As 2023 came to a close, it was easy to predict that breaches would continue to dominate the cybersecurity news. However, the scale of the events, specifically the Change Healthcare breach eclipsed all others for the year. The other event that shook not only the entire technology community, but also the world, was the Crowdstrike update debacle (which no one could ever predict.)
January
As January began, we learned that December 2023 ended with a report that Google settled its $5 Billion “incognito mode” class action lawsuit.
“The class action filed in 2020 alleges “at least” $5 billion in damages for Google unlawfully violated the privacy of millions by using cookies, analytics and tools in apps to track internet browsing activity even when users activated the Incognito mode in its widely used Chrome web browser.”
It will be curious to see how any member of the impacted class is supposed to collect any of that settlement. As we are all aware from previous class action settlements, the reward is usually not very substantial. According to one source, there were 2.65 billion Chrome users in 2021. A $5 Billion settlement spread across the full user population would amount to less than $2 per person. Even if a mere 50% of Chrome users activated incognito mode, it would double the payment to $4 per person. Is it worth the incredibly low payout to let Google know that you use incognito mode? My cynical side is quite sure that Google already knows if I am a Chrome user, but I am still uncertain about whether I will attempt to collect my big payout.
Another year-end statistic revealed – to no one’s surprise – that ransomware continued to increase over the last year. In fact, it increased nearly 33% from 2021. There is currently a movement underway to ban ransomware payments. Those in support of this idea believe that it is the only way to stop ransomware’s profitable arc. However, as we saw last year, where ransomware gangs reported some victims to the government when those victims failed to announce a breach, we can expect similar behavior when some of the ransomware thieves would find a way to twice victimize a target who surreptitiously violates the payment ban.
Similar to last year , the first half of January 2024 remained fairly quiet in the cybersecurity world. There were no monumental attacks. However, unlike the start of 2023 when the tech sector shed tens of thousands of jobs, this year saw only minor layoffs in the tech industry.
It has long been suspected that our mobile devices are actively listening to our conversations, subjecting us to advertising based on a casual reference that we may have had with another person. However, given the results of a study released by Consumer Reports, all of the conspiracy theories can be laid to rest. We are all aware of the data sharing that takes place across all the apps that we use, but the numbers are much larger than most folks would ever imagine.
Among other remarkable statistics, the findings that “186,000 different companies represented in the data of 709 participants”, and “The average participant in our study was identified in the data by 2,230 different companies” should lay to rest any thought that our phones need to listen to any of our conversations; all the information they need to target us with remarkable, albeit coincidental accuracy is readily available to any advertiser who wants to pay for it.
February
Following along the lines of the information from the January Consumer Reports study, Bloomberg News first reported how the incredible amount of data flowing around the internet is too much even for the spy agencies to manually parse, leaving them to use artificial intelligence to help correlate relevant data. That should come as no surprise, as AI is very useful for those mundane tasks. What is more interesting is how the spy agencies do not need to rely so much on traditional clandestine activities to gather data, since the glut of freely available information offers such a rich source of Open Source Intelligence (OSINT). The inferential value of this data has already resulted in actionable intelligence.
In an example of living on the grid by Living Off The Land, the Cybersecurity & Infrastructure Security Agency (CISA) released a report, indicating that an attacker group from the People’s Republic of China has been operating within at least four critical infrastructure sectors for as long as five years. The LOTL method uses software which is normally present on a system, such as Windows Powershell, to remain undetected. The attacker group is known by various names, most recently “Volt Typhoon.” It is believed that the attackers wanted to dwell in the systems so they could launch an active attack in the event of an international conflict. With all the zero trust architecture and practice initiatives, how have these critical infrastructure industries remain so vulnerable?
In cybersecurity, we often caution about insider threats. Usually, this is a warning about a rogue employee. However, the emergence of pandemic-led remote work has stretched not only the definition of the corporate perimeter, but also the definition of the insider threat. In a story reported by the BBC News, the husband of a British Petroleum (BP) employee was charged with violating stock trading laws by engaging in insider trades based on meetings that he overheard while his wife worked remotely. The employee, a member of the BP mergers and acquisitions team, was working on a deal while working from home, and the husband used the information to buy shares of the company that was about to be acquired. When the acquisition was announced, the stock of the acquired company rose by 71%, benefitting the husband by $1.76 Million. In the old days, the way to pry confidential information from a spouse often involved a method known as “pillow talk,” because it happened during intimate moments. Thanks to remote work, pillows are no longer required.
The deepfakes arrived in a very big way in February. Rather than using deepfake technology to sell a product, or to convince a family member to send some money for a fabricated emergency, cybercriminals used AI technology to defraud a company of $25 Million. The scam used fake video and voices of a CFO and other team members to conduct a video call, ultimately convincing another employee to transfer the money to an account controlled by the attackers.
March
March was consumed with the news of the Change Healthcare ransomware attack. Towards the end of February, Change Healthcare, which serves as the largest clearinghouse for healthcare insurers, providers, and prescription distributors in America, was hit with a ransomware attack. To clarify the terminology, the HIPAA Journal defines a healthcare clearinghouse, as:
“A clearinghouse in healthcare is a middleman between a healthcare provider and a health plan that checks claims from healthcare providers to ensure they don´t contain errors before forwarding them to a health plan for payment. Having a middleman to check for accuracy reduces workloads for both healthcare providers and health plans and accelerates the payment of claims.”
While this would normally be nothing more than a typical ransomware story, the plot took an unexpected twist. As reported by Brian Krebs, there is evidence that Change Healthcare may have posted a $22 Million payment to get the decryption key, but the ransomware criminals did not pay the affiliate who managed to compromise the Change Healthcare system.
The attacker used a ransomware-as-a-service offering, for which a commission would be paid for a successful attack. However, it seems that the as-a-service folks took all of the money, and shut down their operations, dubiously claiming that their site and assets were seized by law enforcement agencies. It is unclear if any decryption keys were given to Change Healthcare. It is also suspected that the stolen data may still be held by a very disgruntled, unpaid perpetrator who may seek to further extort Change Healthcare.
It took more than two weeks for Change Healthcare to restore the electronic prescription fulfillment, claims submission, and payment transmission functions. electronic payments and medical claims systems were restored nearly a week after that. It seems that even the most reliable backups (as well as the possibility that Change Healthcare paid for the ransomware decryption key) does nothing to expedite system restoration of such a large entity acting as a single point of failure.
In late March, Change Healthcare’s parent company, United Health Group, posted that they “advanced more than $3.3B to care providers through our Temporary Funding Assistance Program at no cost. We want to help care providers, especially smaller practices, who have been affected by this crisis.” The idea that they are “advancing” the money is one of the strangest choice of words for paying the clients what they have been owed throughout “this crisis”.
Sadly, the end of March also brought news of the passing of a pioneer in the security community. Ross Anderson, a pillar of security activism, and author of one of the most important works in the security community died unexpectedly. Bruce Schneier, who was a long-time friend and collaborator with Ross, offered one of the most touching tributes.
April
Early in April, we were able to get away from the Change Healthcare breach for a short moment. Zack Whittaker wrote a fascinating post about how police can request large swaths of data from tech companies to track criminals. Surprisingly, viewing a YouTube video can provide law enforcement with enough information to track down suspected criminal activity. In at least one case, investigators sent related links to the suspect as enticement to corroborate the criminal activity.
The Change Healthcare breach continued with a second extortion group claiming to have some of the stolen data. According to “Wired”, when pressed for evidence, the group sent over information that appeared legitimate. United Health also stated that the breach has cost $1.7 billion in losses for the company. The company has also declined an invitation by the US Congress to send a representative to testify about the event. Meanwhile, by April 23rd, Change Healthcare still was not functioning at 100% capacity, and the cost of recovery was expected to exceed $1 billion.
By the end of April, Change Healthcare admitted that they paid a $21 million ransom in an effort to protect patient data. While this is different than the $22 Million payment reported in March, it is curious to note that Change Healthcare paid at all, against the advice of most cybersecurity authorities. Bloomberg news reported that “a sample of the breached files found they contain personal information, including health data, that ‘could cover a substantial proportion of people in America’”. If a second extortion group truly has access to that data, then the initial multi-million-dollar ransom payment to the first extortion group demonstrates the reason that the authorities caution against paying ransoms. Alternatively, the original group could just demand payment indefinitely.
On April 29th, the UK became the first country to pass a law that bans the use of default passwords by manufacturers of IoT devices. This was enacted as part of the 2022 National Cyber Strategy. The National Cyber Security Centre (NCSC) created a handout sheet to educate consumers about the regulation. Most people immediately think of Silicon Valley as the manufacturing center of all things technical, but the UK is also home to hundreds of device and software manufacturers. Similar to how GDPR had global reach, one can expect that this new regulation will quickly reach beyond the geographic boundaries of the UK.
May
The CEO of United Health Group testified in Washington, D.C. in front of a U.S. House subcommittee, stating “To all those impacted, I am deeply, deeply sorry.” One could argue that all those impacted are deeply, deeply unimpressed and weary of such statements.
It is worth a moment to examine the progression of health care attacks, as it tells a very important story. Since 2016, ransomware has been on the increase, taking a sharp curve upwards in 2018, and has remained the predominant attack method for cybercriminals. The 2021, and 2022 Verizon Data Breach Investigations Reports showed a steady increase in attacks against health care organizations. Even then, Verizon reported that the attacks were shifting from internal threat actors to external actors. In the most understated prediction ever, the report authors noted:
“For the second year in a row, we have seen Personal data compromised more often than Medical in this sector. That strikes us as strange, given the fact that this is the one sector where you would expect to see Medical information held most commonly. However, with the increase of External actor breaches, it may simply be that the data taken is more opportunistic in nature. If controls, for instance, are more stringent on Medical data, an attacker may only be able to access Personal data, which is still useful for financial fraud. Simply put, they may take what they can get and run.”
Verizon accurately warned about the extreme value of health care data, and the recent attacks against the health care industry demonstrates that the criminals paid attention, perhaps more so than the health care organizations. In the early part of May, another attack against a health care provider was reported, disrupting 140 hospitals, and 40 senior living facilities across 19 states. While it is interesting that there was a slight dip in the Verizon reported attacks against health care organizations in 2023, it more than made up for it in 2024.
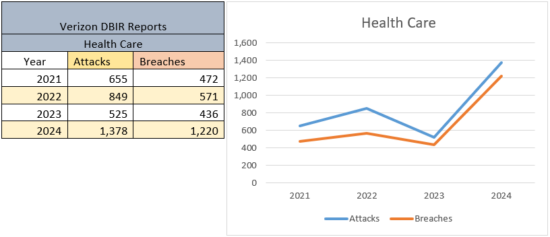
The history of ransomware attacks against health care organizations should serve as a clear warning to others. Industry professionals are now showing that attacks against the energy sector are rising. We can only hope that those in the energy sector, as well as other critical infrastructure sectors are taking heed to improve their security before the trend resembles what has occurred in health care.
The month concluded with an announcement by the Department of Justice about what the FBI has called “likely the largest botnet ever”. The botnet, known as 911 S5 is believed to have infected more than 19 million computers worldwide and is responsible for filing fraudulent pandemic assistance and unemployment applications, as well as providing access to child pornography. The malware was disguised in six free VPN software packages. The FBI published detailed removal instructions for the public.
June
The largest event in June was the attack against CDK Global, which provides technology to automotive, heavy truck, recreation, and heavy equipment industries. As its name indicates, it has a global presence, enabling the operations of motor vehicle dealers at 15,000 locations worldwide. The attack crippled systems, and full service was not restored for many customers until the end of the month.
The HIPAA Journal reported a story that seems to be the trifecta of insider threat, third party risk, and medical technology risk. A terminated subcontractor employee of a medical transcription service stole at least one million patient records. The authorities arrested the individual, but it is unclear if any of the records were sold to malicious data brokers. At least one victim has filed a class action lawsuit against the parent company and the subcontractor. Many times, cybersecurity professionals speak of regulatory and reputational damage that can befall a victimized corporation. While there is no hard evidence of a company suffering crippling consumer-driven reputational damage from a cybersecurity incident, this class action lawsuit makes it evident that it is time to add civil perils to that list of possible consequences.
In Part 2 of the year in review, we will continue our march through the accumulating breach reports, as well as a surprising first-ever cyber-weapon attack that killed multiple people, and injured thousands.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.




