As business leaders become more ‘cyber aware’ concerns over data security shift from awareness to action. Organisations around the globe are increasing security spending, but have they prioritised budgets correctly or are they just throwing money at the problem?
There are many opportunities and benefits provided by doing business in a hyper-connected word but they come with risks. I read a report by the World Economic Forum recently that draws some interesting conclusions about information security practices and risk budgets.
Increasing threats
High profile security breaches, data loss and hackings hit headlines on a regular basis. We are doing business in world where a large organisation can be targeted by 10,000 attacks a day and the resulting costs are growing. Cyber Risk is a global priority and both large and small organisations are encouraged to act now.
Are we doing enough?
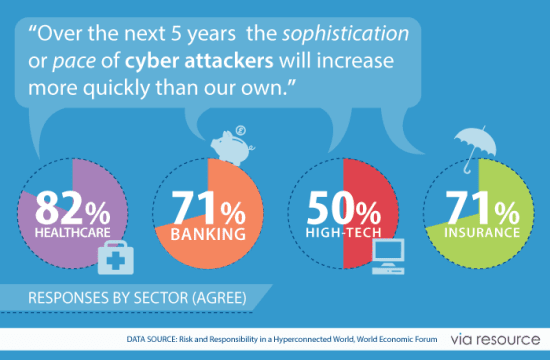
CIO’s, CISOs and other C-Level experts were asked if they felt their businesses were doing enough to defend themselves – the answer was not reassuring. 69% foresaw that the pace and sophistication of cyber threats would escalate faster than our ability to defend against it.
“We just don’t have the resources to counter what is next,” commented a CISO from the Healthcare sector.
The cost of cyber fear
 Information Security is no longer a topic discussed not just by the InfoSec pros, but non-technical executives and the board as well as the UK Government.
Information Security is no longer a topic discussed not just by the InfoSec pros, but non-technical executives and the board as well as the UK Government.
People can jump to worst-case, doomsday scenarios, and impending ‘cybergeddon’ when talking about InfoSec, but even a small breach can cause significant repercussions for a business in terms of information, opportunities and lost trust. Senior leaders are more aware than ever of the risks.
This apprehension over risk could be holding back technological innovation, such as adoption of cloud and byod. 78% of those questioned claimed that security concerns had delayed adoption of public cloud by at least a year.
In contrast some are alarmingly choosing to ignore the threats and risk it. “Concerns about cyber resilience are not delaying adoption of most technologies… Most devices have no security application on them at all,” another Healthcare CISO comments, “Anyone can just get in and manipulate whatever they want.”
Blind budgets – Are we spending wisely?
In general, most believed that their security budgets were too low, though executives from banking and high-tech industries felt they were spending enough.
However, is this proving effective or counterproductive? The report suggests that some large organisations were “throwing money at the problem” without understanding their security priorities – bigger budgets did not guarantee better defences.
“Large institutions lack the facts and processes to make and implement effective decisions about cyber resilience…Most don’t systematically understand which information assets need to be protected, who their attackers are, what is their risk appetite or which is the most effective set of defence mechanisms.”
Current defences built around reactive ‘audit’ and ‘compliance’ models are too fragmented, the report concludes. To succeed businesses are encouraged to abandon these for a model based on a business driven, risk management approach.
To build robust resilience against both ‘real world’ and ‘virtual’ threats we need to strengthen information sharing practices, critical infrastructure and policy development.
Amongst a list of recommendations, businesses are encouraged to enlist front line personnel to offer insight into the information assets they need protected and how to assign security priorities.
For a full list of recommendations for governments, business and international organisation read the full report Risk and Responsibility in a Hyper-connected World 2014 pdf
Read this report? Do you agree? Let us know your opinion in the comments section below.
Tor Macleod, Director at Via Resource
Tor is Director and Founder of the information security recruitment consultancy Via Resource Group. He writes about InfoSec, security trends and IT Security careers. You can follow him on Twitter @ViaResource or read his security blog.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



