Today cyber-attacks are focusing increasingly on smartphones, as they are more and more accessible and used daily for both personal and business activities (BYOD). Smartphoneshave a variety of features such a web browsing, sending and receiving e-mail, instant messaging, media storage, social networks, online banking, and more. This brings new security risks for users’ privacy and the integrity of its communications and information.
Moreover, these devices remain connected to the Internet 24 hours a day, giving to attackers more time than PCs to plan and execute their malicious activities. Many apps use GPS to add location to your uploaded photos or publications. If intercepted, this information could be used against you to know your exact location instantly.
THE RISKS
As these devices have the same functions as a laptop or a desktop computer they also have the same risks related to internet and because its mobility some of them can be higher, depending of the situations.
Malware:
The first mobile virus was detected in 2004 targeting the Symbian OS, representing only the beginning of the mobile malware era. The increment of mobile malware took place when a new generation of smartphones running Android OS or iOS appears. Since the first detection of this kind of malware in late 2010, thousands of variants have been identified.
Mobile malware is designed to make money for its author, and just like the malware for Windows OS, it steals confidential information from their victims. Mobile malware can automatically makes calls or sends SMS without the user knowing. It will call to premium charge numbers or to chargeable SMS text services that are operated by the cybercriminals. For example, the Trojan Svpeng is able to steals SMS messages and information about voice calls, logins and passwords to online banking accounts, bank card information, and the new version is now capable of mobile phishing.
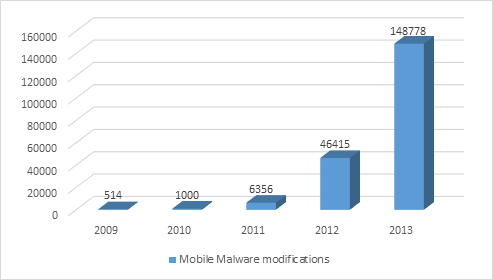
Malware modifications of malware targeting mobile devices. Source: Kaspersky
In all 2013 a total of 747 malware families and 148778 new modifications of malicious programs targeting mobile devices were detected.
Android Operating System stills the main target of malicious attacks of all the malware detected in 2013 (98.05 %), proving the vulnerability of its architecture and also a certain lack of control by Google Play Store on allowed apps.
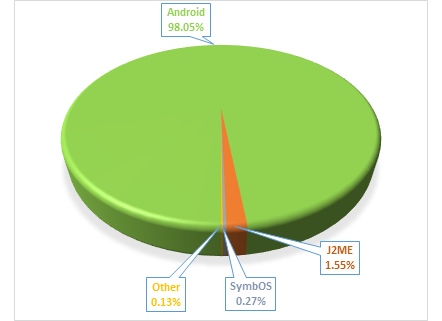
The distribution of mobile malware detected in 2013 by platform. Source: securelist.com
Infection Vectors:
• App Stores: Attackers develop applications including camouflaged malicious functionalities like Trojans or they download legitimate applications and inject them malware and then upload them in the official or third-party App Store, which do not control securely the software it authorizes.
• Self-replication: Malware is able to self-replicate by sending SMS or emails containing a malicious link to the victim’s contacts.
• Infected Web sites: Many consumers use their Smartphones to surf web pages without being aware that these resources can be infected and infect them too.
Theft of Confidential information by Shoulder Surfing:
In public places anyone could try to spy you and steal the displayed information on your screen, or the keys you typed in, like passwords. Beware of shoulder surfing attacks.
Theft of confidential information stored in the smartphone’s memory:
Be careful of being robbed or lose your device, if it contains unencrypted sensitive data anyone can access to it.
Theft of confidential information transmitted on wireless networks:
If you connect to a public wireless network (airport, university, hotel, etc.) a malicious person can intercept sensitive information transmitted during a connection, with your bank for example. It’s very important to verify if it is a secure connection (HTTPS or VPN).
SECURITY TIPS:
1) Password-protect your Smartphone:
Protecting your Smartphone with a strong password or pattern is one of the simplest ways to strengthen the access security of your Smartphone, but many people do not use it. Do not forget to set it to block automatically after 2-5 minutes of inactivity.
2) Install security solutions:
There are many free and paid security solutions available for Smartphones nowadays: Antimalware, AntiSpam, and Firewall. Don’t forget to update their databases regularly.
3) Download applications only from trusted and reliable sources:
Official App Stores monitor and verify the security of submitted applications before publishing them. Never install an application from an unknown App Store.
4) Check your apps permissions and rights:
Many applications ask for more permissions than needed. Be careful with those requirements, for example, a simple clock application that requires access to your contacts, GPS or internet access, does it really need it?
5) Keep the operating system up to date:
It is very important to perform regular updates of the O.S on your device, they contain last security patches.
6) Beware of links in emails or SMS:
Never open links included in emails or SMS from unknown sources, they could redirect you to phishing websites requesting for personal information or infect your device with malware.
7) Back up your information:
Don’t forget to back up your information frequently, like your contacts, photos, videos, audios, etc.., you may lose everything in the event of loss, theft or malware infection.
8) Encrypt your confidential information:
In our day, many people store sensitive information in the Smartphone memory, both personal and business. Encrypting it prevents any malicious person to access your information in case of theft, loss or malware infection.
9) Beware of Shoulder Surfing:
Be careful when you are entering sensitive information on your smartphone, such banking credentials, because you could be spied by people around you.
10) Avoid jailbraking or rooting of the device:
Even if jailbraking or rooting your smartphone allows you to get the full access of your smartphone OS it also opens a security hole, letting the malware get full access to the stored information without asking the user authorization.
Frédéric Fraces, Security Consultant, Enfocus,
 I am a Security Consultant and Researcher at Enfocus, a company located in Bogota, Colombia. In the Security world I conduct PenTests on ATMs, Web Apps, Smartphones and anything with an IP address. I work mostly with Banking and Government agencies. I am also ISO 27001 Internal Auditor.
I am a Security Consultant and Researcher at Enfocus, a company located in Bogota, Colombia. In the Security world I conduct PenTests on ATMs, Web Apps, Smartphones and anything with an IP address. I work mostly with Banking and Government agencies. I am also ISO 27001 Internal Auditor.
With Enfocus, I started a research project named “StatusCo” which focuses on identifying and analyzing vulnerabilities affecting the technological resources connected to Internet in Colombia and propose possible solutions in order to prevent Cyber Attacks. I am the author of the Blog Ryu Security
Follow Frédéric on Twitter here: @FredFraces
[wp_ad_camp_4]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



