Not even one month after Incapsula announced our new DNS and infrastructure protection services, our new ’Behemoth‘ scrubbers were put to the test – mitigating a massive, multi-vector DDoS attack, peaking at 110+ Gbps and 90+ million packets per second.
Like the proud parents we are, we couldn’t help but brag about our success on Facebook and Twitter. Our story caught the attention of Mohit Kumar, founder and editor-in-chief of The Hacker News (THN), who shot us an email with some questions. In response we told him it appeared the attack “wasn’t going to stop any time soon”.
FREE ebook: What Is The Security Industry´s Dirty Little Secret
In retrospect, this turned out to be a serious understatement.
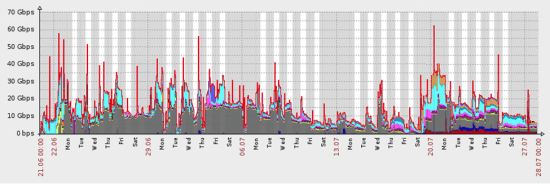 DDoS traffic generated by DNS and SYN floods over the course of the attack.
DDoS traffic generated by DNS and SYN floods over the course of the attack.
The DDoS attack continued to rumble on days after the story appeared in THN magazine. Its presence became a regular fixture of our daily routine to the point where we started second-guessing traffic reports which didn’t include a few tens of millions of filtered-out DDoS packets.
During this time we saw the offenders throwing everything they had at us. They tried everything from massive network layer DDoS attacks to focused application layer (HTTP) floods, followed by dozens of SQLI and XSS attempts – all foiled by Incapsula’s Web Application Firewall.
Typically, the perpetrators were simultaneously using at least two of these attack vectors. It was not uncommon to see them turning up the heat with “all guns blazing” five-vector attacks.
At all times, they continued to use extremely large DNS floods, usually comprising several tens of millions requests per second. Often these were accompanied by large SYN floods, also aimed at Incapsula DNS infrastructure.
It should be noted that, in the last few months, we have mitigated many more of these massive DNS floods, which are quickly becoming the new weapon of choice for DDoS offenders.
38 Days and 50 Petabits of DDoS
The DDoS attack lasted 38 days, during which Incapsula’s scrubbing servers filtered out 50+ petabits (51,000+ terabits) of malicious traffic.
Interestingly, while the offenders did switch between several targets, they consistently targeted the websites of one Incapsula client – a video game company that onboarded Incapsula services on the eve of the attack.
Clearly, this organization was the real target. Combined with the extreme determination of the attackers, one can surmise that the DDoS attack was the result of a business feud. The goal: nothing short of a complete takedown of this online business.
Pareto’s Law – 80% of DDoS Traffic From 20% IPs
The ‘business feud’ theory is reinforced by the resources used during the attack. Looking at source IP data, Incapsula noticed the majority of malicious packets were originating from the same IP ranges. We knew that 20% of C-classes are typically responsible for ~80% of all DDoS traffic.
In other words, we detected offenders who had continuous access to several very powerful network resources. These were strong and reliable enough to sustain a month-long offensive—while also generating 90+ Gbps of unamplified DDoS traffic.
This is a long way off from what you would expect from an off-the-shelf botnet for hire. The perpetrators weren’t script kiddies looking to make a quick buck with a 20 Gbps DDoS attack and a $300 ransom note.
Whoever they were, they were DDoSing for a living.
Just In Time for Graduation
As previously mentioned, the attack started shortly after Incapsula rolled out our new ‘Behemoth’ scrubbing servers. While these new mega-scrubbers were deployed after a month of internal tests, this DDoS event was their true “rite of passage”.
During the weeks of the attack, an observer only had to look at the satisfied smiles of Incapsula’s team to see that we couldn’t have asked for a better final exam.
About Incapsula
 Incapsula’s cloud-based Application Delivery service enables businesses to simplify their IT operations and reduce costs by consolidating multiple appliances and services into a single cloud solution. Enterprises get best-of-breed security, load balancing, failover and a global CDN, without having to deploy, manage and integrate separate products.
Incapsula’s cloud-based Application Delivery service enables businesses to simplify their IT operations and reduce costs by consolidating multiple appliances and services into a single cloud solution. Enterprises get best-of-breed security, load balancing, failover and a global CDN, without having to deploy, manage and integrate separate products.






