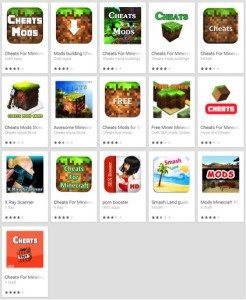
ESET has discovered over 30 scareware applications available for download from the Google Play store. The malicious applications, which pretended to be cheats for the popular Minecraft game, have been installed by more than 600.000 Android users.
It’s not easy to slip a malicious application into Google’s official Play Store these days. Google’s automated application scanner, Bouncer, helps in reducing the number of malware on the official app store. Yet, some baddies do occasionally get by, as demonstrated by our recent discovery of over 30 scareware applications that have been uploaded to the Play store in the course of the last 9 months
Most of the rogue applications pretended to be cheats for the popular Minecraft game. All of the discovered apps were fake, in that they did not contain any of the promised functionality and only displayed banners that tried to trick users into believing that their Android system is infected with a “dangerous virus”. Users were then directed to remove viruses by activating a premium-rate SMS subscription that would cost them 4.80 EUR per week.
All of the identified scareware apps behaved in a similar way, the only differences being in the names and icons of the applications. They were uploaded to the Play store by different developer accounts, but we assume that these were all created by one person.
The first scareware applications were uploaded to the store in August 2014. During the time they were online, they received poor user reviews and negative comments. Yet, according to public data from the Google Play store, several of them were installed between 100.000 – 500.000 times and the total number of installations of all 33 scareware applications lies between 660.000 and 2.800.000.
ESET security software detects this threat as Android/FakeApp.AL. After our notification, Google has taken the apps down from the Play store.
Analysis
After installation, all of the applications looked and behaved in a similar manner. The apps’ icons resembled the official Minecraft game.
After launching the application, the whole screen was covered with flashing advertisement banners. The app itself has three buttons – Start, Options, Exit, but none of their functionality was implemented in the code.
The language of the scareware advertisements is based on the geographic location of the device – a common practice in ransomware.
Any user interaction with the application – either clicking the Start, Options, and Exit buttons, or clicking on one of the numerous ad banners – will lead to an alert window popping up, saying that the device is infected with a virus and gives the victim the possibility to remove it.
Clicking on the alert leads to another step of the scam – several websites with more scareware messages. One of these websites tries to appear as if they belonged to the legitimate AV vendor, G-Data.
In the endgame of the scam, the scareware prepares an SMS in the system default SMS application. The text of the SMS appears as an activation of the antivirus product. The application does not have permissions to send the SMS itself and solely relies tricking the user to do it manually by social engineering. If the user falls for the scam, it will cost him 4.80 € per week.
Note that the scam webpage has nothing to do with the legitimate G Data security software.
Conclusion
The damage that this recent Android malware discovery can inflict is perhaps less acute when compared to the file-encrypting Android/Simplocker but the seriousness of this threat lies in the fact that it may have been downloaded by almost three million users from the official Google Play store.
Google’s Bouncer has been used since late 2011 on all uploaded applications and it has decreased the percentage of malicious applications in the store by about 40%. In March 2015 Google announced that all applications will also be reviewed by humans. This step should increase security and further lower the amount of malicious applications on Google Play.
Generally, Android users can effectively avoid the installation of malicious or unwanted applications. Refrain from downloading apps from unofficial sources and keep security software on your Android (ESET Mobile Security, for example) up to date. It is also advisable to spend some extra time to read reviews from people who already installed it and to consider what permissions an app requests during installation.
By Lukas Stefanko, malware researcher, ESET