In the first half of 2021, we released our Security Outcomes Study: Endpoint Edition. We worked with an independent research firm to conduct a double-blind survey of 4,800 IT and security professionals for our study. Those individuals’ responses demonstrate the value of endpoint security solutions including best practices and program-level outcomes that organizations can use to shape their endpoint security initiatives going forward.
Let’s examine some of the study’s major findings below.
Less Than Half Were Successful in Avoiding a Major Incident
In our survey, 43% of respondents said that their organization had succeeded in avoiding major security incidents and losses over the past couple of years. That’s not to say they didn’t struggle to some degree along the way. That’s also not to say that they didn’t suffer minor or even moderate security incidents in that period. Rather, it means that their security controls helped to preserve their reputation, advance their security goals, and keep them out of the headlines.
We wanted to know how many organizations had experienced a major incident or loss. To find that out, we posed a follow-up question: “Has your organization actually had a major security incident or loss in the last two years?” Approximately two in five survey participants responded in the affirmative, while another 5% said they weren’t sure.
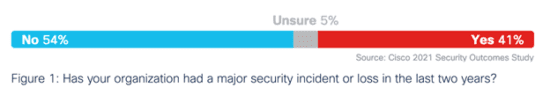
These findings raised the following question. “What threats are helping to drive these major security incidents and losses?”
We examined critical-severity Indicators of Compromise (IOCs) observed on our customers’ networks to find out. Overall, we found that dual-use tools came in first place at 23% of those significant events. Malicious actors specifically leveraged PowerShell Empire, Cobalt Strike, PowerSploit, Metasploit, and other utilities for both exploitation and post-exploitation tasks, as doing so helped them to reduce the noise surrounding their attacks. This is the logic behind using “living off the land” techniques. By abusing legitimate tools for malicious purposes, attackers increase their chances of avoiding detection by not deploying foreign tools that could otherwise raise a red flag with AV tools, a behavior analytics engine, and/or other security capabilities.
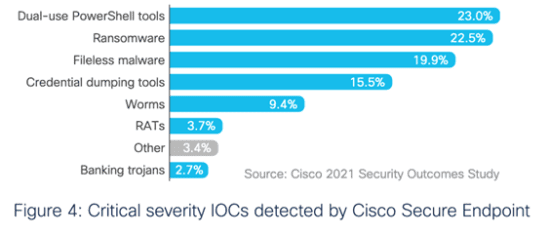
As you can see from the screenshot above, ransomware came in second just behind dual-use tools at 22.5% of critical-severity IOCs. Those attacks highlight the extent to which malicious actors now use email, Remote Desktop Protocol (RDP) weaknesses, and other vectors to compromise an endpoint with ransomware. From there, they eventually attempt to spread to other endpoints containing sensitive information as a means of facilitating double extortion.
Fileless malware came in third at 19.9% of critical-severity IOCs. The important thing to note about fileless malware is that signature-based AV solutions can’t detect it because it doesn’t have a signature or executable files. Instead, it deliberately injects itself into processes and uses registry activity to avoid detection.
No wonder then that “Defense Evasion,” one of the Tactics discussed in the MITRE ATT&CK Framework, appeared in 50% of critical IOCs we detected on the endpoint level.
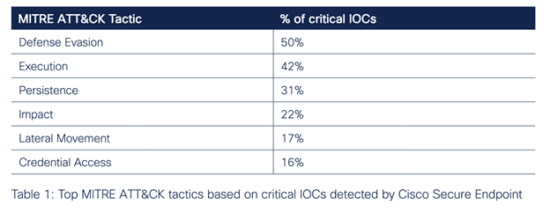
Execution came in second place at 42% of critical IOCs. This was followed by Persistence, Impact, and Lateral Movement at 31%, 22%, and 17%, respectively. Credential Access was least prevalent in critical IOCs we observed at just 16%.
How Organizations Can Avoid Falling Victim to These Threats
In response to the threats identified above, we conducted a multivariate analysis of our survey data to pull out some practices that explain why some organizations’ endpoint security efforts tend to succeed over others. We found that a proactive tech fresh strategy had the greatest impact. Indeed, we found that this exercise helped organizations to increase their chances of avoiding major incidents and losses by 5%-9%, with an average of 7.2%.
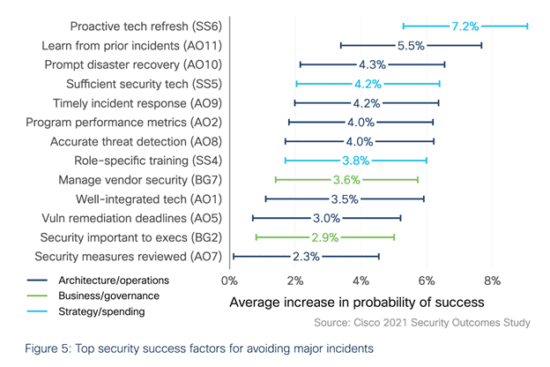
Learning from previous incidents increased organizations’ probability of success by 5.5%, while executing prompt disaster recovery and having sufficient security tech had a similar impact at 4.3% and 4.2%, respectively.
For more insights, check out Cisco’s Security Outcomes Study: Endpoint Edition here.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



