Last week, DOSarrest had a run in with the notorious Brobot Botnet. If the name sounds familiar, it’s because this bot was responsible for sporadic outages on a number of large US based financial institutions in 2013. It is said to be operated by al-Qassam Cyber Fighters (AKA QCF).
Botnets are born, die, grow, shrink, and morph on a daily, if not hourly, basis and it is extremely hard to keep track of them all. There are particularly nasty ones that are large, powerful and sophisticated. To keep track of them, they will have some of their zombies or bots corralled off for research purposes by a number of organizations, including private Botnet hunters, government cyber surveillance departments and other large law enforcement agencies.
The attack
A large media outlet specializing in Middle Eastern news was attacked last week.
With all the conflict over there these days, it is suspected that it has written a few stories that the attackers were not in agreement with.
Using Brobot, the attackers threw millions of TCP port 80 requests at the website.
Unlike a SYN attack that tries to exhaust the TCP open sessions table buffers, this attack would open and close each session/request:
1) Request a TCP connection
2) Once established they would send one character
3) Then request the TCP session to close.
The major problem arose when they started receiving approximately 50 million of these per second.
This botnet is comprised of infected webservers using PHP, hosted on various webhosting companies around the globe.
One notable observation of the Brobot is that it’s US centric; while not all of the bots are based in the US, approximately 40% are, which makes filtering based on countries very difficult.
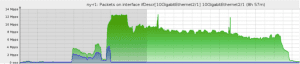
When under a large TCP port 80 attack, it usually is not evenly divided across DOSarrest’s scrubbing nodes in the US and Europe. This attack was different; virtually all of the upstream links in every city had pretty much the same amount of Packets Per Second and Bandwidth. This is extremely unusual.
All links appeared almost exactly like the graph above
The upshot
DOSarrest was able to successfully defend against this attack and within a couple of hours of the attack starting it was contacted by a private Botnet hunter that knew the company was dealing with Brobot. This was soon followed by visits to the DOSarrest website from two US federal Law enforcement agencies. This proves for certain that not all botnets are equal, as not all of them would attract this much attention.
By Mark Teolis, General Manager for DOSarrest
About DOSarrest
DOSarrest is the result of seven years of research, experimentation and mitigation of malicious traffic. In the last seven years, we have formed a dedicated team of network security specialists, network engineers and developers focused on mitigating DoS/DDoS attacks. Solving the DDoS problem is like a never ending cat and mouse game with attackers.
– See more at: http://www.dosarrest.com/company/#sthash.FgPkMnVJ.dpuf
DOSarrest is the result of seven years of research, experimentation and mitigation of malicious traffic. In the last seven years, we have formed a dedicated team of network security specialists, network engineers and developers focused on mitigating DoS/DDoS attacks. Solving the DDoS problem is like a never ending cat and mouse game with attackers.
– See more at: http://www.dosarrest.com/company/#sthash.FgPkMnVJ.dpuf
 DOSarrest is a true, cloud-based fully managed DDoS protection service specializing in DDoS Protection. Its layered protection strategy evaluates complex attacks on a request-by-request basis, so there is never a false positive. Also, its proprietary mitigation methods and techniques have successfully and instantly stopped thousands of real-world DDoS attacks since 2007.
DOSarrest is a true, cloud-based fully managed DDoS protection service specializing in DDoS Protection. Its layered protection strategy evaluates complex attacks on a request-by-request basis, so there is never a false positive. Also, its proprietary mitigation methods and techniques have successfully and instantly stopped thousands of real-world DDoS attacks since 2007.
DOSarrest is the result of seven years of research, experimentation and mitigation of malicious traffic. In the last seven years, we have formed a dedicated team of network security specialists, network engineers and developers focused on mitigating DoS/DDoS attacks. Solving the DDoS problem is like a never ending cat and mouse game with attackers.
– See more at: http://www.dosarrest.com/company/#sthash.FgPkMnVJ.dpuf