The human factor often plays a role in data breaches, primarily because their inherent biases can be exploited. This vulnerability is especially pronounced in the digital age, where user authentication is a cornerstone of online applications and services. The most common method, static passwords, epitomizes this issue – users must create, remember, and enter these passwords to access their accounts and sensitive information. However, password fatigue, the tendency to reuse or choose weak passwords due to the overwhelming number of accounts and complexity requirements, undermines their effectiveness.
The Evolution of Authentication Methods
Single-Factor Authentication
When used with a username, passwords alone are considered Single-Factor Authentication (SFA). Over the years, various policies have been introduced to enhance password security, including NIST special publication (800-63B). These policies have since evolved, but passwords remain a weak link in security. The 2024 Data Breach Investigation Report (DBIR) highlights that 68% of breaches involved a non-malicious human element, such as falling victim to social engineering attacks.
Two-Factor and Multi-Factor Authentication
To mitigate issues with password-only authentication, companies across the globe have started requiring additional factors to authenticate their users. One widely used mechanism is dynamically generated One-Time Passcodes (OTP) sent to phones or emails. However, any OTP-based MFA still falls short in preventing phishing or password replay attacks. OTPs are also prone to attack types, such as Man-in-the-middle and SIM swapping. This attack works successfully even with one-time use and short-lived OTPs.
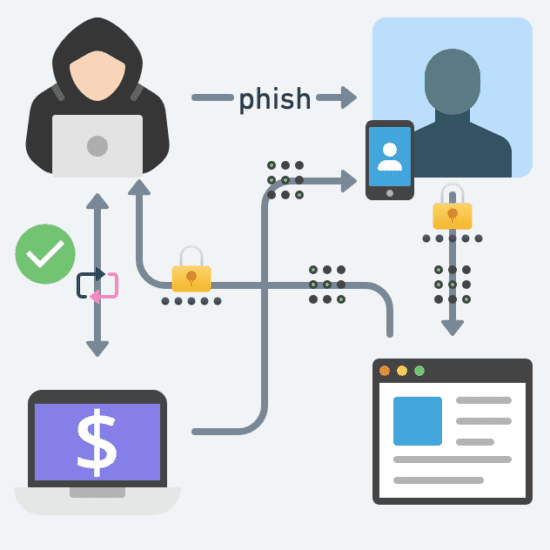
What is a Good MFA Strategy?
So, how can one design a strong MFA strategy that addresses the problems discussed above without letting customers assume that their data is protected with OTP-based MFA? Generally, when it comes to factor types used in authentication, there are three types: something you know, something you have, and something you are. To effectively use these factors and raise the authentication bar, the industry has developed several approaches, with three main ones frequently mentioned in the Information Security space: Web Authentication (WebAuthn), FIDO2, and the latest buzzword, Passkeys.
Web Authentication (WebAuthn) and FIDO2
FIDO2, WebAuthn, and Passkeys are related but distinct concepts that leverage Public Key Infrastructure (PKI) to provide better and stronger authentication factors to users. The goal is to eliminate password usage, as we all know it. FIDO2 is the overarching standard developed by a joint effort between the Fast IDentity Online (FIDO) Alliance and the World Wide Web Consortium (W3C).
PKI is at the heart of these technologies, providing cryptographic support for secure authentication. When a user triggers a registration event with a FIDO2-enabled service, the WebAuthn API facilitates the creation of a unique public-private key pair for that specific domain. The authenticator generates the key pair, stores the private key securely on the device, and sends the public key to the service, which verifies and stores it for eventual authentication attempts. These keys are tied to the web service domain name and cannot be used on other services with different domains, providing strong protection against phishing attacks.
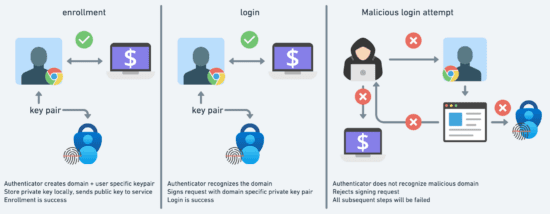
Passkeys: Spearheading the Passwordless Movement
The concept of passkeys was first introduced in May 2022 by Apple, Google, and Microsoft in a joint effort to expand support for passwordless sign-in authenticators. Users are not against security features; they want them to be easy to adopt. Passkeys are built to be more user-friendly and widely adoptable, improving the usability model of FIDO2 and WebAuthn. They do not require purchasing new hardware, remember long forms of multiple strings, and can be stored in password managers or devices they already own—for instance, Apple and Google support syncing passkeys across user devices through their secure technologies. Apple’s implementation uses iCloud Keychain to sync passkeys created on one device, like a MacBook, to another, like an iPhone.
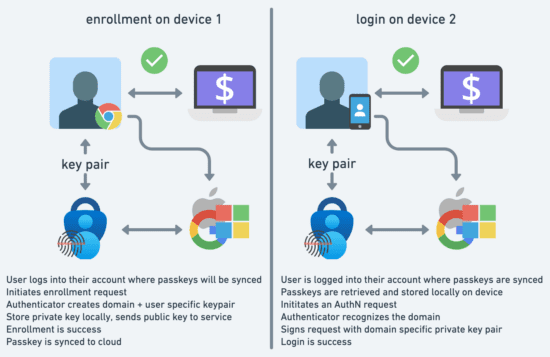
Conclusion
Passkeys provide a great alternative solution to passwords; not only do they provide significant security benefits, but they also come with excellent user convenience. Passkeys align with fundamental yet highly effective cybersecurity practices. They are backed by leading tech companies committed to making it a successful attempt to eliminate passwords. Because of these reasons, the time is NOW for enterprises to consider providing passkey as an option for their users. Passkeys align with basic but very effective cybersecurity practices. A simple Google search will reveal that complex account creation and weak login practices can negatively impact the business’s revenue. This underscores the importance of providing simple to-adopt, more secure signup, and login options using solutions such as passkeys.
Many major customer-focused services already support passkeys, including Amazon, Microsoft, Google, Apple, DocuSign, PayPal, and Shopify, to name a few. A community-driven Bitwarden passkey index tracks which platforms and websites currently support passkeys. If your enterprise isn’t on the list, now is the time to join the passkey revolution. Security practitioners and application developers with influence should prioritize passkey support by adding it to their roadmap items. To learn how to deploy or convert password-based authentication to support passkeys, explore the resources at passkeys.dev. By taking this step, you can contribute to a more secure, passwordless future, protecting users and their data from evolving cyber threats.
Opinions expressed in this article are solely the Author’s own and do not express the views or opinions of the Author’s employer.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.