July
AT&T announced (in a financial filing) the discovery of a data breach dating back to 2023 that affects almost every AT&T customer. “The stolen data also includes call records of customers with phone service from other cell carriers that rely on AT&T’s network, the company said.” It should be noted that the delayed reporting of the incident was at the behest of law enforcement, citing national security concerns. Techcrunch reported that the data breach is related to similar criminal activity that targeted the Snowflake cloud service provider. This was also the second breach this year for AT&T customers.
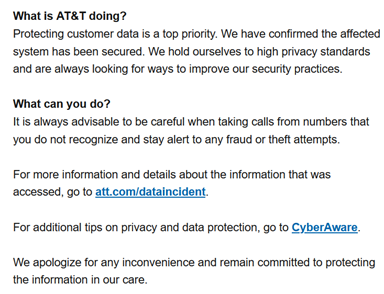
It was also reported that AT&T paid the attacker $300,000 to delete the data, including a video of the deletion event. Does anyone other than AT&T believe that this was the only copy of the data in the attacker’s possession? More insulting is the message that was sent to affected customers. AT&T did not offer any credit monitoring, instead advising its customers of how to best protect their privacy. One can only surmise that the logic behind this is that since no Personally Identifiable Information (PII) was taken, there is no need for credit monitoring services. The mere idea that a phone numbers cannot be traced to a person is infuriating. If that were true, then why was this data worth $300,000 to AT&T? Humorously, the message to customers includes a heading titled “What is AT&T doing?”, which is exactly what every AT&T customer is probably exclaiming as well.
On July 19, the world awoke to a major internet outage caused by an update to the Crowdstrike security platform. The outage impacted Windows-based systems, which grounded airplanes, impacted hospitals, banks, energy companies, and just about every business that had even the most peripheral connection to the Crowdstrike platform. A patch was released, however, after the initial impact and subsequent recovery, Crowdstrike stock dropped more than 12% over the course of the trading day, and continued a downward trend over the remainder of the month, losing more than 25% of its value. The global impact was estimated to be in the billions of dollars of lost revenue. It is notable that the event was the result of a technological blunder, rather than the result of a breach or privacy violation. It is also predicted that Crowdstrike will recover its value over the next few months.
July ended with an announcement by Intel Corporation that it was reducing its workforce by 15%, totaling the elimination of 15,000 jobs.
August
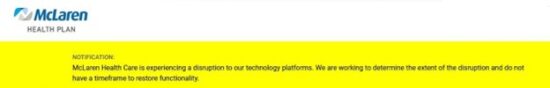
2024 continues to maintain the title of The Year of the Health Care Data Breach. McLaren Health Care announced that it was victimized by another ransomware attack. This is the second attack against the company in two years. A shocking aspect of the event is that the company made no prediction about when systems would be fully functioning.
Brian Krebs reported that a consumer data broker was compromised. Troy Hunt’s analysis indicates that the attack exposed 137 million unique email addresses, and further analysis by various other sources indicate that there are more than 250 million unique social security numbers in the stolen data. It seems that the data is in an extremely disorganized state with names not matched to social security numbers, as well as information for deceased individuals. The reported price demanded by the thieves for any interested buyer is $3.5 million. Considering that the data is in such a jumbled state, and that it also contains useless information, the asking price seems to exceed any real benefit. It is also suspected that the data is the same as what was offered in an earlier breach from April of this year, further supporting the idea of its uselessness. Simply stated, more reliable data is apparently available elsewhere.
In mid-August, NIST announced that it “has finalized its principal set of encryption algorithms designed to withstand cyberattacks from a quantum computer.” Quantum computing has often been seen as a challenge to existing encryption, so it is good to see that work is being performed with equal vigor to keep pace with the development of quantum technology.
In other encryption news, towards the end of August, the Chief Executive of the popular Telegram app, Pavel Durov, was arrested in France. “The investigation is reportedly about a lack of moderation, with Mr. Durov accused of failing to take steps to curb criminal uses of Telegram.” Since Telegram offers the option to use end-to-end encryption – it is not on by default – one can only wonder how the app moderators are expected to reveal the contents of the messages transmitted across the platform? It would be surprising to discover that the criminals do not use the encryption option.
September
Following the Pavel Durov arrest in August, Telegram announced that it will now share some user data of those who violate the platform’s terms of service with law enforcement officials.
The most shocking cybersecurity story of September was the apparent supply chain attack against paging devices in Lebanon that caused the devices to simultaneously explode upon receiving a signal from a spoofed phone number. The attacks injured more than 2,500 people and killed at least 12 immediately. A day later, walkie-talkie devices exploded in Lebanon, killing an additional 20 people, and injuring at least 450 people. It is believed that both sets of communication devices were equipped with an explosive during the manufacturing process, making this the deadliest cyberweapon attack known to date.
October
In late October, the Crowdstrike incident took a new, confusing turn. Delta Airlines filed a lawsuit against Crowdstrike, stating that Crowdstrike’s faulty software update cost more than $500 million dollars in losses to the air carrier. Crowdstrike also filed a lawsuit against Delta, claiming that their update did not cause Delta’s failure, and that Delta refused help from both Crowdstrike and Microsoft. Does Crowdstrike often reach out to help companies who suffer system failures that are not the result of a cybersecurity incident?
Also in late October, United Healthcare announced that 100 million people were impacted by the Change Healthcare breach that took place in March, making it the largest healthcare breach to date.
November
In late October, more details about the September pager attacks in Lebanon were reported. Bruce Schneier offered the most concise summary of the event in his November newsletter.
As of November 13th, Crowdstrike’s stock price was up 34% over the previous three months.
As one source states: “This robust performance, achieved despite deal delays in the final weeks of the second quarter, reflects the loyalty of CrowdStrike’s customer base and the trust built over the years.” Once again, the idea of reputational damage is weakened against forces of corporate stability and customer loyalty.
Also on November 13th, the FBI and CISA released a joint statement about an attack against US telecom companies, stating that the attacks were “a broad and significant cyber espionage campaign”.
Throughout the year, Artificial Intelligence was a constant presence in the news cycle, yet nothing rose to the top of the cybersecurity food chain. Despite dire warnings of AI being used to influence America’s presidential election, there was little evidence of any viral moments. However, in November, a couple of related events occurred that could be strong warnings of what is to come with AI. A nefarious use of the technology forced a school in Pennsylvania to shut down for a day when it was revealed that a student created sexually explicit AI images of nearly 50 female classmates. In a more positive example, researchers used AI to identify three subtypes of the congenital brain disorder. While not cybersecurity related, both examples fuel the ongoing debate about whether AI will ultimately benefit or hurt humanity.
Towards the end of November, the head of the US Senate’s Intelligence Committee declared that the recently announced breach of US telecom companies by suspected Chinese operatives was the “worst telecom hack in our nation’s history – by far”.
December
The year wrapped up with the news that Google’s “Willow” quantum chip could solve a complex mathematical calculation in 4 minutes. The same calculation would take the world’s fastest supercomputer ten septillion years to solve. Even with the announcement by NIST in August of a “principal set of encryption algorithms designed to withstand cyberattacks from a quantum computer”, from a cybersecurity standpoint, it is unclear if that principal set is ready to compete with the reality of this latest development.
As with last year, it would be a grave injustice to overlook all those who made this year in review piece possible. These are some of the folks and sites that generously offer their services free of charge. They should be in every cybersecurity professional’s bookmarks and “required reading” lists (shown alphabetically):
arsTECHNICA: https://arstechnica.com/
Brian Krebs: https://krebsonsecurity.com/
Cybersecurity & Infrastructure Security Agency (CISA): https://www.cisa.gov/
BackLinko: https://backlinko.com/
BBC News: https://www.bbc.com/
Bloomberg: https://www.bloomberg.com/news/
Bruce Schneier: https://www.schneier.com/
CNN: https://www.cnn.com/
Consumer Reports: https://innovation.consumerreports.org/
Crowdstrike: https://www.crowdstrike.com/
Data Breach Today: https://www.databreachtoday.com/
Emisoft: https://www.emsisoft.com/
GOV.UK: https://www.gov.uk/
HIPAA Journal: https://www.hipaajournal.com/
National Cyber Security Centre: https://www.ncsc.gov.uk/
National Institute of Standards and Technology: https://www.nist.gov/
NY Times: https://www.nytimes.com
Research Gate: https://www.researchgate.net/
Reuters News: https://www.reuters.com/
SANS Internet Storm Center: https://isc.sans.edu/index.html
Tripwire State of Security blog: https://www.tripwire.com/state-of-security
Troy Hunt: https://www.troyhunt.com/
U.S. Department of Energy: https://www.energy.gov/
Verizon: https://www.verizon.com/
WashU Medicine: https://medicine.washu.edu/
World Economic Forum: https://www.weforum.org/
Zack Whittaker’s weekly security newsletter: https://this.weekinsecurity.com/
ZDNet: https://www.zdnet.com/
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.




