The DDoS Environment
Before we look at how an attack affects you and everyone in your network, here’s a quick primer on what a DDoS attack is.
A typical brute force DDoS attack comes from a botnet – an enormous network of malware-infected devices, often numbering in the millions, that cyber criminals use to lock up your website. Many infected computers and mobile phones are unwitting components of a botnet as people browse the Internet unaware of enabling any malicious activity. This cycle perpetuates itself creating a self-sustaining chain of criminal activity.
At the center are the victims from whom the cyber criminal harvests data or leverages computing resources to conduct a DDoS attack.
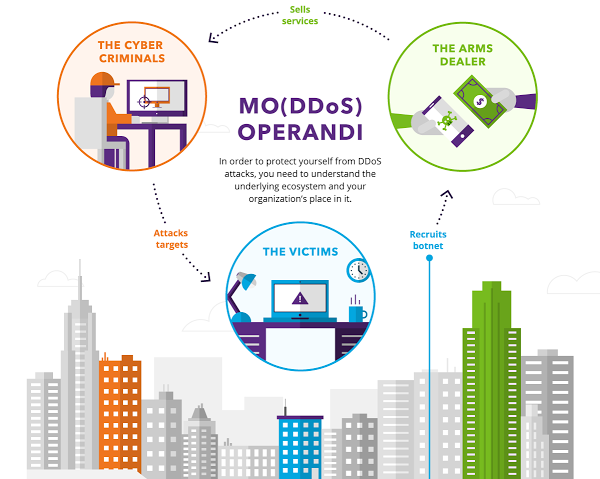
The Victims
High-profile DDoS attacks are in the news constantly, but the truth is that anyone with a public web presence (small or large) is a potential target, including:
- Large corporations
- Mid-sized corporations
- Small businesses
- Political entities
- Controversial leaders
- Online personalities
The Arms Dealers
We know the damage a botnet attack can cause. But who creates the traffic surge and how do they do it?
- The Kit Maker builds user-friendly toolkits that make botnets easily accessible.
- The Builder uses malware kits to build botnets for herders and booters.
- The Bot Herder controls botnets via remote command-and-control servers.
- The Booter sells botnets and toolkits under the guise of server stressers.
The Cyber Criminals
After the malware has been built and distributed, who uses it? And for what purpose? Here’s a short list of perpetrators:
- The Hacktivist expresses criticism to politicians, governments, or controversial persons or organizations
- The Intimidator threatens free speech and political discussions
- The Harasser bullies online users
- The Extortionist ransoms sites (take a tip from us: don’t give it to them)
- The Hired Gun makes a living out of DDoSing others
- The Script Kiddie thrives on the thrill of it or the rights to brag to their peers
Cybercrime and the Bottom Line
DDoS is serious business affecting e-commerce sites and corporate and online assets.
Even though DDoS attacks are often associated with large organizations, research shows that 51 percent of all companies (no matter the size) have experienced a distributed denial of service attack. And on average, all companies face nearly two successful cyberattacks per week.
Seventy percent of DDoS attack victims are targeted more than once. And surprisingly, 35 percent of all cybercrime comes from insiders like employees, contractors, and various business partners.
The Cost of Unlawful Entry
The fallout from a DDoS attack is substantial. The average cost to mitigate an attack is $408,292. In other words, it takes about 19 days (and over $21,000 per day) to resolve the problem. That’s a substantial amount of time, money, and energy.
To break it down even further, here’s a list of areas most financially impacted by a DDoS attack:
- IT: 35 percent
- Sales: 23 percent
- Security: 22 percent
- Customer service: 12 percent
[su_box title=”About Imperva®” style=”noise” box_color=”#336588″]