 PhishMe has issued details of a malicious phishing campaign currently circulating, with an XORed payload that is capable of grabbing a ton of credentials, mostly FTP.
PhishMe has issued details of a malicious phishing campaign currently circulating, with an XORed payload that is capable of grabbing a ton of credentials, mostly FTP.
Ronnie Tokazowski, PhishMe’s senior researcher, explains, ” When reversing malware samples, one of the things that we as analysts look for are places where the attackers slip up. This can be anywhere from using the same strings, to weak obfuscation routines, or re-using the same snippet of code. When we talk about the attackers, there is this misconception that they are these super villains who can only do evil, but keep in mind they are humans too. Yesterday, we came across an interesting phishing email that contained the following attachment.”
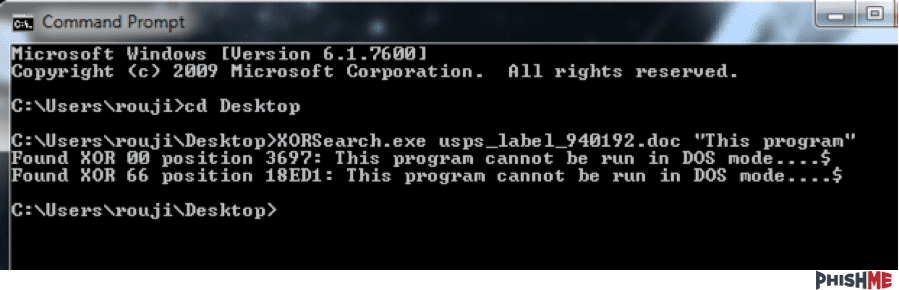
 Ronnie continues ” While we’ve seen tons of word documents that contain macros, it’s typically more rare to see this triggering in conjunction with XOR exe’s. These types of payloads are usually used in conjunction with an exploit and later unpacked. By using xorsearch, we can confirm that there is a malicious payload inside.”
Ronnie continues ” While we’ve seen tons of word documents that contain macros, it’s typically more rare to see this triggering in conjunction with XOR exe’s. These types of payloads are usually used in conjunction with an exploit and later unpacked. By using xorsearch, we can confirm that there is a malicious payload inside.”
 “Once the macro code executes, a copy of the word document will be saved to %temp%/300.rtf and %temp$/301.rtf, our malicious payload will be saved to %temp%/q2.exe, then executed. When looking at q2.exe, we can see the compile path of ‘T:\mandatory\Hence\one\Date\
“Once the macro code executes, a copy of the word document will be saved to %temp%/300.rtf and %temp$/301.rtf, our malicious payload will be saved to %temp%/q2.exe, then executed. When looking at q2.exe, we can see the compile path of ‘T:\mandatory\Hence\one\Date\
Ronnie concludes that this malware “Is capable of grabbing a ton of credentials, mostly FTP”
To help organisations protect themselves from this malicious program, PhishMe has provided the C2 and user agents identified within this malware that can be downloaded via its github.
About PhishMe
PhishMe® provides organizations the ability to improve their employees’ resilience towards spear phishing, malware, and drive-by attacks. Our approach entails immersive training to effectively change employee behavior, empower users to detect and report targeted phishing attacks, and augment an organization’s existing security operations and incident response processes. With over 4 million individuals trained in 160 countries, PhishMe has been proven to reduce the threat of employees falling victim to advanced cyber-attacks by up to 80 percent. PhishMe works with Fortune 1,000 companies across many industries, including defense industrial base, energy, financial services, government, healthcare, and retail.






