’s mission was to probe the local system to ascertain what the level of patch which was in place in order to perfume a targeted exploit – it was successful in a number of instances, and all born out of associated harvested, and targeted email which were connection with a well-known on-line credit checking system.
As a conclusion, as with the London Olympic Games who suffered from large numbers of attacks, and some successful exploitations, thus, with the benefit of knowledge we should realize that where we see other such profiled events taking place there should be an expectation that Cyber Criminality will be involved, and will be planning their attacks. Maybe by setting up of domain names which the organization has overlooked which are reflective of the event, or one which relies on the simple matter of a user mistyping the URL, to take them to an unsafe and exploitable place. As we have now come to accept, the hit rates do not have to be high, but the rich pickings can be massive, and the path to exploitation can be very low cost and very simple – so take care, and remember, Situational Awareness is more than a phrase, it’s a Condition.
[su_box title=”About Professor John Walker – FMFSoc FBCS FRSA CITP CISM CRISC ITPC
” style=”noise” box_color=”#336588″]
 Visiting Professor at the School of Science and Technology at Nottingham Trent University (NTU), Visiting Professor/Lecturer at the University of Slavonia [to 2015], Independent Consultant, Practicing Expert Witness, ENISA CEI Listed Expert, Editorial Member of the Cyber Security Research Institute (CRSI), Fellow of the British Computer Society (BCS), Fellow of the Royal Society of the Arts (RSA), Board Advisor to the Digital Trust, Writer for SC Magazine UK, Originator of DarkWeb Threat Intelligence, CSIRT, Attack Remediation and Cyber Training Service/Platform, Accreditation Assessor and Academic Practitioner and Accredited Advisor to the Chartered Society of Forensic Sciences in the area of Digital/Cyber Forensics.
Visiting Professor at the School of Science and Technology at Nottingham Trent University (NTU), Visiting Professor/Lecturer at the University of Slavonia [to 2015], Independent Consultant, Practicing Expert Witness, ENISA CEI Listed Expert, Editorial Member of the Cyber Security Research Institute (CRSI), Fellow of the British Computer Society (BCS), Fellow of the Royal Society of the Arts (RSA), Board Advisor to the Digital Trust, Writer for SC Magazine UK, Originator of DarkWeb Threat Intelligence, CSIRT, Attack Remediation and Cyber Training Service/Platform, Accreditation Assessor and Academic Practitioner and Accredited Advisor to the Chartered Society of Forensic Sciences in the area of Digital/Cyber Forensics.
Twitter: @SBLTD
John Walker is also our Panel member. To find out more about our panel members visit the biographies page.[/su_box]







