It has been a few weeks since the original discovery of the Dyre malware, and the attackers have sent another wave of phishing, reports PhishMe. This time, the phishing campaign only went to one senior level individual within the enterprise.
Here’s a screenshot of the phish:
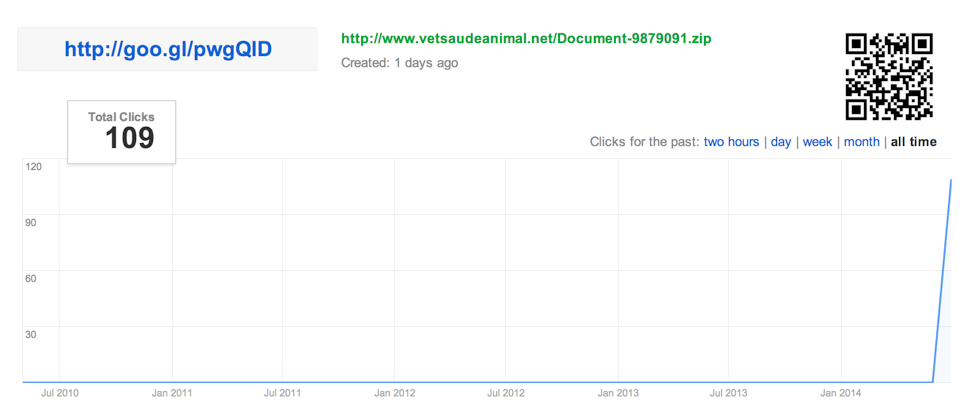
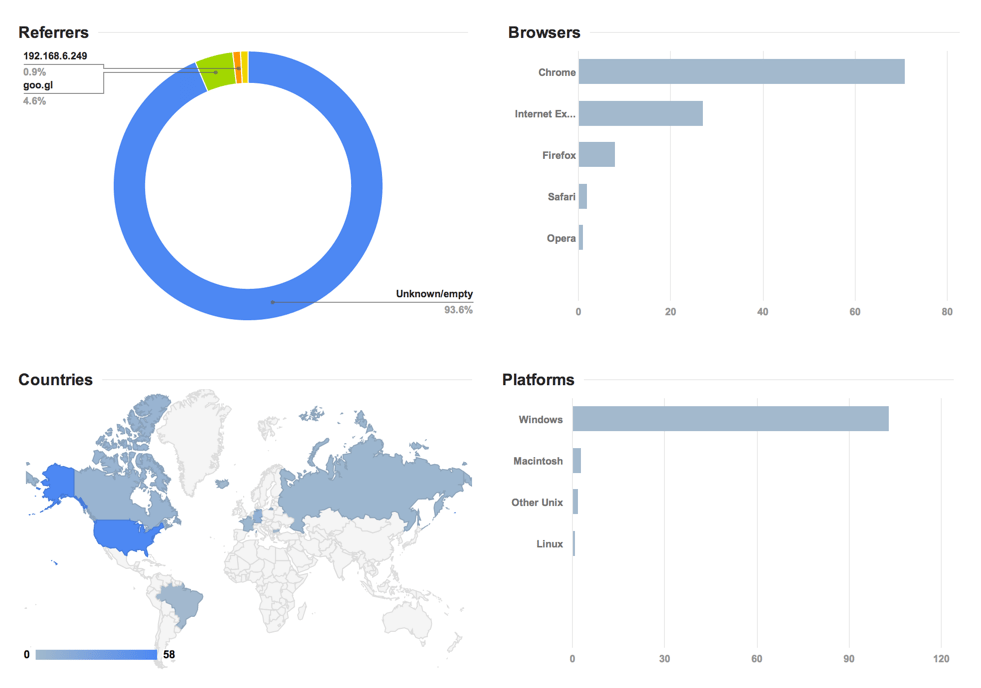
In the last few campaigns, the attackers made it difficult to access their Google Analytics page. However, the attackers slipped up this time, making it possible to uncover how many potential victims have fallen for the link. This gives further insight into the geographical location they may be targeting as well.
We can also see the country and browser that the individuals are using.
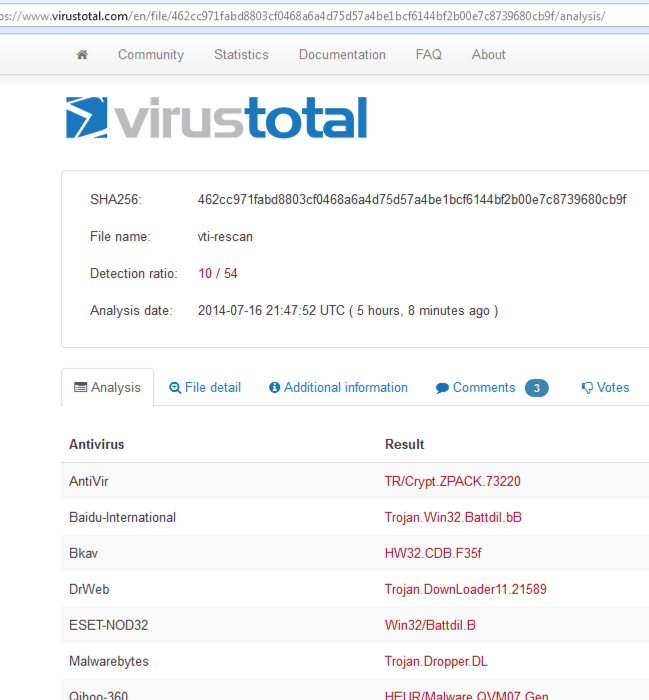
Once the zip file containing a screensaver file is downloaded and executed, several files are downloaded. The detection rate for the malware is very low, and starts out with the Upatre dropper with 12 out of 53 (at time of writing) AV vendors detecting the threat.
Another file, flagged as kegotip by the VirusTotal community, has an even lower detection ratio of 11 out of 54 AV vendors
And for the third piece of malware, Dyre joins the show! At the time of this writing, this is only picked up by 10 of 54 AV vendors.
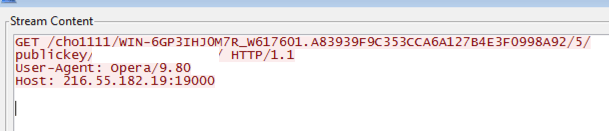
Based off the network data in Figure 6, it can be further confirmed that this is Dyre, as it matches the network traffic from PhishMe’s previous analysis.
While googleupdaterr.exe is quick to exit, if you’re quicker, it is possible to obtain a memory dump via process explorer. (Author note: Volatility works too, but for brevity, process explorer approach may be preferable) In the previous variant of Dyre, the string “C:\CPP_PROJECTS_GIT\DYRE\x64\Release\iebattle.pdb” was observed as the project path. Performing strings on the memory dump does not show this existing.
However, by grepping for “DYRE”, the attackers have may have left the message of “I’m DYRE”. By looking before and after this string, the following phrase of “Slava Ukraini!” is there as well, which translates to “Glory to the Ukraine!”
By looking at the capitalization of the phrases, we can come up with many possible theories; unless the author provides more clues, he/she will remain unattributable. “I’m DYRE!” may show that the attacker is referred to as Dyre or wants the malware referred to as that, or it could be slang, such as rouji (肉鸡), that is common among attackers.
“Glory to Ukraine!” seems to have a deeper meaning to the malware author. This phrase is common in the Ukraine, and has even been referred to as the unofficial motto. Jared Leto also shouted “Glory to Ukraine” during a concert in Kiev, supporting the independence movement.
How to find this in your enterprise
Here are a few tips for finding this malware and preventing further infections:
– Look for zip files being downloaded that contain executables and screen savers.
– Search for email artifacts from figure 1 to help identify this one and variants.
– Kimberly at StopMalvertising has put together a very deep analysis of Dyre, as well as the new changes in the malware. (removal of compilation artifacts)
By Ronnie Tokazowski, security researcher at PhishMe
About PhishMe
![]() PhishMe® provides organizations the ability to improve their employees’ resilience towards spear phishing, malware, and drive-by attacks. Our approach entails immersive training to effectively change employee behavior, empower users to detect and report targeted phishing attacks, and augment an organization’s existing security operations and incident response processes. With over 4 million individuals trained in 160 countries, PhishMe has been proven to reduce the threat of employees falling victim to advanced cyber-attacks by up to 80 percent. PhishMe works with Fortune 1,000 companies across many industries, including defense industrial base, energy, financial services, government, healthcare, and retail. For additional information, please visit: www.phishme.com.
PhishMe® provides organizations the ability to improve their employees’ resilience towards spear phishing, malware, and drive-by attacks. Our approach entails immersive training to effectively change employee behavior, empower users to detect and report targeted phishing attacks, and augment an organization’s existing security operations and incident response processes. With over 4 million individuals trained in 160 countries, PhishMe has been proven to reduce the threat of employees falling victim to advanced cyber-attacks by up to 80 percent. PhishMe works with Fortune 1,000 companies across many industries, including defense industrial base, energy, financial services, government, healthcare, and retail. For additional information, please visit: www.phishme.com.