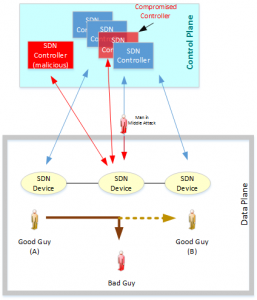
In Software Defined Network (SDN) architecture, the control plane is separated from the data plane and implemented in a software application. In this blog, we will briefly analyze the security threats to SDN because of this decoupling. The controller is the most vital component in SDN architecture mainly because it defines the data flows that occur in the Data Plane (traffic flow manager). It is the “brian” of the network and therefore the attacks on and vulnerabilities in controllers are probably the most severe threats to SDN architecture. If the controller is compromised, the attacker can disrupt the data path. For example in Figure below, the compromised controller can alter the traffic flow in the SDN device to send the traffic to Bad Guy. The communication between the controller and the SDN device is also an essential part of the SDN and can be exploited in the following ways:
– Install malicious controller to send malicious instruction to the underlying SDN devices.
– Man in the middle attack for communication between the controllers and the SDN devices to change the instruction sent by the trusted controller.
These vulnerabilities can be used to launch the DoS attacks on the SDN devices or to change the data path to get access to sensitive information. The possible solutions to mitigate these threats in SDN architecture are:
– The controllers need to be placed at secure location in the network with stringent access policy.
– Out of band management to establish dedicated channel between the controller and SDN devices.
– Secure communication channel between the controller and SDN devices.
– Establish trust relationship between the controller and SDN devices.
In addition, the network will still have to cope with existing threats such as attacks on vulnerabilities in network devices and management stations.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.