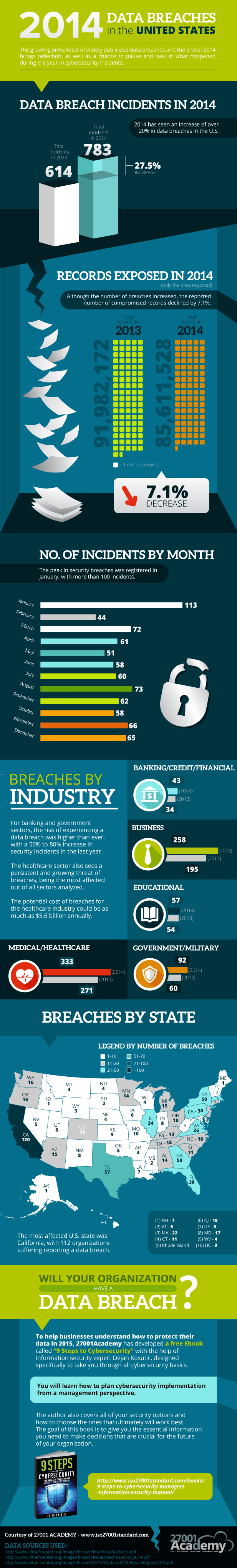
The growing prevalence of widely publicized data breaches and the end of 2014 brings reflection as well as a chance to pause and look at what happened during the “Year of the Breach.”
27001 Academy, the largest online learning center where you can get training and documentation for implementing the international standard for information security management, ISO 27001, has created an infographic showing the state of data breaches in 2014.
Free eBook: Modern Retail Security Risk – Get your copy now.
Here are some stats:
2014 has seen an increase of over 27.5% in data breaches in the U.S.
Total incidents in 2014: 783
Total incidents in 2013: 614
2014 vs. 2013: 27.5% increase
Although the number of breaches increased, the reported number of compromised records declined by 7.1%.
Total records in 2014: 85,611,528
Total records in 2013: 91,982,172
2014 vs. 2013: 7.1% decrease
The peak in security breaches was registered in January, with more than 100 incidents.
Check out the infographic for additional findings.
Will your organization have a data breach?
To help businesses understand how to protect their data in 2015, 27001 Academy has developed a free eBook called “9 Steps to Cybersecurity” with the help of information security expert Dejan Kosutic, designed specifically to take you through all cybersecurity basics.
You will learn how to plan cybersecurity implementation from a management perspective.
The author also covers all of your security options and how to choose the ones that ultimately will work best. The goal of this book is to give you the essential information you need to make decisions that are crucial for the future of your organization.
27001 Academy is the largest online learning center where you can get training and documentation for implementing ISO 27001.
The Academy helps companies of any size implement ISO 27001 and ISO 22301 standards by themselves and reduce the implementation time by 50%.
Free consultations are available.
About 27001 Academy
![]() 27001 Academy is one of the projects of EPPS Services Ltd. EPPS operates several websites that specialize in helping organizations implement top international standards and frameworks, like ISO and ITIL. Over the years, EPPS has become a global leader in the provision of web-based training and documentation for ISO 27001 (information security management) and ISO 22301 (business continuity management). Our products are of the highest quality, and have been implemented in over 45 countries. Combined with our best-in-class customer service, success is inevitable.
27001 Academy is one of the projects of EPPS Services Ltd. EPPS operates several websites that specialize in helping organizations implement top international standards and frameworks, like ISO and ITIL. Over the years, EPPS has become a global leader in the provision of web-based training and documentation for ISO 27001 (information security management) and ISO 22301 (business continuity management). Our products are of the highest quality, and have been implemented in over 45 countries. Combined with our best-in-class customer service, success is inevitable.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.