Today, cybercriminals launched a highly effective email scam that included a link to a Google Docs document that was in fact a link to a 3rd party app designed to steal information from the recipient. Worse, the email appears to come from someone known to the victim. Based on information from the Agari Trust Network, we saw more than 3,016 organizations compromised that sent 23,838 emails to Agari protected organizations. Based on social media posts and the number of Gmail/G-Suite users, the number of victims is likely unprecedented.

When users click on the Google doc link, the malicious site uses a Google API to prompt the user to give the attackers’ malicious app access to their email account, supposedly to access the document. When users allow access, the malicious app sends the same email to your contacts, spreading itself.
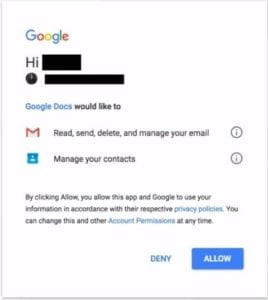
What Should You Do If You Clicked on The Link?
For individual Gmail users:
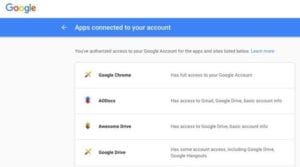
Go to your Google security setting at https://myaccount.google.com/permissions and remove any apps connected to your account that you don’t recognize. The malicious app was originally called “Google Docs”.
For G-Suite administrators at organizations:
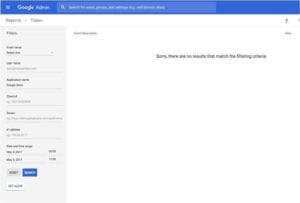
Go to the Google Admin page. You can go to reports>token and run a search for any apps installed on May 3rd and revoke that app. Unfortunately, you have to do this one user at a time if you use the Google admin interface but at least you can filter by the users who installed something on May 3rd. Alternatively, you could also use a command line tool like this one if you have a large number of users https://github.com/jay0lee/GAM/wiki/SecurityExamples
What’s Different About This Attack?
This attack is different and scary because of its ability to evade common defenses and leverage Google APIs to trick users into granting access. The attack didn’t directly try to steal usernames and passwords like a typical phishing scam but rather tricked users into allowing complete access to their email account. Typically, users have been trained to change their password when they think they have been a victim of a phishing scam. In this case, that would not solve the problem.
What could these Cybercriminals do with this access?
While we haven’t seen reports of fraud yet, the cybercriminals who launched the attack have access to all of the victims’ emails until the app is disabled. With that access, the criminals can use your identity to scam co-workers or relatives, reset your bank account password and steal money or harvest information to steal the victim’s identity. There are an infinite number of ways a cybercriminal can monetize this kind of access.
Why Didn’t Traditional Defenses Didn’t Stop This Attack?
- Two-Factor Authentication – Gmail and Gsuite have integrated two factor authentication. This attack didn’t steal a password. If you change your password, you are still vulnerable.
- Endpoint Security– There is no malware to detect or block using anti-virus or other endpoint security techniques.
- Secure Email Gateways– The URL used for the link had never been seen before and was an actual Google doc with a strong reputation.
- Email Authentication– This attack came from an authentic email account. It wasn’t spoofing and therefore wouldn’t fail email authentication.
Predictions About Future Attacks
This is likely the first of a new breed of attack. Next time, the attacker might be smarter and only mine the information while propagating slowly enough not to get caught the same day. Other email systems such as Office 365 have similar app plugin systems that could be used to mount similar attacks on larger enterprise organizations. I also believe we will see an increase in targeting to make attacks more credible; whether using account takeover (ATO), social networks, or just publicly available information. As a result, more emails will look “right” to the victim and fewer malicious emails will be reported. This will hamper traditional blacklisting-based methods, which depend on reporting.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



