A cybersecurity framework lays the foundation for your entire program and one of the keys for CISO to succeed. It not only helps CISO to streamline the cybersecurity activities but also helpful in communicating the state of cybersecurity to top management. But there is no black and white answer to which framework to choose.
HIGH-LEVEL CYBERSECURITY STRATEGY
Frank Kim, former CISO of the SANS Institute and currently leads the security management curricula for SANS, simplifies the approach to cybersecurity framework by dividing into three groups that organizations adapt in turns as they mature. Briefly, three groups are:
Control Frameworks: These are foundations of any security operations and it helps to develop an initial roadmap for the security program. Examples are:
o NIST 800-53: Complete list of controls but no one would ever implement them all.
o CIS Controls (CSC): The Center for Internet Security (CIS) defines the top 20 controls, which helps to prevent data breaches and mitigate the damage caused by most of the security attacks.
o ASD Mitigation Strategies: Australian Signal Directorate developed top mitigations (i.e., controls) strategies to help mitigate cybersecurity incidents caused by various cyber threats. These strategies are more granular than CIS controls.
Program Frameworks: These frameworks help cybersecurity professionals to build a comprehensive security program as it goes beyond specific controls to bring business requirements. These frameworks are often time-consuming and costly to implement. Examples are ISO 27001 and NIST Cybersecurity Framework (CSF).
Risk Frameworks: The risk framework mainly helps to prioritize the activities defined in control or program frameworks. It also helps CISO to assess and manage risk in a way that helps the business. Examples are: NIST 800-30, NIST RMF, ISO 27005, COSO ERM and quantitative approach like Factor Analysis of Information Risk (FAIR)
By dividing the cybersecurity framework into different groups will help CISO to define Cybersecurity strategy and plan the activities accordingly.
CIS CONTROLS
The 20 CIS controls will help us to define the initial cybersecurity strategy and roadmap, especially around which technologies to adopt. These controls are divided into three groups:
- Basic CIS Controls (1-6) are the starting point for any organization’s cybersecurity
- Foundational CIS Controls (7-16)
- Organizational CIS Controls (17-20)
In this article, I will discuss the strategies and roadmap to implement the CIS Control# 1: Inventory and control of hardware assets. The main goal of this control is to ensure only authorized devices are connected to the network.
CIS Control# 1: IMPLEMENTATION ROADMAP
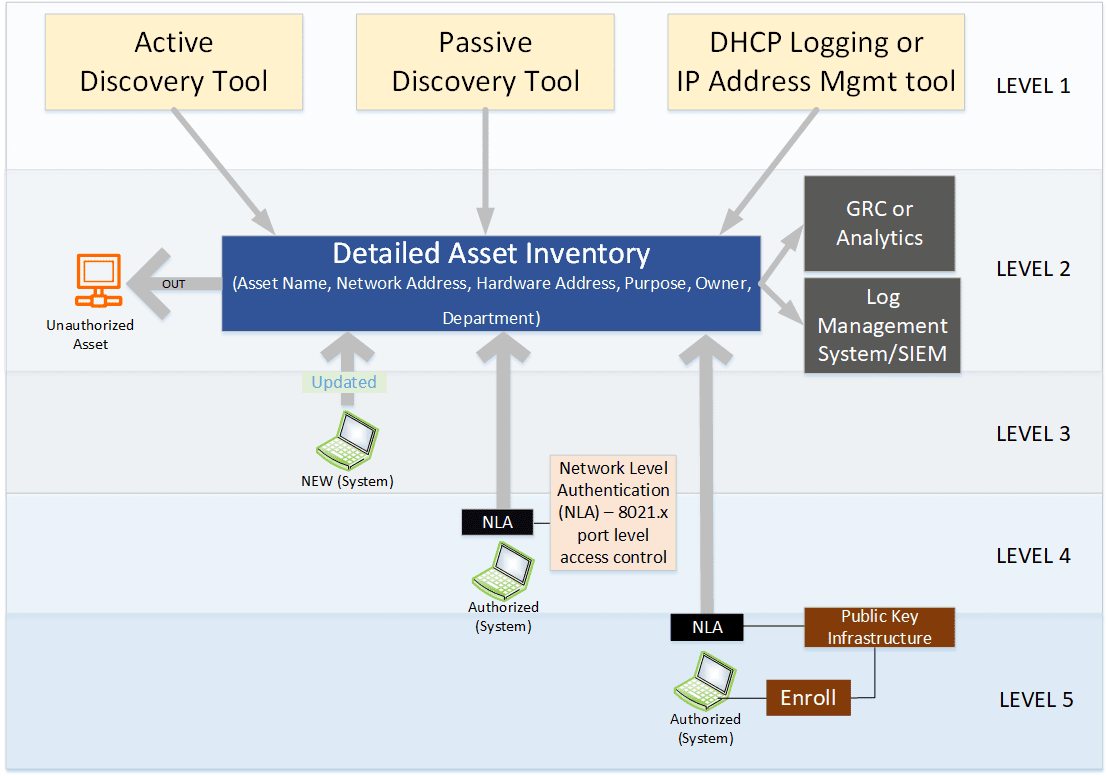
The figure below shows the roadmap illustrating the levels (1-5) to achieve as you progress the implementation of this control.
Level 1: Discovery
The first step is to discover what assets are in your network. The three main technologies can be used are:
Active Discovery Technology: The active discovery technology help to identify devices connected to the network and update the asset inventory accordingly. This technology utilizing an active process meaning it should have the ability to detect new assets as they connect to the network at any given time and report to the inventory system.
Passive Discovery Technology: In addition to active discovery technology, passive discovery tools sniff network traffic flowing through the network to identify the assets. This will help the organization to find the assets that the active discovery tool might miss.
DHCP Logging: The Dynamic Host Configuration Protocol (DHCP) logging on all DHCP servers can also be used to identify the assets connected to the network. IP address management is also another option to be used.
Level 2: Detailed Asset Inventory
The above discovery technologies or techniques can help us to create a detailed asset inventory. The asset inventory should be maintained on a continuous basis and should contain at a minimum the following information:
- Asset Name
- Network Address
- Hardware Address
- Purpose
- Owner
- Department
The asset inventory can be in the form of a spreadsheet for smaller organizations but it is preferable for large organizations to have an asset management database integrated with discovery technologies. The detailed asset inventory once populated can also help us to identify unauthorized assets in the network which should be removed.
Level 3: New and Decommissioned Assets
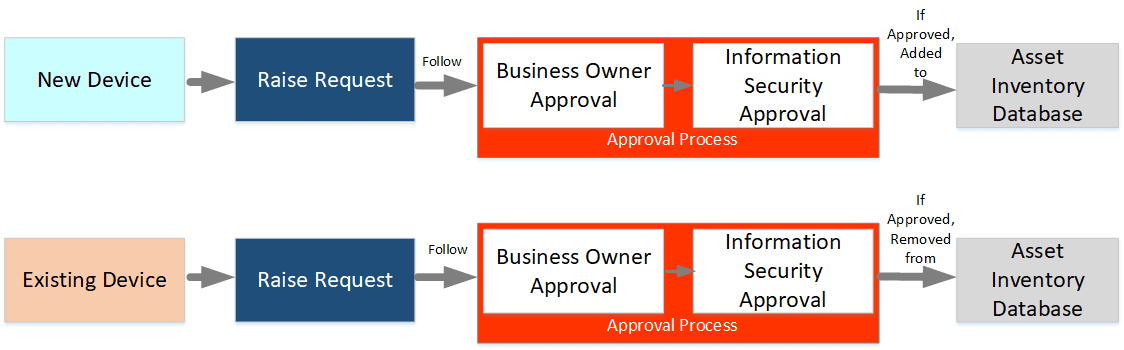
Once an initial asset inventory is developed, the job is to maintain it by developing processes to record new assets in the inventory before connecting to the network. Similarly, when the asset is decommissioned, it should be removed from the inventory as part of the decommissioning process. It is also recommended to store the inventory database offline for comparison purposes in case the online copy got corrupted or altered. The figure below shows the processes of adding and decommissioning an asset from the network which can be amended as per your need.
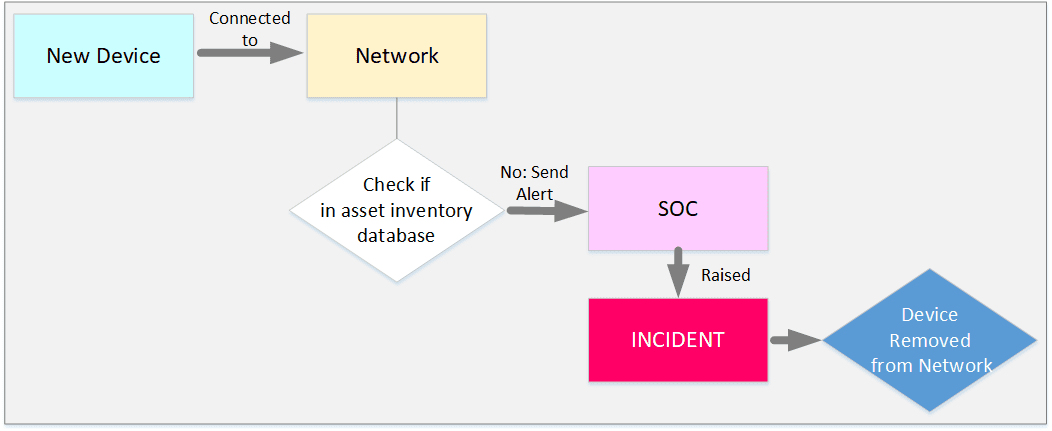
The inventory system should have the capability to send logs when there is a change in the inventory database. The security analyst or the engineer must regularly monitor the logs to ensure all events are properly responded to make sure only authorized assets are remain connected to the network.
Level 4 and 5: Network Level Authentication (NLA)
The above technology solutions (level 1 to 3) will help to detect an unauthorized asset connecting to the network but will not prevent the employee from plugging an infected personal computer into the network. Levels 4 and 5 of the roadmap will help to prevent unauthorized assets connecting to the network by deploying network-level authentication (NLA) solutions such as port-level access control, following 802.1x standards. This authentication can be tied to the hardware inventory database to make sure only authorized devices are allowed to connect to the network. This can be implemented in a number of ways depending on the technology map of the organization. For example, 802.1x can be integrated with Active Directory for machines that are part of the domain to authenticate the device (aka machine authentication) against the inventory database. MAC authentication can also be used for devices not part of the domain whereby the authentication is based on the device’s physical MAC address.
As the organization gets more mature in this control, utilize client certificates to authenticate hardware assets but it is very complex to implement. It requires Public Key Infrastructure (PKI) to be deployed and managed. The device needs to be enrolled for a certificate before allowing it to connect to the network.