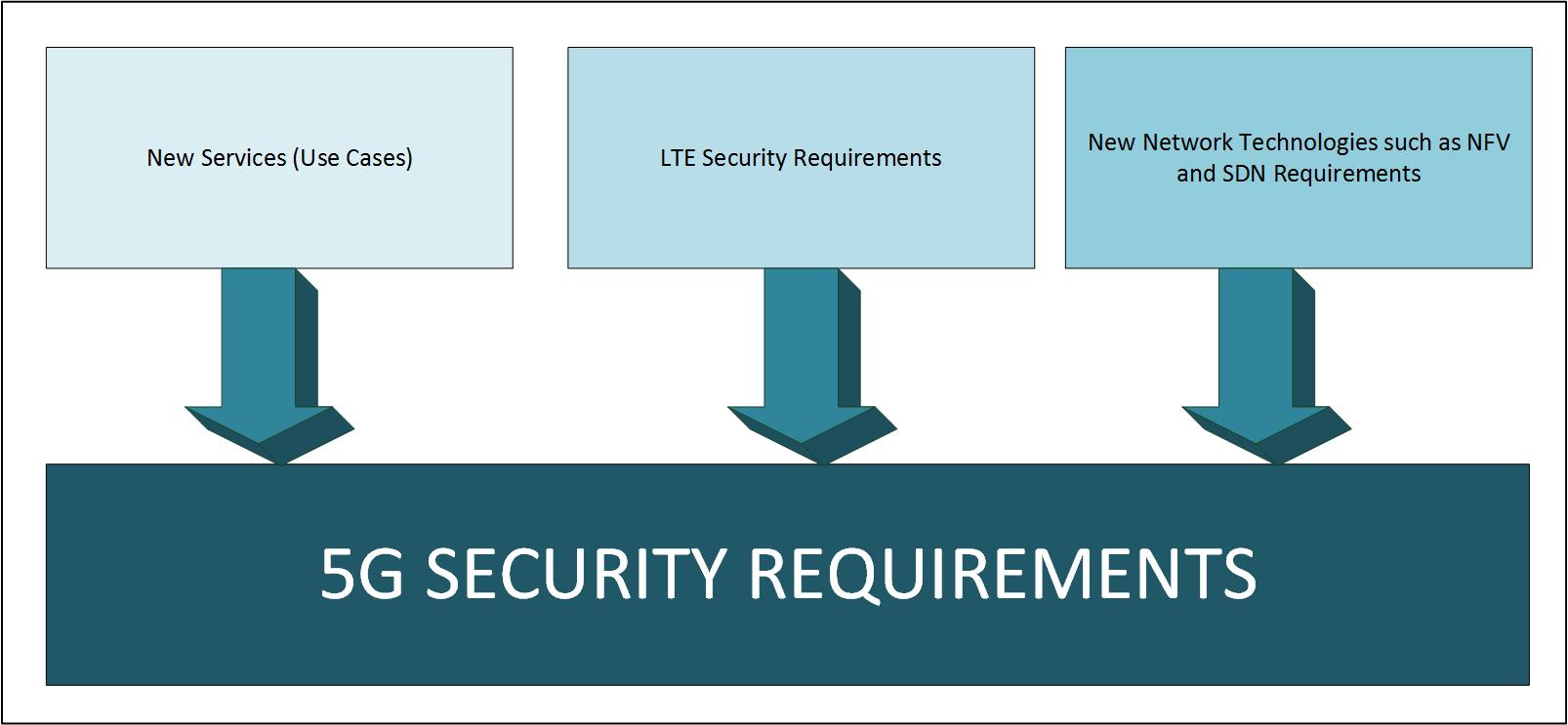
5G technology is the next step in the development of mobile communication. 5G will not only provide voice and data communication but also provide capabilities for new technologies such as Internet of Things. 5G is no longer confined to provide faster mobile services for voice and data communication but instead it will serve vertical industries, which will foster a new form of services. The new networking technologies such as such as Software Defined Network (SDN)/Network Functions Virtualisation (NFV) will further enhance the 5G capability to provide an effective platform for new services/businesses to flourish.
These new technologies also bring new threats. For example, NFV establishes virtualised networking environment dedicated to providing different network services and the security of data hosted in these virtualised environments largely depends on the degree of isolation between virtualised components. It always remains a challenge to provide a fully dependable secure NFV environment and hence next generation mobile networks should have security controls in place to address the vulnerabilities imposed by NFV environment. Similarly, SDN brings a new form of threats because of centralised software controller controlling network flows. Although these issues are not specific to 5G technology but 5G security framework should address these issues and provide a secure environment for next generation network.
The changing ecosystem is another driver for 5G security. In contrast to LTE network which is owned by a single network operator to provide network services to its customer, 5G networks will be composed of a number of stakeholders providing specialised services as illustrated in Figure below.
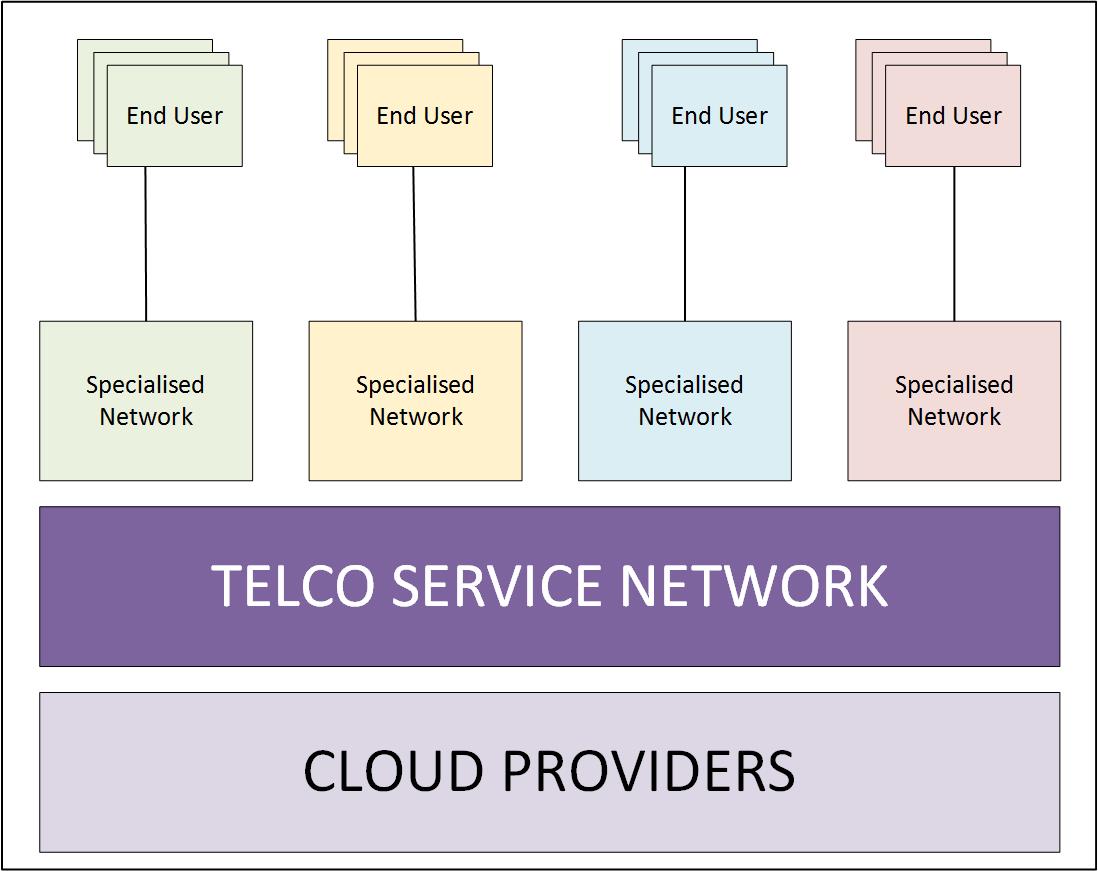
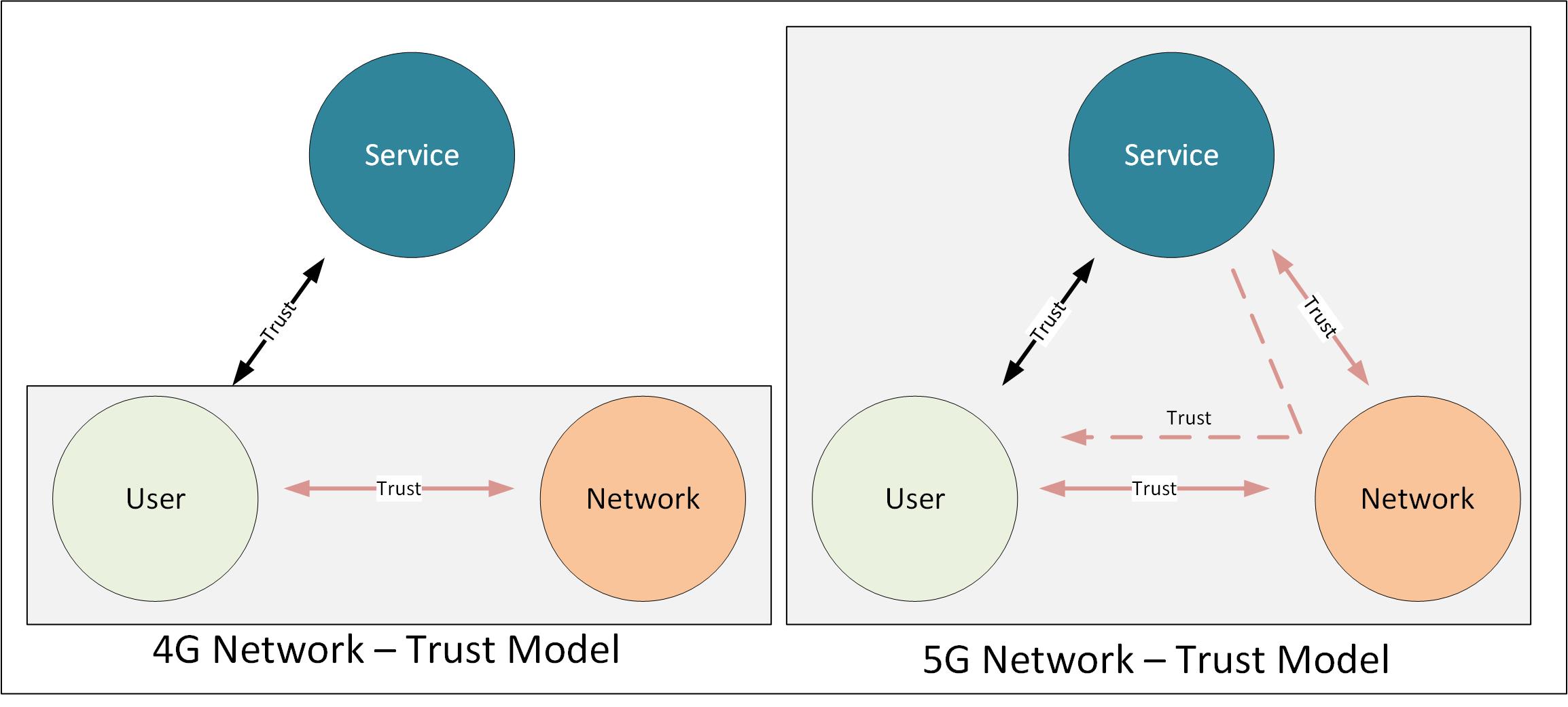
These specialised networks may provide network services cater for the specialised end users such as medical agency running a network to provide medical services for her customers. Today traditional network provides hop by hop security by provide secure communication path between the communicating parties which may not be efficient in 5G environment which requires end to end security to serve these new forms of specialised networks. These new specialised networks will result in new trust model for 5G networks with an additional element of services compared to traditional 4G trust model shown below [1].
The Next Generation Mobile Network (NGMN) alliance highlights the following security requirements in 5G Whitepaper:
- Strong Subscriber Authentication
- Must provide the security mechanism for protecting diverse range of information.
- Bearer-independent (e.g., higher layer) security (end to end security)
- Secure network design
- Resilience and High Availability to provide 99.999% network availability
- Reliability
5G Security Architect
The 5G network is still in early stage but the overall 5G mobile network is assumed to consist of number of clouds running network functionality as shown in Figure below [2].
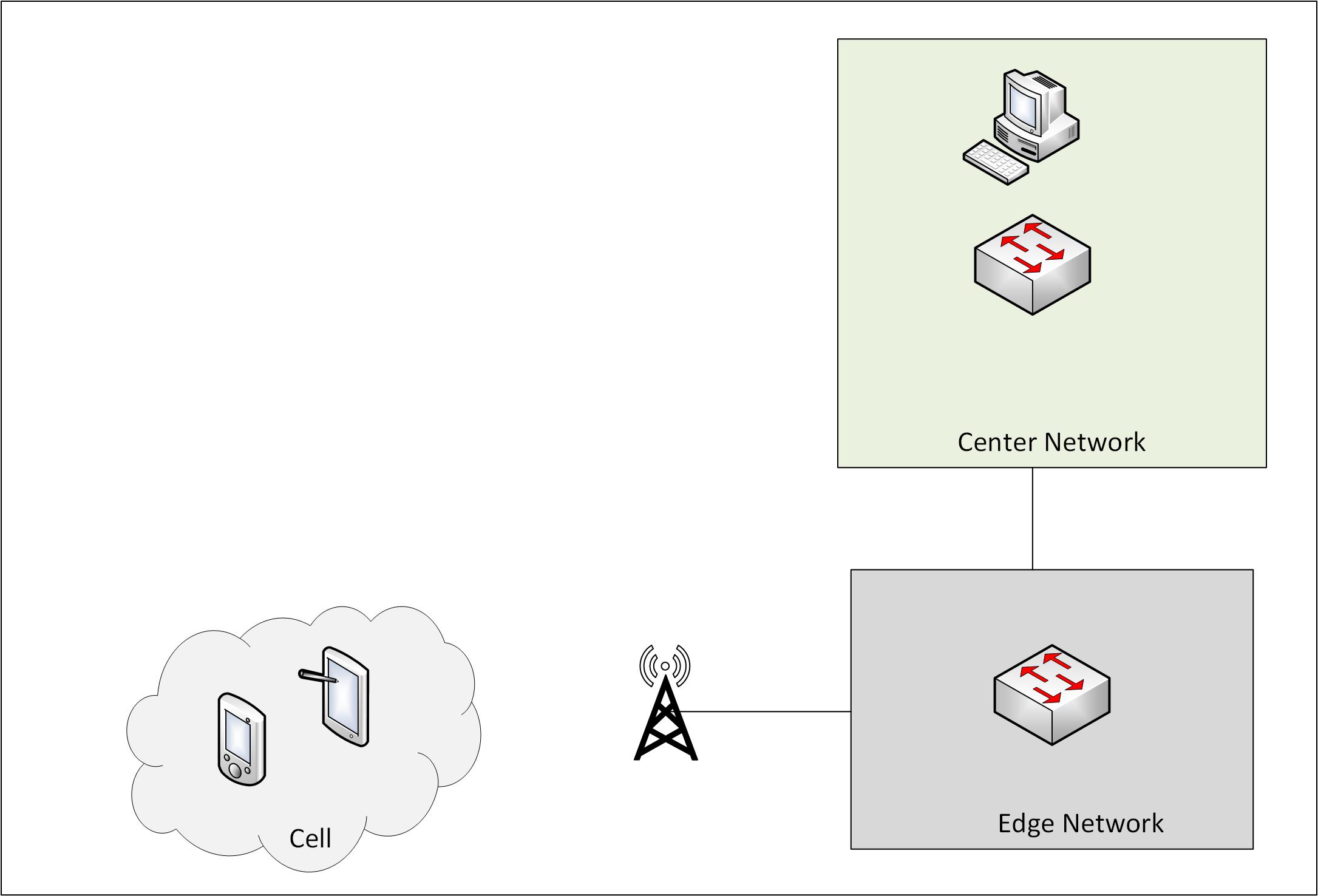
The components of security in 5G network are as follows:
- Security Between Mobile Devices and the Network
The first and foremost security requirements in this component is to identify the subscriber which may be mobile devices, sensors and other devices using 5G networks. The Universal Subscriber Identity Module (USIM) application running on SIM card may still be use in 5G network to identify the mobile devices. But other identification methods can be used to identify new services such as IoT devices. The confidentiality of the data is also an important security requirement which can be achieved by using existing security protocols such as IPSec or TLS or there is need to design new crypto algorithms as per specialised network.
- Telco Clouds
As discussed earlier, more network virtualization will be adopted in the Telco clouds and the security architecture must address the issues related to virtualisation such as to achieve high degree of isolation in shared virtualised environment. The availability of the network is also an important factor when designing such network and also network should have security controls in place to defend against both internal and external threats.
The most attractive targets for future attackers in the 5G networks will be:
- End user devices
- Access Networks
- Telco Core Networks
The possible threats and attack vectors should be evaluated for these components in order to design countermeasures to increase the security posture of the 5G network.
[1]
[2]
[su_box title=”About Dr. Muhammad Malik” style=”noise” box_color=”#336588″][short_info id=’100137′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.