Of all information security threats, the ‘insider’ security threat usually isn’t the image that people’s minds go to first. Angry young men in darkened bedrooms, perhaps. Or offices full of reclusive geniuses, hacking away at the behest of their government, maybe.
The costliest form of information security incident is none of these things. It is the incidents caused by regular, every day staff members, acting maliciously, accidentally or obliviously to the damage they could cause by their actions, or lack thereof. Causing or enabling the leak of information to people outside the organisation, or to others inside the organisation who shouldn’t have it.
A recent survey found that security incidents caused by malicious insiders cost companies an average of over $144,000 each year. Another survey found that every company experiences an average of six breaches like this in 2015 alone, and 75% of organisations experienced at least one.
Forthcoming regulations from the EU are set to apply extremely harsh punitive fines to any company responsible for information containing details of its citizens, which leaks to the public, no matter the cause. Staff member accidentally share a spreadsheet containing customer names and addresses? The fine could exceed €20 million. The regulators – they’re not messing around.
This, now, qualifies as a severe, even existential risk to companies everywhere. It is up to us, as practitioners of SharePoint, the biggest information management system in the world, to put information security at the top of our list of concerns in everything we do.
Defining the ‘Insider’
For the purposes of this discussion, I’m going to give a definition of the term ‘insider’. I’m going to exclude administrators, who often necessarily have high privilege access to information in order to do their job. I’m also going to exclude ‘hackers’, using subversive technical means to gain access to data.
I’m talking about regular, every day staff members working in the business. And I’m talking about anyone to whom they have given or lost their access credentials.
The Nature of the Insider Security Threat
Most other information security threats stem from gaps in the IT landscape. They tend to warrant predominantly technical responses such as firewalls, DMZs, intrusion detection, etc.
The insider security threat is different. To understand the threat, is to recognise the nature of how information is created, shared, stored and moved within organisations. There are four pillars: people, information, business environment, and technology.
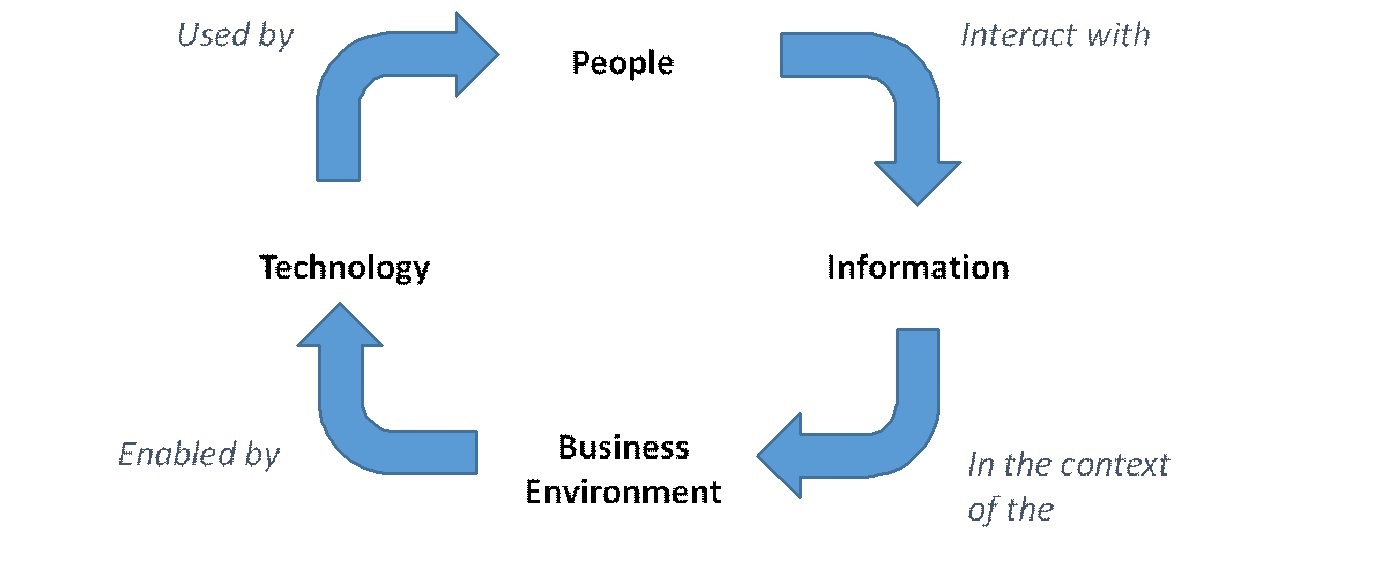
So when it comes to the nature of the insider threat, we can frame it using these four pillars also. Let’s list some aspects of the reality of each:
People
- Disgruntled staff
- Phishing threats and social engineering
- People constantly joining, moving, leaving
- External partners / customers / suppliers
- Poor security awareness / too busy to care
- 20% of staff willing to sell their passwords for $1000
Information
- Massive and exponentially growing volume of data
- In many different forms, including documents, emails, images, databases, printouts
- Moving independently through different lifecycle stages
- Of various sensitivities, classifications and purposes
Business Environment
- Constant business change – new customers, old partners, departments starting, offices closing, strategies and priorities shifting, organisational structures changing, mergers and acquisitions
- Working practices are increasingly flexible and collaborative
- The best intelligence about the information lies with the people in the business who are closest to the information, but IT tends to be responsible for information security
- IT tends to operate at arm’s length from the rest of the business
- Sometimes we try to bridge the gap with workflow and business processes, with varying success
Technology
- Information scattered across multiple platforms of varying maturity and capability
- The rise of the cloud – bringing powerful capabilities more cheaply, but also downsizing of IT teams, skills and budgets
- The rise of mobile devices and workforces – everything is available everywhere, anytime
- Many security solutions and vendors competing for market share
As with any risk, the insider threat can be stated as the likelihood of an incident, crossed with the potential severity of an incident.
So, any effective solution for minimising insider security threat needs to sit at the junction of all four areas at once, reducing the likelihood and severity of any incident.
Solutions which focus too narrowly on only one or two of these areas are only ever going to have limited overall effectiveness.
Relevant Technologies
There are a wide variety of technology types which are relevant to insider security. Choosing which technologies are right for your business must begin from an analysis of your own specific circumstances, risks and priorities.
Following is a list of some of the relevant technology types. This is certainly not an exhaustive list, but should cover the main areas of interest to most organisations.
- Access Management – controlling and reporting on who has access to what, and how that changes over time
- Data Loss Prevention – detecting, alerting and preventing documents and other forms of information containing sensitive details (such as credit card numbers, DOBs, social security numbers, etc.) when moving across boundaries or between people in violation of business rules
- Behavioural Analytics – monitoring people’s interactions with systems and information, detecting, alerting and preventing anomalous behaviour. e.g., if a user tries to download an entire document library when they’ve not actually been involved with the information, might trigger an alert for an administrator to investigate
- Data Classification – classifying information by some combination of criteria, such as sensitivity, audience or purpose, and then using those classifications to drive security behaviours in both people and technology
- Rights Management – extending and enforcing rights to interact with information in different ways, including when the information has left its host system. e.g. a person may only open a particular document if they have rights to, even after that document was emailed to them outside the network
Other technologies such as authentication, identity management, lockboxes, CASBs, encryption, firewalls, and intrusion detection are also relevant in a general sense, but are more foundational and technical than this discussion is intended to cover.
How SharePoint / Office 365 Measure Up
Some technology types relevant to the insider threat are quite well serviced through SharePoint, in particular Office 365 which is evolving rapidly. Mileage will vary for on-premises deployments of SharePoint, depending on which version of SharePoint you’re running, and which related technologies you’ve deployed alongside it.
- Rights Management – now generally available through Office 365. On-premises, requires Active Directory Rights Management Services (ADRMS).
- Data Loss Prevention – capabilities coming online in Office 365
- Behavioural Analytics – While this is not generally provided through Office 365 yet, the combination of the Audit and Graph APIs is now providing much of the big data that is the basis for behavioural analytics. Expect to see this space maturing over the next 12-18 months.
SharePoint’s Biggest and Most Difficult Insider Security Gap
In my judgement, the biggest gap in SharePoint in terms of the insider security threat is, and has always been its permissions model.
I’m referring to SharePoint on premises, SharePoint Online and OneDrive for Business collectively here, because their permissions models are effectively identical.
SharePoint’s model for managing user permissions tends to be difficult to manage, especially at scale. Configuration errors where people have access to information they shouldn’t have, are commonplace. They are also extremely difficult to detect, because doing so requires a close understanding of the people, business and technical perspectives of every individual piece of information (i.e. each of the four pillars above).
A recent survey (not SharePoint specific, but certainly relevant) found that 71% of staff have access to more information than they should. Bringing this number down dramatically is very difficult. For years, Information Architects have prescribed governance processes to address this issue, but success has always been limited.
But minimising this number is fundamental to minimising the likelihood and severity of insider security incidents. If this number were theoretically zero (i.e. every person always has access to only the information they need at any given moment, and none that they don’t), this would equate to a minimisation of the insider attack surface, and thus minimisation of the risks.
How This Gap Arises – 1. User Experience
Firstly, the SharePoint user experience is oriented towards information sharing – making it easy to grant access for people to information. This is great for facilitating collaboration and information reuse. But the counter-point – revoking access from people to information when it is no longer needed – is much less prominent.
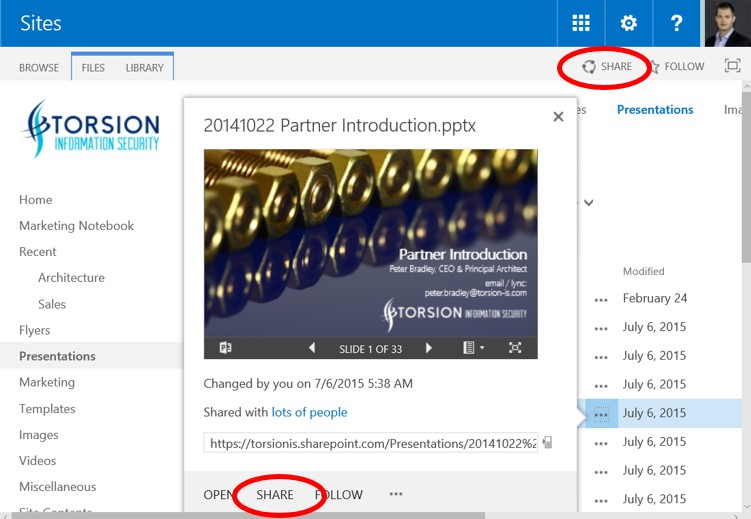
Take the following screenshot of a SharePoint document library as an example. There are two prominent links in the main user experience, suggesting that we expand access rights, circled in red.
Want to revoke access for a person to a document? I count eight clicks (Context menu > … > Advanced > Shared with > Advanced > Select User > Remove User Permissions > OK). And that is only after some trigger for someone to go on this journey in the first place. In reality – its just not going to happen in any normal course of events.
The result is that people tend to accumulate access to information over time. The business circumstances which made it appropriate for a person to have access to a piece of information may have changed, but people keep their access anyway. We call this phenomenon, ‘Privilege Creep’.
How This Gap Arises – 2. ‘Who’ is Not Meaningfully Connected to ‘Why’
It is easy to grant access for a person to a piece of information. It is much harder to know why this was done in the first place, unless you happen to be the person who made that that decision. And even then, are you really going to remember why you gave someone access to a document at 2am 18 months ago? Probably not.
How is this relevant? Because unless we know why someone has access to something, we can’t easily reassess whether they should continue to have access to something. It is very difficult to determinethe correctness of access permissions in the future, especially as the information ages, and people’s attention moves on.
And if we can’t assess that, we can’t revoke people’s access when they no longer need it, unless we interrogate the institutional memory of the specific people involved. We certainly can’t do that automatically.
But given that we may have thousands of staff, millions of documents, and squillions of individual access control decisions along the way, automatically is the only way it is ever going to work.
SharePoint 2010 did actually provide the basis for improving things in this area, when it enabled role-based access control through claims-based authentication. This allowed us, for example, to provide read permissions for a document to anyone in a given department. This was why someone should have access, not who should have access. It was a great start.
But the unfortunately this functionality didn’t fully reach its potential. It required complex customisation to be used in practice. It had scaling issues, was difficult to manage, and most importantly it couldn’t be ‘just switched on’ unless you were a serious SharePoint expert.
And even though this functionality remains in SharePoint 2016, perhaps the fatal blow was that it is not supported in Office 365.
How This Gap Arises – 3. Empowering IT, not the Business
A number of vendors have tried to fill this need, by providing tools which empower IT teams to monitor, manage and audit people’s access to information. Varying levels of aggregation across the security groups involved
But this highlights another fundamental problem – IT tends to operate at arm’s length from the rest of the business. Whoever is responsible for controlling who has access to what, and how that changes over time, must be in a good position to understand the context, sensitivity, purpose, and nature of the information itself.
This is only ever going to be the people in the business who are closest to the information. It is never going to be the IT teams – no matter how many business processes we create to try and bridge that gap in understanding.
[su_box title=”About Peter Bradley” style=”noise” box_color=”#336588″][short_info id=’68629′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



