When each nation’s best athletes compete at the Olympic Games, one city seemingly becomes the center of the universe. And while the world looks on closely, threat actors do the same—only for much more nefarious reasons.
Every four years, the Olympics’ host country pours an enormous amount of time and resources into building the physical and technical infrastructure necessary to accommodate visitors from all over the world. For example, the total cost of the 2016 Olympics in Rio de Janeiro, Brazil, is estimated to exceed $12B, an increase by $99.3M since August alone.
Spectators and revelers are projected to spend millions on tickets, travel, and accommodations while sponsors such as Coca-Cola, McDonald’s, and Nike have earmarked hundreds of millions for sponsorships to keep their name top of mind during the world’s biggest sporting event. But all the spend associated with the Olympics makes for easy and profitable work for threat actors looking to separate people and organizations from their money. That’s why it’s unsurprising that RiskIQ, an external threat intelligence and detection company, is seeing a sharp rise in fraudulent sites and mobile apps related to the Rio Olympics.
Fraudulent Sites
Ticketing scams using fake websites is a common way that Olympics-goers end up ticketless and several hundred dollars in the hole. Fake sites target a specific organization by using one of the following methods:
- The name of the company in the domain (log-in-page-companyname.com)
- A variation of the brand’s spelling (favebook.com)
- The organization name paired with an uncommon top-level-domain (TLD) (companyname.net, companyname.de, companyname.party, etc.).
Threat actors often use hundreds, if not thousands of variations across different domain variations to maximize their reach. The shady domains can resolve or redirect to hosts aimed at exploiting visitors.
In the fake site below (which RiskIQ found and blacklisted), the brand is the Olympic Games itself. The URL resolves to a site selling fake tickets—even to known sold-out events like the Opening Ceremony. Victims of this scam get nothing more than a fake ticket, without recourse.
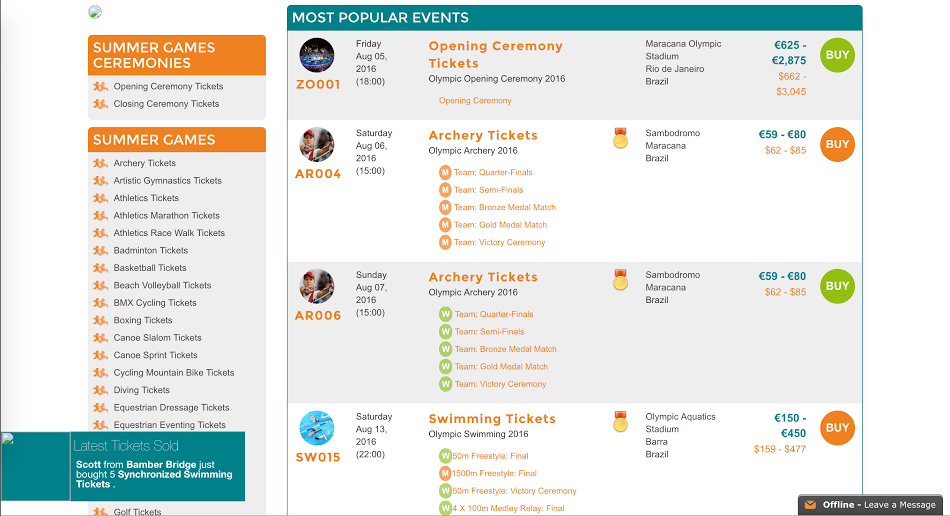
Although many of these fake ticketing sites are crudely built with telltale typos and other errors—such as this notorious one that scammed English soccer fans out of nearly $500,000—some are more difficult to detect. Screenshots of pages above and below are particularly dangerous due to how professional they look.
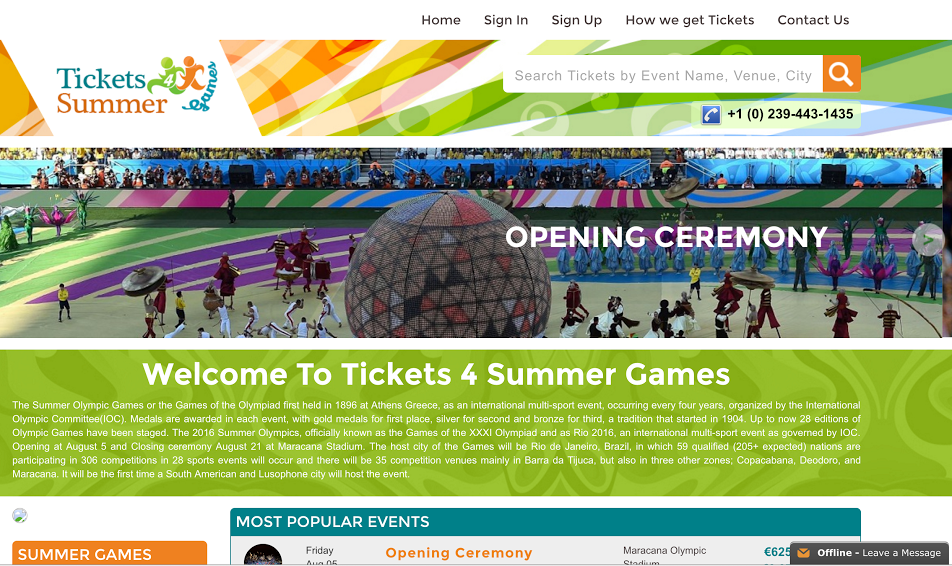
RiskIQ has also observed fake websites that promise an “inside look” at the Rio Olympics in exchange for the user’s personal information. Other viable scam use fake travel booking sites that steal financial data and sites that exploit the concern over the Zika epidemic by offering fake safety information and delivering malware to users.
Mobile Apps
Using the immense size and dynamic nature of the global app store ecosystem against them, threat actors are exploiting well-known Olympic Games sponsors. It’s complex environment makes monitoring a sponsoring organization’s mobile presence increasingly difficult, making it more challenging to protect their customers. Threat actors take advantage of this lack of visibility by major sponsors by creating several—if not hundreds—of apps that mimic the original, offering games or other interactive experiences in exchange for users’ financial data and other sensitive information. Shady developers know users are conditioned to grant app permissions to gain access to the content and are happy to take advantage of this social conditioning.
Fake mobile apps with promotional tie-ins and sponsorships for the 2016 Games have been found in app stores globally, tricking more users every day. This deceit degrades consumers’ trust in the organization, compromising the very goal of the sponsorship. Once published, mobile apps can rapidly proliferate from official stores throughout the app store ecosystem, spreading to new stores and web download locations without the developer’s knowledge or consent.
Even legitimate apps can be compromised, especially if they are not actively maintained and updated. Every major sporting event, from the Super Bowl to the Olympics to the World Cup, leaves digital detritus, a graveyard of event-specific apps in its wake after the events’ sponsors have moved on to the next opportunity. Opportunistic threat actors find and eventually compromise these apps to exploit them at the organization’s expense.
Protect Yourself
A company’s security perimeter is only as strong as its employees’ security practices. Infected personal devices like mobile phones and laptops are a common way in for malware. Companies with remote employees traveling to the Olympics must think about security beyond the firewall and take the necessary precautions to avoid the pitfalls mentioned above.
Companies cannot leave it up to employees to protect their devices. Increasingly sophisticated threat actors have the tools and know-how to take advantage of people, wreak havoc on their employers, and eventually steal the organization’s data. The best way to defend against the growing threat outside the firewall is to discover and monitor your entire attack surface so you can quickly investigate any threats for rapid response.
[su_box title=”About Arian Evans” style=”noise” box_color=”#336588″][short_info id=’84046′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



