A new study finds that only one third of businesses require MFA access, have separate staff /guest WI-FI or use VPNs for remote workers. The UK government released their Cyber Security Breaches Survey 2022 this week reporting that only around third of organizations follow any of these practices, with the percentage being only slightly higher for businesses vs charity organizations. The report goes on:
“Two-factor authentication was covered for the first time in this year’s survey. Just over a third of businesses (37%) and just under a third of charities (31%), have a requirement for their people to use two-factor authentication when accessing their network, or for applications they use. … Two-factor authentication is noticeably more prevalent among businesses in information and communications (63%). Conversely, fewer than one in five (18%) businesses operating within the food and hospitality sector employ two-factor authentication procedures. It is also relatively under deployed among utilities, production, and manufacturing businesses (28%).”
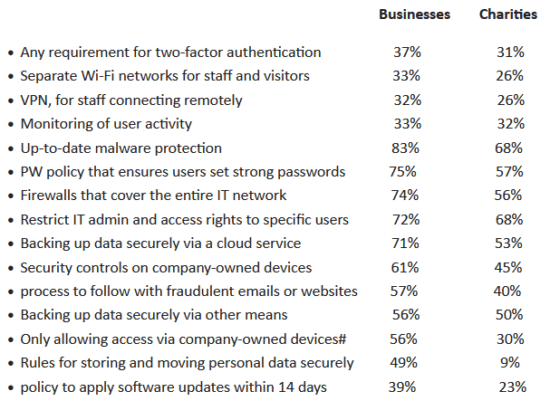
Percentage of organizations that have the following rules or controls in place
The Cyber Security Breaches Survey is an influential research study for UK cyber resilience, aligning with the National Cyber Strategy. It is primarily used to inform government policy on cyber security, making the UK cyber space a secure place to do business. The study explores the policies, processes, and approaches to cyber security for businesses, charities, and educational institutions. It also considers the different cyber attacks these organizations face, as well as how these organizations are impacted and respond.
The Cyber Security Breaches Survey is an influential research study for UK cyber resilience, aligning with the National Cyber Strategy. It is primarily used to inform government policy on cyber security, making the UK cyber space a secure place to do business. The study explores the policies, processes, and approaches to cyber security for businesses, charities, and educational institutions. It also considers the different cyber attacks these organizations face, as well as how these organizations are impacted and respond.







Of the 39% of UK businesses who identified an attack, the most common threat vector was phishing attempts (83%). The main goal of a phishing attack is to access the user’s credentials, that is mainly their password. Besides 37% are using two-factor authentication, the level of security depends on what that second factor is. As when it is an OTP via SMS or a link via email for example, these are not secure enough and could be under man in the middle attack vectors.
Authentication is crucial for everything in our digital life, we cannot rely anymore password shortcomings related not only to security but also usability, productivity, and compliance. Enterprises need to put in place robust MFA, phishing-resistant second factors. Passwordless authentication is the foundational step to eradicate most of these attacks.
MFA, while crucial for preventing credential theft and mitigating unauthorized access, can be met with business resistance as many MFA solutions tend to increase user friction. Organizations should consider implementing a zero trust strategy while also bolstering and modernizing existing VPN environments as both support different use cases for improving workspace security.
MFA solutions need to also be implemented along with endpoint device posture checking and in conjunction with the concept of least privilege to truly drive a zero trust posture. Finally, some modern VPNs have capabilities like multi-pathing and managed attribution which can enhance security by making users and network resources virtually invisible and hard to target by threat actors in the first place.