Following the News that hospitals across England have been hit by a large scale cyber-attack. Hospitals across the country appear to have been simultaneously hit by a bug in their IT systems, leading to many diverting emergency patients, IT security experts from SQS, Synopsys, Recorded Future, Ivanti, Wombat Security, Splunk, Vectra Networks, CFC Underwriting, Thales e-Security, Rubrik, Anomali, Bromium, GCHQ Cyber and Intelligence, Kaspersky Lab, Avast, SailPoint, Lastline, Cyberis, Imperva, Tripwire, Firemon, AlienVault, Tenable Network Security, Comparitech.com, Censornet, Infoblox, Synchronoss, BMC Software, Maintel, Varonis, RES, F5 Networks, CrowdStrike, Lieberman Software and Digital Defense, Inc. provide an insight on the attack below.
It is said that 24 NHS organisations have been hit. The full list is below:
- Mid Essex Clinical Commissioning Group
- Wingate Medical Centre
- NHS Liverpool Community Health NHS Trust
- East Lancashire Hospitals NHS Trust
- George Eliot Hospital NHS Trust in Nuneaton, Warwickshire
- Blackpool Teaching Hospitals NHS Trust
- St Barts Health NHS Trust
- Derbyshire Community Health Services
- East and North Hertfordshire Clinical Commissioning Group
- East and North Hertfordshire Hospitals NHS Trust
- Sherwood Forest NHS Trust
- Nottinghamshire Healthcare
- Burton Hospitals NHS Foundation Trust
- United Lincolnshire Hospitals NHS Trust
- Colchester General Hospital
- Cheshire and Wirral Partnership NHS Foundation Trust
- Northern Lincolnshire and Goole NHS Foundation Trust
- North Staffordshire Combined Healthcare NHS Trust
- Cumbria Partnership NHS Foundation Trust
- Morecombe Bay NHS Trust
- University Hospitals of North Midlands NHS Trust
- NHS Hampshire Hospitals
- Kent Community Health NHS Foundation Trust
- Plymouth Hospitals NHS Trust
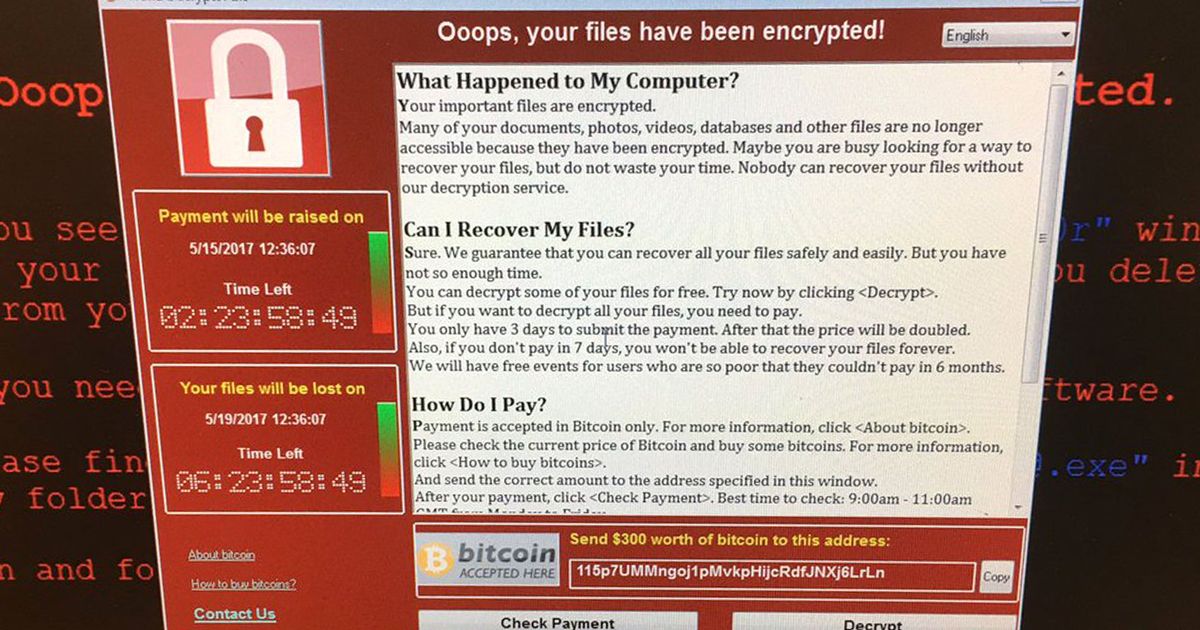
The ransomware message affecting NHS IT systems is below:
Kevin Cunningham, President and Founder at SailPoint:
 “While we don’t yet know if patient data was affected in the NHS cyberattack, the risk is clear and present.
“While we don’t yet know if patient data was affected in the NHS cyberattack, the risk is clear and present.
“As cyber-attacks continue to become harder and harder to prevent as cybercriminals are ever more sophisticated, organisations of all kinds need to prepare for the worst-case scenario.
“Shore up your cybersecurity strategy by protecting identities and credentials. This has become such an easy inroad for attackers today – breach just one person’s user credentials and an attacker has just walked through your now-unlocked front door.
“The combination of strong identity governance controls, especially in the area of access to unstructured data like files and documents (which is where ransomware is generally targeted) when combined with the ability to detect and respond to behavioral anomalies in real-time is a key to stopping a breach before it gets out of control.”
Mike Ahmadi, Global Director – Critical Systems Security at Synopsys:
 “Ransomware has proven itself to be a very viable and profitable business model for cyber criminals to engage in, and it will get much worse before it gets better. Hospitals are currently hosting scores of devices and applications heavily polluted with thousands of known vulnerabilities, and current regulations simply do little or nothing to stop this from happening.”
“Ransomware has proven itself to be a very viable and profitable business model for cyber criminals to engage in, and it will get much worse before it gets better. Hospitals are currently hosting scores of devices and applications heavily polluted with thousands of known vulnerabilities, and current regulations simply do little or nothing to stop this from happening.”
Allan Liska, Senior Solutions Architect at Recorded Future:
 “The ransomware infection that is spreading throughout the United Kingdom, and the world, is version 2.0 of WanaCypt0r (aka WCry, WannaCry, and WannaCryptor). Recorded Future saw the first appearance of this ransomware on March 31st, but the version that is rapidly spreading has made some significant changes.
“The ransomware infection that is spreading throughout the United Kingdom, and the world, is version 2.0 of WanaCypt0r (aka WCry, WannaCry, and WannaCryptor). Recorded Future saw the first appearance of this ransomware on March 31st, but the version that is rapidly spreading has made some significant changes.
Specifically, the new version takes advantage of the SMB vulnerability outlined in Microsoft Security Bulletin (MS17-010), also known as the EternalBlue exploit. This means that once the ransomware gets into a network it can spread quickly through any computers that do not have that patch applied. The worm-like capabilities are the new feature added to this ransomware.
The attacks that have taken place do not appear to be targeted attacks, instead they appear to be part of a phishing campaign, though that has not been fully confirmed. Infections of the new version of WanaCypt0r started in Spain earlier today, but have since spread to the United Kingdom, Russia, Japan, Taiwan, the United States and many more.
Given the relative ineffectiveness of the first version of WanaCypt0r, it is likely the author did not expect this type of success from the new campaign, which could cause problems for any organisation that attempts to pay the ransom. For now, the best advice is to ensure that all Windows systems are fully patched, to ensure that firewalls are blocking access to SMB and RDP ports, and to educate users to watch out for suspicious emails.”
Phil Richards, CISO at Ivanti:
 “This appears to be a variant of WanaDecryptor which is a relatively new strain of ransomware. This particular ransomware is correctly identified and blocked by 30% of the AV vendors using current virus definitions. It is correctly handled by both Kaspersky and BitDefender.. There is no public decryption (crack code) available at present. This malware modifies files in the /Windows and /windows/system32 directories and enumerates other users on the network to infect. Both of these actions require administrative privileges.
“This appears to be a variant of WanaDecryptor which is a relatively new strain of ransomware. This particular ransomware is correctly identified and blocked by 30% of the AV vendors using current virus definitions. It is correctly handled by both Kaspersky and BitDefender.. There is no public decryption (crack code) available at present. This malware modifies files in the /Windows and /windows/system32 directories and enumerates other users on the network to infect. Both of these actions require administrative privileges.
Methods to combat this particular ransomware:
- This ransomware attacks through phishing or other social engineering email. Train staff to not click on unknown or malicious email.
- Run Antivirus software such as Kaspersky or BitDefender on all endpoints and make sure the virus definitions are up to date. If your virus definitions are 1 week out of date, it would not recognize this particular ransomware.
- Run ApplicationControl to restrict administrative privileges. This malware would not be as successful if it did not have access to admin privileges.
Joe Ferrara, President and CEO at Wombat Security:
 “Hackers are interested in valuable data, and today healthcare records are some of the most valuable. Ponemon Institute estimates data breaches cost the healthcare industry $6.2 billion last year. And as we’ve recently seen, when the healthcare industry is hit with a data breach or ransomware attack it presents a huge risk to the delivery of care and patient data. The healthcare industry faces distinct challenges in their environment. It’s key for a training program to work in harmony with busy, irregular, unpredictable schedules. Training staff empowers them to be the first line of defense in cyber security. The best way to arm the healthcare industry is with the right training and tools that works with their schedule to avoid these kind of attacks in the future.”
“Hackers are interested in valuable data, and today healthcare records are some of the most valuable. Ponemon Institute estimates data breaches cost the healthcare industry $6.2 billion last year. And as we’ve recently seen, when the healthcare industry is hit with a data breach or ransomware attack it presents a huge risk to the delivery of care and patient data. The healthcare industry faces distinct challenges in their environment. It’s key for a training program to work in harmony with busy, irregular, unpredictable schedules. Training staff empowers them to be the first line of defense in cyber security. The best way to arm the healthcare industry is with the right training and tools that works with their schedule to avoid these kind of attacks in the future.”
Rich Barger, Director of Threat Research at Splunk:

- This event should serve as a global wakeup call – the means of delivery and the delivered effect is unprecedented.
- The WCry/WannaCry ransomware strain has how hit 11 countries in just three hours- researchers are scrambling to look for Patient Zero. While Spain and Russia look to be hit the hardest, other countries including Italy, Portugal, Ukraine and Pakistan look to be affected as well. This is one of the largest global ransomware attacks the cyber community has ever seen.
- Initial reports that this malware is propagating on its own – for those who remember the early 2000’s this is a worm (malware that infects a machine and then looks for other vulnerable hosts on the same network or randomly scans and looks for other vulnerable hosts to infect).
- This ransomware attack is causing ripples much further than financial gain. With their IT systems at a complete shutdown, a number of hospitals all over London are said to be turning away ambulances as they’re not confident they can care for patients. Hospitals are understood to have lost the use of phone lines and computers, with some diverting all but emergency patients elsewhere.
- Ransomware is arguably the #1 method of cyber attack in 2017, and this attack demonstrates the paramount need for critical enterprises to have a ransomware playbook in place for when they are attacked. Protecting critical infrastructure from cyber attack is a responsibility that cannot be taken lightly.
- One thing is for sure – somebody is going to get very rich, or spend a very long amount of time in jail.
Possible Mitigations:
- Organizations should consider compartmentalizing & self-containing, until they can report 100% patching compliance. Imagine your network like a submarine.
- Consider disabling or blocking the SMB v1 service
- Consider monitoring for and or mitigating scan behavior on TCP/445, externally and internally.
Gérard Bauer, Vice President EMEA at Vectra Networks:
 “This is not the first time the NHS has been the target of ransomware. Just last October a major attack hit Northern Lincolnshire and Goole NHS Foundation Trust, causing it to cancel operations and other activities. However, today’s appears to be the most serious and successful attack yet on the UK’s health infrastructure.
“This is not the first time the NHS has been the target of ransomware. Just last October a major attack hit Northern Lincolnshire and Goole NHS Foundation Trust, causing it to cancel operations and other activities. However, today’s appears to be the most serious and successful attack yet on the UK’s health infrastructure.
“Add to this that Telefonica, a major telecoms, mobile and broadband provider with operations in Europe as well as South America, appears to have been hit with the same brand of ransomware. It raises serious concerns about whether this is a targeted (and contained) attack on infrastructure, or a ransomware variant that is loose in the wild and starting to propagate indiscriminately like CryptoLocker did in 2013. If it’s the latter, we could yet see more instances further afield as the day progresses in other major markets such as the US.
“With the UK government setting its sights on a renewed paperless strategy for the NHS during this decade, including another go at digitising all patient data, UK hospitals represent a tantalising target for cybercriminals. The ongoing proliferation of poorly secured IoT-connected devices in the NHS hasn’t helped either and can provide an easy backdoor for malicious hackers. Without robust security defences in place, sensitive patient data and connected medical devices are ripe for the picking.
“It makes the ability to identify, understand and intervene early in the in-progress attack’s lifecycle all the more essential. Such insight can limit the impact before it becomes mission-critical. Being able to isolate known infected hosts and rapidly re-image them to return them to a trusted “known good” configuration can make the difference between having to pay a ransom to recover a machine or not.
“Given the speed and scale of the attacks, it seems likely that it enters via one machine and spreads laterally on the inside using some form of scan/exploit playback. Ransomware like this does not require external command and control signalling, and so renders traditional perimeter defences which look for a call-back useless in detecting and preventing the spread of this ransomware attack.
“The NHS and key infrastructure providers alike must also realise that traditional perimeter defences are not enough. Leveraging the latest technologies, such as machine learning and advanced behavioural analytics, organisations can automate the tracking of an attacker’s activities inside a network before a ransomware action brings down essential systems. Placing a focus on where and how to intervene minimises the time patients are endangered and reduces the impact of a given threat. Any subsequent attempts at remote control of the compromised device will also be spotted using this behavioural approach to security detection.”
Graeme Newman, Chief Innovation Officer at CFC Underwriting:
 “WanaCrypt0R is spreading like wildfire and in just a few hours has already affected internet-users in a dozen countries – from Russia and Taiwan to Spain and Turkey. Specialist cyber insurance provider, CFC, has already seen a significant spike in claims following the new strain of ransomware’s release.
“WanaCrypt0R is spreading like wildfire and in just a few hours has already affected internet-users in a dozen countries – from Russia and Taiwan to Spain and Turkey. Specialist cyber insurance provider, CFC, has already seen a significant spike in claims following the new strain of ransomware’s release.
It looks as though the NHS is simply the latest high-profile victim. And the cost of paying the ransom – or not – is arguably the least of their worries right now; patient diversion, system restoration, and a whole host of other costs will begin to add up. Previous attacks on hospitals like this one have racked up bills of well over £1m.
However, it’s clear now from news reports and CFC’s own claims data that the NHS isn’t the only business being affected by this. Ransomware has been around for many years, but this particular strain is one of the fastest-spreading and most damaging that we’ve seen. If it continues at its current rate, it’s easy to see how this could end up costing UK businesses in excess of £100m.”
Peter Carlisle, VP EMEA at Thales e-Security:
 “These heinous attacks on our hospitals are a reminder that cyber criminals have no boundaries, even when their activities put lives at risk. The cybersecurity industry gives its full backing to the IT professionals in NHS Trusts who are currently tackling these threats and working hard to keep systems secure. Moving forward, much more needs to be done to improve overall encryption policies and data security strategies to ensure hackers have no chance of disrupting the vital work of our healthcare professionals.”
“These heinous attacks on our hospitals are a reminder that cyber criminals have no boundaries, even when their activities put lives at risk. The cybersecurity industry gives its full backing to the IT professionals in NHS Trusts who are currently tackling these threats and working hard to keep systems secure. Moving forward, much more needs to be done to improve overall encryption policies and data security strategies to ensure hackers have no chance of disrupting the vital work of our healthcare professionals.”
Alex Raistrick, Director WEUR at Rubrik:
 “The large-scale cyber attack that hit the NHS this afternoon has reconfirmed the need for organisations to ensure their data is effectively backed up and, more importantly, instantly recoverable should the worst happen. With an effective cloud data management solution, ransomware can be reduced to merely a minor inconvenience. Attacks are inevitable – we know that. But if you have a system that is validated and can be quickly and easily restored, you not only avoid paying the ransom, but also have the ability to return to ‘business as usual’ in record time.
“The large-scale cyber attack that hit the NHS this afternoon has reconfirmed the need for organisations to ensure their data is effectively backed up and, more importantly, instantly recoverable should the worst happen. With an effective cloud data management solution, ransomware can be reduced to merely a minor inconvenience. Attacks are inevitable – we know that. But if you have a system that is validated and can be quickly and easily restored, you not only avoid paying the ransom, but also have the ability to return to ‘business as usual’ in record time.
Long gone are the days where backup was used just for compliance purposes – it’s no longer just an insurance policy. In today’s data rich and cyber attack prevalent world, data protection has become business critical. Whether your organisation is big or small, public sector or private, investing wisely in the right level of protection for your data will enable your business to run after the unexpected happens.”
Travis Farral, Director of Security Strategy at Anomali:
 “This cyber attack is much larger than just the NHS. It appears to be a giant campaign that has hit Spain and Russia the hardest. Wanna Decryptor/ WannaCry/ WCRY, the encryption-based ransomware leverages AES128 encryption and then the victims are asked to pay in order to decrypt their files, which some already are. There is a component of the ransomware that spreads laterally, unconfirmed reports suggest this could potentially be via SMB shares or leveraging a recent Microsoft bug to spread.
“This cyber attack is much larger than just the NHS. It appears to be a giant campaign that has hit Spain and Russia the hardest. Wanna Decryptor/ WannaCry/ WCRY, the encryption-based ransomware leverages AES128 encryption and then the victims are asked to pay in order to decrypt their files, which some already are. There is a component of the ransomware that spreads laterally, unconfirmed reports suggest this could potentially be via SMB shares or leveraging a recent Microsoft bug to spread.
Ransomware attacks are becoming ever more targeted and effective, with attackers targeting specific verticals, companies, and even choosing time periods when an outage is most damaging to try to discourage any alternatives to paying the ransom. Staff training, anti-phishing controls, and reliable backups to meet recovery objectives are the most effective mitigations here. Automating and streamlining the sharing of intelligence on these threats amongst industries can also help organisations work together in both defence and remediation in ongoing attacks.”
Fraser Kyne, EMEA CTO at Bromium:
 “Information about this attack is still coming in. However it’s clear that the potential impact is huge. Unfortunately, these attacks have been rife for some time, but this is one that will resonate through all walks of life. The possible implications for patient care are quite terrifying. Unfortunately for too long the IT security industry has been focused on dealing with the symptoms of such attacks, rather than tackling the disease itself. It’s the equivalent of using Lemsip to manage the flu, rather than improving our immunity to it.”
“Information about this attack is still coming in. However it’s clear that the potential impact is huge. Unfortunately, these attacks have been rife for some time, but this is one that will resonate through all walks of life. The possible implications for patient care are quite terrifying. Unfortunately for too long the IT security industry has been focused on dealing with the symptoms of such attacks, rather than tackling the disease itself. It’s the equivalent of using Lemsip to manage the flu, rather than improving our immunity to it.”
Brian Lord OBE, Former Deputy Director GCHQ Cyber and Intelligence:

- “This would appear to be a wide ranging, well-coordinated Ransomware attack, using a new variant of Ransomware. It was well thought out, well-timed and well-coordinated. But fundamentally, there is nothing unusual about its delivery. It is still fundamentally robbery and extortion, albeit large scale
- The impact on services has not been caused by the Ransomware, it has been caused by the Trust’s necessary reaction to it, whereby they have had to shut everything down to stop its spread – not helped by poor understanding of network configuration meaning everything has to shut down
- Something like this was always inevitable.While organisations are distracted by high profile dramatized threats , such as Russian election hacking, they are neglecting basic cyber hygiene measures which can prevent the mass effectiveness of mass ransomware attacks like this
- Hopefully, this is a wakeup call. Until basic cyber hygiene is taken seriously, these attacks will continue to happen at this scale with an impact disproportionate to the nature of the attack
- The cyber security industry itself also needs to accept its share of responsibility. The reason basic breaches are growing is because organisations aren’t protecting themselves properly, because they are being made confused by the cyber vendors who avoid the most straightforward solutions
- A ‘cyber mythology’ has been created by the industry, to sell unnecessarily expensive solutions through fear. A high profile cyber-attack such as this could and should have been prevented with relatively low cost solutions
- It isn’t either expensive or complicated to understand and manage these risks. But while it is still made so, incidents like the one the NHS has experienced will continue and the real world effect will be greater than it needs to be”
David Emm, Principal Security Researcher at Kaspersky Lab:
 “The news of a cyber attack on NHS hospitals across the country highlights the fact that cyber-attackers are becoming ever more creative and professional and supports our prediction that cybercriminals are turning their attention from attacks against private users to targeted ransomware attacks against businesses. While we don’t have much information yet, the reports support the theory that the IT outage is a result of ransomware and loss of telephone systems.
“The news of a cyber attack on NHS hospitals across the country highlights the fact that cyber-attackers are becoming ever more creative and professional and supports our prediction that cybercriminals are turning their attention from attacks against private users to targeted ransomware attacks against businesses. While we don’t have much information yet, the reports support the theory that the IT outage is a result of ransomware and loss of telephone systems.
There are a range of motives for all kinds of cyber-attack, ranging from financial gain, the desire to make a social or political point, cyber-espionage or even, potentially, cyber-terrorism. If the screenshot in reports is accurate showing that attackers are asking for $300, this suggests it is a random attack rather than a targeted attack; if a cyber criminal can impact so many systems at once, why not ask for lots of money? Further, we’ve seen cyber attacks on a number of other organisations across Europe today however it’s unclear whether they are connected.
While we don’t know if the cyber attack also took down the telephony system, it does demonstrate the need for businesses to segment their network to ensure that in such attacks other aspects of the network are not affected. For example, don’t give administration rights to users by default and only allow access to data on a ‘need to access’ basis.
Over the next few years, the pace of healthcare’s digital journey will accelerate, introducing ever greater connectivity and generating ever more data. The healthcare sector in Europe is harnessing the power of the Internet and digital technologies to enhance medical care for a growing and ageing population, whilst also reducing operational costs and improving efficiency.
The numbers of attempted attacks on healthcare organisations have and will only inevitably increase. With clear gaps in security, healthcare providers and their IT security teams need to implement the sophisticated, high quality protection that will allow them to withstand cyber-attacks. From today, they need to do so in a way that complies with the new GPDR and NIS regulation recently set out by the European Union.
It is only a matter of time before healthcare-specific regulation will be introduced and by then the penalties will be even more unforgiving. The healthcare providers and their IT security professionals need to ensure they comply with the new regulations by implementing a comprehensive, multi-layered security solution that ultimately safeguards patients and the organisation as a whole.
It’s important that security is seen as an ongoing process that can’t simply be fixed by simply deploying an out-of-the-box solution. It must include policies to manage different systems within the organisation and a programme to develop greater security awareness among staff.
In order to protect organisations from such attacks, Kaspersky Lab security experts advise the following:
- Conduct proper and timely backup of your data so it can be used to restore original files after a data loss event.
- Use a security solution with behavior based detection technologies. These technologies can catch malware, including ransomware, by watching how it operates on the attacked system and making it possible to detect fresh and yet unknown samples of ransomware.
- Visit The “No More Ransom” website, a joint initiative with the goal to help victims of ransomware retrieve their encrypted data without having to pay the criminals.
- Audit installed software, not only on endpoints, but also on all nodes and servers in the network and keep it updated.
- Conduct a security assessment of the control network (i.e. a security audit, penetration testing, gap analysis) to identify and remove any security loopholes. Review external vendor and 3rd party security policies in case they have direct access to the control network.
- Request external intelligence: intelligence from reputable vendors helps organisations to predict future attacks on the company.
- Educate your employees, paying special attention to operational and engineering staff and their awareness of recent threats and attacks.
- Provide protection inside and outside the perimeter. A proper security strategy has to devote significant resources to attack detection and response in order to block an attack before it reaches critically important objects.”
Pete Turner, Consumer Security Expert at Avast:
 “This latest attack once again proves that ransomware is a powerful weapon that can be used against consumers, businesses and now patients and healthcare professionals alike.
“This latest attack once again proves that ransomware is a powerful weapon that can be used against consumers, businesses and now patients and healthcare professionals alike.
We have observed a massive peak in WanaCrypt0r 2.0 attacks today, with more than 36,000 detections, so far. While activity has largely targeted Russia, Ukraine, and Taiwan, we are now seeing a peak in the UK with this latest NHS attack. While this has reached a peak today, this was first detected in mid-February, showing how critical it is for organisations to stay up-to-date on cyber security.
We have recently observed major ransomware strains being delivered through malicious Office documents containing macros sent via email, as well as via exploit kits. If ransomware infects via email attachment, a malicious Office document first needs to be opened and then macros enabled in order for the ransomware to be downloaded. In the case of ransomware infecting via an exploit, a malicious site is typically visited and then a computer with a zero-day vulnerability is exploited to infect it with ransomware.
This could well be the source of the cyber breach affecting the NHS Trusts and company’s such as Telefonica today. It’s critical that organisations and employees, particularly those in our most critical sectors like healthcare, start to think proactively about how to protect themselves from ransomware by:
- Ensuring they have the latest digital security installed
- Maintaining their devices by keeping all apps and programmes up to date
- Being vigilant about not opening suspicious emails and attachments
- Not downloading software or applications from unauthorised sources which may not be official and could contain malicious ransomware
Observing simple rules and being smart about what we do online are all important defences against ransomware.
This is, of course, not the first time that an NHS trust has been hit by a cyberattack. In October 2016, it was discovered that at least 28 NHS trusts in England had been the victim of ransomware attacks, and the emergence of open source ransomware programs hosted on GitHub are making these kinds of attacks more common. Today, 16 NHS Trusts are reporting this attack simultaneously.”
Marco Cova, Senior Security Researcher at Lastline:
 “The interesting story underlying the NHS and Telefonica attacks is that they both are using the same ransomware, Wanna, which exploits the NSA’[s EXTERNAALBLUE vulnerability that was released recently in the Shadow Brokers data dump.
“The interesting story underlying the NHS and Telefonica attacks is that they both are using the same ransomware, Wanna, which exploits the NSA’[s EXTERNAALBLUE vulnerability that was released recently in the Shadow Brokers data dump.
The NSA has known about this vulnerability in Windows for quite some time now: this incident will certainly refuel the discussion on whether security agencies should responsibly inform vendors about vulnerabilities they find or sitting on them for their own use (as in this case): the leak of the exploit enabled today’s hack
This is an example of a worm: a malware that can automatically spread from one machine to another without user intervention. The attackers can compromise 1 victim and the infected computer will automatically attempt to take over vulnerable machines reachable from the infected one. Of course, this is very efficient for the attackers.
Microsoft released the patch address ETERNALBLUE on March 14, 2017 (a month *before* the Shadow Brokers release). In other words, in this case there actually was time for people to patch. It’s easy to blame people who don’t upgrade, but in practice things are often more complicated: operations team may not touch legacy systems for a number of reasons; in some cases they may even be unaware that such legacy systems are running in their infrastructure.”
Spencer Young, RVP EMEA at Imperva:
 “It’s too early to say what or who is behind these attacks. But, we’ve seen the warning signs over the last few years – risks due to massive denial of service attacks, loss of service due to ransomware, and attacks against infrastructure with the stakes getting continually higher and now directly effecting people in potentially devastating ways.
“It’s too early to say what or who is behind these attacks. But, we’ve seen the warning signs over the last few years – risks due to massive denial of service attacks, loss of service due to ransomware, and attacks against infrastructure with the stakes getting continually higher and now directly effecting people in potentially devastating ways.
Ransomware works because itis delivered in various forms of email messages, either containing infected files or linking to infected pages, or files. Email messages take various forms, some more simple while other more subtle and sophisticated. These email messages are delivered through massive phishing campaigns to millions of individuals, some of which will fall prey despite all precautions, and this is likely the case here.
Imperva research titled, Phishing Trip to Brazil, (https://www.imperva.com/docs/HII_Phishing_Brazil_report.pdf) shows that most infections, any type of infection, on end points happen during work hours, hence it is not uncommon to see an enterprise end station hit by ransomware. The most important thing to notice in such incidents – clearly demonstrated in this case is ransomware usually incurs operational damages that cannot be recovered or avoided by paying a ransom.”
Paul Norris, Senior Systems Engineer at Tripwire:
 “The worst time to create an incident response plan is during an incident. At this point, there can be little doubt that cyber attacks can impact human safety. We’re no longer talking about protecting data, or credit card theft alone. Whether it’s a hospital serving patients or a utility delivering power to customers, cyber attacks can have real impact on the physical world. Hospitals and other medical facilities need to recognize the impact that these incidents can have on their operational status, and take proactive measures to implement foundational controls for information security. Implementing basic controls for systems that affect patient care needs to be as standard as sterilizing equipment.
“The worst time to create an incident response plan is during an incident. At this point, there can be little doubt that cyber attacks can impact human safety. We’re no longer talking about protecting data, or credit card theft alone. Whether it’s a hospital serving patients or a utility delivering power to customers, cyber attacks can have real impact on the physical world. Hospitals and other medical facilities need to recognize the impact that these incidents can have on their operational status, and take proactive measures to implement foundational controls for information security. Implementing basic controls for systems that affect patient care needs to be as standard as sterilizing equipment.
“Keeping devices on current operating systems, hardening systems, updating software and installing security patches might not be exciting, but it’s proven to reduce the number of successful attacks. Hardening systems to a specific standard or best practices could also help reduce propagation of the ransomware across other parts of the organization. As other industries have ramped up security due to increased breach activity, attackers are migrating to less protected targets. Hospitals contain valuable data and a lower security profile, making them next on the list. Information security professionals in the hospital community should use this report as an opportunity to educate their executives and broader IT partners about the very real risks facing the industry.”
Paul Calatayud, CTO at Firemon:
 “The recent NHS hospital attack is an indicator for a new evolution of malware that will focus on critical systems such as airlines and hospitals where paying ransoms may be the only way to resume business operations in some case life or death.
“The recent NHS hospital attack is an indicator for a new evolution of malware that will focus on critical systems such as airlines and hospitals where paying ransoms may be the only way to resume business operations in some case life or death.
It’s also a good time to highlight that attacks such as ransomware are only effective if the information residing within their encryption is valuable. To avoid this, the best approach is to prevent these types of malware from being able to grab hold of your systems by deploying intelligent defenses such as a next-gen firewall or next-gen antivirus. While the NHS no doubt has taken these and other precautions, the complexity of their security environments may be leaving gaps where attacker can find a way in. Therefore, managing all those security technologies becomes vitally important.
Another tip is to have a backup plan to ensure the data on these systems is always backed up. If it is, and you are hit with such an attack, you can simply restore and be back up and run in no time. Some backups solutions are better than others, so ensure it’s near-real time for these to be viable options.”
Javvad Malik, Security Advocate at AlienVault:
 “It’s early and details are limited to fully assess what the situation is. However, it appears as if ransomware may have infected NHS hospital systems.
“It’s early and details are limited to fully assess what the situation is. However, it appears as if ransomware may have infected NHS hospital systems.
“The attack seems to show that there is no segregation between front-end, back-end, and critical NHS systems. While it is not always possible to defend against all attacks, having critical systems segmented, to prevent being impacted by such a breach could have allowed core capabilities to remain online.
“By having security designed into system architecture, it can make services harder to compromise, or reduce the impact of a compromise.”
Lee Munson, Security Researcher at Comparitech.com:
 “Early reports of a large-scale cyber-attack against UK hospitals appear to be somewhat misleading, with the implication being that there has been a data breach or huge DDoS attack.
“Early reports of a large-scale cyber-attack against UK hospitals appear to be somewhat misleading, with the implication being that there has been a data breach or huge DDoS attack.
The truth, however, appears to be that many devices have been infected with ransomware – which explains why NHS users are being asked to pay to regain control over their machines and the data on them.
How this has spread throughout several trusts is not yet clear but it would seem to suggest either that many doctors and other hospital staff have been targeted in quick succession, or that an extremely convincing email containing a malicious payload has been shared far and wide.
In any event, the incident highlights many issues.
Firstly, there is the lack of security training and awareness that has likely led to several people opening emails and/or attachments from unknown senders.
Secondly, there must be questions as to why this attack has been so damaging in such a short period of time. My thoughts are that there is either an issue with the security around the entire NHS network and/or the IT department has been extremely tardy in taking and restoring backups of essential data.”
Jamie Moles, Principal Security Consultant at Lastline:
 “While security remains a low priority for NHS management, they will increasingly fall victim to these kinds of attacks, which will cause serious problems as it results in the cancellation of treatments whilst the affected systems are investigated and cleaned up. The National Health Service is one of the largest organisations in the United Kingdom. With an annual budget in the region of £116 billion, it is a massive target for cyber-attacks and currently, it’s a poorly defended target.
“While security remains a low priority for NHS management, they will increasingly fall victim to these kinds of attacks, which will cause serious problems as it results in the cancellation of treatments whilst the affected systems are investigated and cleaned up. The National Health Service is one of the largest organisations in the United Kingdom. With an annual budget in the region of £116 billion, it is a massive target for cyber-attacks and currently, it’s a poorly defended target.
There are a number of trusts in deficit and spending on the NHS has dropped in real terms since the recession. Priorities for all NHS trusts are unsurprisingly targeted at medical needs over and above admin and operational needs, but of course this includes IT Security.
Interestingly, the NHS takes a very strict and sanitary approach to dealing with these attacks, shutting down almost all of its IT capabilities while it triages and treats the problem. Why would we expect any different from a medical organization? Moving forward if we are to prevent these attacks causing delays to treatment and potentially deaths, NHS trusts are going to have to invest in technology to deal with cyber-threats. There are plenty of good technologies available to assist in this issue and they can be scaled effectively and cost efficiently to cope with massive organisations like the NHS.”
Gavin Millard, EMEA Technical Director at Tenable Network Security:
 “Whilst this isn’t the first time the NHS has been hit with Ransomware, it seems like this particular attack has affected more trusts than before. Until the NHS speak publicly about how the ransomware entered their systems and started encrypting crucial files, we can only guess that it was successful due to lax security practices like insufficient patching, poor configuration, and effective filtering of internet communications.
“Whilst this isn’t the first time the NHS has been hit with Ransomware, it seems like this particular attack has affected more trusts than before. Until the NHS speak publicly about how the ransomware entered their systems and started encrypting crucial files, we can only guess that it was successful due to lax security practices like insufficient patching, poor configuration, and effective filtering of internet communications.
What is really interesting is that the NHS doesn’t appear to be the only organisation tackling a major ransomware outbreak this afternoon. Reports are emerging of ransomware named “Wcry / Wannacry” taking systems offline in a number of other geographies – Telefonica, banks BBVA and Santander have all been reported as affected.
WCry is a fairly new strain of malware with some reports suggesting it’s been picked up in 14 countries, including Germany, Spain, Russia and the UK. The speed with which its spreading is frightening. Ransomware becomes a significant nuisance if full backups of the systems weren’t taken, dramatically increasing the recovery time if the ransom isn’t paid.”
Nathan King, Director at Cyber Security Consultancy at Cyberis:
 “It is well-established that the health sector is an industry which has been specifically and repeatedly targeted by cyber attacks and therefore the NHS should have clearly identified the threat as a priority for vulnerability management and predicted such incidents. Managing the threat and related vulnerabilities is not straightforward as it involves people, process and technology controls to be fully effective. Practically, there is no 100% effective defence strategy. For the NHS, the logistics of coordinating the deployment and management of the controls would not be easy and the associated costs likely to be high.”
“It is well-established that the health sector is an industry which has been specifically and repeatedly targeted by cyber attacks and therefore the NHS should have clearly identified the threat as a priority for vulnerability management and predicted such incidents. Managing the threat and related vulnerabilities is not straightforward as it involves people, process and technology controls to be fully effective. Practically, there is no 100% effective defence strategy. For the NHS, the logistics of coordinating the deployment and management of the controls would not be easy and the associated costs likely to be high.”
Israel Barak, CISO at Cybereason, comments: “We know that ransomware purveyors are often savvy e-marketers that know their targets, and it is not uncommon for a ransomware gang to run multiple campaigns at the same time, with tiered pricing based on a variety of parameters such as vertical industry, region, age, etc. However, the attacks on the NHS trusts across the UK seem to show particularly ruthless calculation even by criminal standards, banking on the trusts having weak defences and being especially desperate to restore access to their systems due to health and even lives being at stake.
While ransoms have surpassed the hundreds of thousands mark, the goal is to set a price that makes it either cheaper or easier for the victims to pay the ransom then to recreate or restore the compromised systems, especially when the victim has a sense of urgency. Today’s ransoms show that this can still be very costly, especially when it comes to lost operational time and data. We’ve seen many examples where companies didn’t have the proper backups in place and decided to pay the ransom so that they could resume normal business operations, and that will obviously be a pressing concern for the affected trusts.”
Ed Macnair, CEO at Censornet:
 “It’s pretty disgusting to see the morals of hackers sink to the depths we’re seeing today. This isn’t just about the financial implication – this is bound to lead to operations, procedures and appointments all being cancelled, affecting thousands of patients.
“It’s pretty disgusting to see the morals of hackers sink to the depths we’re seeing today. This isn’t just about the financial implication – this is bound to lead to operations, procedures and appointments all being cancelled, affecting thousands of patients.
Ransomware is on the rise. And no organization is immune. Freedom of information requests published recently highlighted that 28 of 29 NHS trusts in the UK had suffered ransomware attacks in the last year. And in February, a hospital in California paid nearly $100,000 to a ransomware attacker.
Our advice to hospitals is as follows:
Shore up authentication: passwords don’t cut it. And neither does two-factor authentication. You really need multi-factor authentication (MFA), which uses a number of variables to validate your users. Two thirds of network breaches are caused by compromised weak or stolen passwords. You really can’t afford to leave your front door wide open to hackers.
Shine the light on shadow IT: particularly with the use of the cloud, you have to be switched on in terms of what apps employees are using and why and for what. It will help you get a gasp of cloud sprawl (proliferation of app usage) and help limit security vulnerabilities.
Permission: you need to be prescriptive about who has access to what and when you want them to have it. The less people who are granted access to sensitive data, the less change you have of a data breach coming your way.
Of course, there are a million and one things you can – and should – be doing to protect systems, data and networks. Just as organizations like hospitals are completely dependent on tech to function and becoming more reliant on cloud apps, it is increasingly important to ensure that your back is covered on a security level. If not, the consequences – such as the risk to patient safety – can be dire.”
Peter Groucutt, Managing Director at Databarracks:
 What is ransomware and how does it happen?
What is ransomware and how does it happen?
“Ransomware is malware that, upon infection, prevents access to certain elements of your systems until a ransom is paid to the attackers. There are many different strains of ransomware, which variously encrypt data and system files, through a range of possible attack vectors.
What actually happens?
“Regardless of what the ransomware attacks, the methods are broadly the same: attackers exploit a security vulnerability or backdoor in order to infiltrate the victim’s systems silently and encrypt critical systems and data.
Attackers then demand payment (often in an untraceable cryptocurrency, such as Bitcoins) within a specified time frame. If the victim fails to pay in time, or attempts to remove the malware manually, attackers destroy the unique decryption key, and any compromised data and systems will be permanently irretrievable.”
Who is being targeted, and why?
“The short answer is everyone – individuals and organisations alike.
Cybercrime is big business, and ransomware is popular for a reason: it’s a low-investment, high-yield form of attack, with little technical barrier to entry. Malicious groups and individuals can now purchase ransomware capabilities as discrete tools with full GUIs on places like the Dark Web, or even as a managed service from criminal providers.
This increased accessibility has significantly broadened the variety of potential attackers in recent years, and as such it’s hard to generalize around the motivations of individuals. Whether it’s lone actors operating from a bedroom, a politically-motivated hacktivist, or an international criminal organisation with salaried employees, everyone is a target to someone.
Larger organisations with valuable datasets and a public reputation to protect obviously represent high-value targets, and often attract the most sophisticated attacks as a result.”
Why are these attacks so successful?
“Whoever the target is, the rise of cryptocurrencies has increased the degree of anonymity afforded to criminals taking ransom payments.
Cyber criminals balance risk and reward. Taking payments as cryptocurrency means the reward has stayed constant, whilst the risk of being caught has dropped significantly.”
How to recover
“If you are hit with a ransomware attack you essentially have two options. You can either recover the information from a previous backup or pay the ransom. However, even if you pay the ransom, there is no guarantee that you will actually get your data back, so the only way to stay fully protected is to have historic copies of your data.
When recovering from ransomware, your two aims are to minimise the amount of data loss and to minimise the amount of IT downtime.
Although outright prevention of ransomware is impossible, there are simple yet essential steps organisations can take to reduce the risk and impact of attacks.”
Recommendations for recovery
“It is vital that the Incident Response Team or Crisis Management Team has the authority to be able to make large scale, operational decisions to take systems offline to limit the spread of infection.
You must then find when the ransomware installation occurred in order to be able to restore clean data from before the infection.
Once the most recent clean data is identified you can being a typical recovery, restoring data and testing before bringing systems back online again.”
Dr Malcolm Murphy, Technology Director, Western Europe at Infoblox:
 “While ransomware has traditionally posed a threat to consumers and their personal data, attacks such as this demonstrate that the risk to public services is far greater. With hospitals actually being shut down as a result of ransomware, the extent to which attacks such as these can pose a risk to both operations and patient safety is abundantly clear.
“While ransomware has traditionally posed a threat to consumers and their personal data, attacks such as this demonstrate that the risk to public services is far greater. With hospitals actually being shut down as a result of ransomware, the extent to which attacks such as these can pose a risk to both operations and patient safety is abundantly clear.
“The ransomware trend is only set to increase, however. The last Infoblox DNS Threat Index reported a 3,500 per cent increase in domains that either hosted or communicated with malicious ransomware downloads was recorded in the first quarter of last year, and its commoditisation through cyber-crime toolkits means that even the most novice criminal can deploy it.
“All organisations must ensure that their security measures are up to scratch: from having all software patched and up to date and making sure users observe best practice, to deploying DNS effectively as an enforcement point to block ransomware.”
Richard Anstey, CTO EMEA at Synchronoss:
 “While it’s still unclear what data has been accessed in today’s NHS attack, personal data is extremely valuable and healthcare records tend to be the most prized by attackers. Add to that the rise of crypto-currencies and medium of the dark web and you have a perfect storm for malicious actors to trade in this type of data. We are in an especially vulnerable time because of the early stage of adoption of electronic health records.
“While it’s still unclear what data has been accessed in today’s NHS attack, personal data is extremely valuable and healthcare records tend to be the most prized by attackers. Add to that the rise of crypto-currencies and medium of the dark web and you have a perfect storm for malicious actors to trade in this type of data. We are in an especially vulnerable time because of the early stage of adoption of electronic health records.
“Healthcare companies and the NHS can proactively defend their data by ensuring their employee’s personal and professional devices are secure. With the increasing importance of BYOD for healthcare professionals, it’s vital to deliver the right blend of mobility and security – the right amount of security with the minimum friction.
“Electronic health data is here to stay, and it’s important that the NHS continues on its digital transformation journey as this will ultimately help give doctors a more holistic view of their patients and enable them to give top-tier care. As ransomware persists in the medical field, it’s imperative these facilities maintain their vigilance against these threats and implement a solution that guarantees the only people with access to healthcare information are the people involved in providing patient care.”
Paul Cant, VP of EMEA at BMC Software:
 “Hackers will increasingly target organisations like the NHS to disrupt operations in an attempt to gain access to a wealth of personal data.
“Hackers will increasingly target organisations like the NHS to disrupt operations in an attempt to gain access to a wealth of personal data.
“As the NHS continues on its digital journey, more and more of its assets will be at risk during this transformation, unless robust security policies are in place.
“This particular case is an extraordinary example of just how dangerous these kind of cyber-attacks can be, not just to companies and services, but to people’s livelihoods.”
Jean-Frederic Karcher, Head of Security at Maintel:
 “This NHS attack is further proof of the rise of ransomware. Ransomware has increased three-fold from 2015 at 1000 attacks a day to 4000 attacks a day in 2017, and shows no signs of slowing down. It will be one of the top three malicious software to watch out for in the coming year and with impact across sectors and society. The right security measures including threat detection must be put into place to ensure businesses, their employees, and customers are kept safe
“This NHS attack is further proof of the rise of ransomware. Ransomware has increased three-fold from 2015 at 1000 attacks a day to 4000 attacks a day in 2017, and shows no signs of slowing down. It will be one of the top three malicious software to watch out for in the coming year and with impact across sectors and society. The right security measures including threat detection must be put into place to ensure businesses, their employees, and customers are kept safe
The proliferation of ransomware comes as a direct result of its high monetary return on investment. With more valuable information readily available on the web, hackers are using this as a means to steal, lock out users and then ransomware back access – all with the goal of a sizable pay packet at the end.
The main reason medical institutions and the NHS are targeted is because they have vast amounts of patient data at their disposal. Hackers can sell large batches of this personal data for profit on the black market.
Medical information can be worth 10 times more than credit card numbers on the deep web. Fraudsters can use this data to create fake IDs to buy medical equipment or drugs, or combine a patient number with a false provider number and file fictional claims with insurers. Consumers often discover their credentials have been stolen a long time after fraudsters have used their personal medical ID to impersonate them and obtain health services.
This means medical identity theft is not immediately identified by a patient or their provider, giving criminals ample time to maximise the use of such credentials. This is the main reason why medical data is valued so much more highly than credit card data, which tend to be quickly flagged and canceled by banks.
As awareness of cybercrime within the public sector continues to rise, one thing is clear – organisations are continuing to rely on aging computer systems that do not use the latest security features. Indeed, NHS hospitals are using very old legacy systems – often Windows systems over 10 years old that have not seen any patches and are therefore extremely vulnerable to such attacks. Honestly, this attack should not come as a surprise to the security community.”
Matt Lock, Director of Sales Engineer at Varonis:
 “A lot of organisations like to think they don’t have insider threats, but often at times it’s the loud intrusion of ransomware that is alerting an organisation to over-exposed, unmonitored permissions and data. When a user / employee with excessive permissions to data across the network is infected and the ransomware spreads to every file to which that user has access, organisations cannot ignore the crippling effects of hijacked data. In this case, it’s not just the administrative and executive staff affected, doctors and patients have no access to the resources they need to provide timely and effective medical care. This cyberattack on a rapidly growing list of NHS Trusts is shining a big, bright spotlight on the holes in their defences. If ransomware can temporarily halt productivity and medical care due to overexposed permissions, you can only imagine what a malicious insider or external actor with co-opted credentials can do to your organisation and how long they can go undetected.
“A lot of organisations like to think they don’t have insider threats, but often at times it’s the loud intrusion of ransomware that is alerting an organisation to over-exposed, unmonitored permissions and data. When a user / employee with excessive permissions to data across the network is infected and the ransomware spreads to every file to which that user has access, organisations cannot ignore the crippling effects of hijacked data. In this case, it’s not just the administrative and executive staff affected, doctors and patients have no access to the resources they need to provide timely and effective medical care. This cyberattack on a rapidly growing list of NHS Trusts is shining a big, bright spotlight on the holes in their defences. If ransomware can temporarily halt productivity and medical care due to overexposed permissions, you can only imagine what a malicious insider or external actor with co-opted credentials can do to your organisation and how long they can go undetected.
Organisations should ensure that they actively monitor their IT infrastructure, specifically users and the files and emails they can access, and then perform regular attestations of access rights to reduce overexposed sensitive from being hijacked in the first place as well as perform user behaviour analytics against threat models that look for signs of ransomware activity.”
Jason Allaway, VP UK and Ireland at RES:
 “It’s becoming more common an occurrence to see ransomware attacks against healthcare organisations; after all, they are a prime target for attackers due to the nature of the data they hold. It’s not just a monetary loss when it comes to medical facilities: it’s far more important. The fact that East and North Hertfordshire has had to suspend all of their non-urgent activity, and shut down A&E is a testament to how much they rely on their data to operate.
“It’s becoming more common an occurrence to see ransomware attacks against healthcare organisations; after all, they are a prime target for attackers due to the nature of the data they hold. It’s not just a monetary loss when it comes to medical facilities: it’s far more important. The fact that East and North Hertfordshire has had to suspend all of their non-urgent activity, and shut down A&E is a testament to how much they rely on their data to operate.
“Education, vigilance and proven technology such as context-aware access controls, comprehensive blacklisting and whitelisting, read-only access, automated deprovisioning and adequate back-up need to be put in place by healthcare organisations to both prevent and combat this problem as efficiently as possible. Today’s events are clear evidence that many healthcare organisations still need to invest in this integrated approach to security.”
David Warburton, Senior Systems Engineer, Central Government and Defence at F5 Networks:
 “There is no silver bullet for protecting against ransomware and the overwhelming concern for personal data is exactly what cyber-criminals are counting on. The individual ransom demands seem low, around $300, but this will add up quickly if hundreds or thousands of computers are affected. Although paying a ransom might encourage further attacks, the reality is that patient care could be affected in a very direct way if care givers are unable to access their systems. As with many aspects of information security, prevention is better than cure, but ransomware is very difficult to totally prevent. The NHS seem to have taken the best action they can – by shutting down systems they have limited the spread of the infection. For many organisations, the best methods currently available for combatting ransomware are to have reliable backups and an up to date response plan.
“There is no silver bullet for protecting against ransomware and the overwhelming concern for personal data is exactly what cyber-criminals are counting on. The individual ransom demands seem low, around $300, but this will add up quickly if hundreds or thousands of computers are affected. Although paying a ransom might encourage further attacks, the reality is that patient care could be affected in a very direct way if care givers are unable to access their systems. As with many aspects of information security, prevention is better than cure, but ransomware is very difficult to totally prevent. The NHS seem to have taken the best action they can – by shutting down systems they have limited the spread of the infection. For many organisations, the best methods currently available for combatting ransomware are to have reliable backups and an up to date response plan.
“Looking ahead, the NHS will need to determine the initial source of compromise and then review employee education. As data becomes more of a commodity and more workplace tools are built around apps and connected to the Internet of Things, there are an increasing number of gateways available for cyber-criminals to infiltrate. Following the attack, it will be important to increase awareness across all industries about why it happened and educate organisations on how to safeguard critical data and ensure security compliance.”
Mike East VP EMEA, at CrowdStrike:
 “Holding the national health services to ransom is a critical national security issue.
“Holding the national health services to ransom is a critical national security issue.
“Finding that patient data is being held to ransom is like watching a cardiac monitor start flat lining. This attack is posing a threat as ambulances have been diverted and GP surgeries have cancelled routine appointments. For our frontline nurses and doctors real time access to patient information is critical to delivering high-quality patient care.
“The attack targeting is likely in bulk, via massive phishing campaigns delivering .zip archives with themes such as fake invoices, job offers, security warnings, undelivered email. Once an infection takes place, Wana encrypts victim files using the AES-128 cipher, and demands a Bitcoin ransom of increasing value as time passes. Files encrypted by Wana are appended with a file extension of .wncry. Observed ransom demands require victims to pay either $300 or $600 USD worth of BTC for a decryption key.
“Without the defenses in place, once ransomware has initiated, the chances are it is already too late to recover that data set. Obviously, robust backups are a foundational best practice to prepare for ransomware attacks, but they are no panacea. With variants like Locky, Samas and KeRanger acting as harbingers of future ransomware attacks that can also delete or damage backups. The best medicine for treating ransomware will be preventing an infection in the first place.
“The best defense to wide scale cyber security is a crowdsourced response. This is about pulling together what we have learnt on one machine, one endpoint and applying that learning to help defend other networks. Once this attack is over, the next step has to be attribution and bringing the perpetrator to justice.”
Paul Calatayud, Chief Technology Officer at FireMon:
 “The NHS hospital attack is an indicator for a new evolution of malware that will focus on critical systems such as airlines and hospitals where paying ransoms may be the only way to resume business operations in some case life or death.
“The NHS hospital attack is an indicator for a new evolution of malware that will focus on critical systems such as airlines and hospitals where paying ransoms may be the only way to resume business operations in some case life or death.
This does and will continue to happen within American hospitals, often going unreported.
It’s a good time to highlight that attacks such as ransomware are only effective if the information residing within their encryption is valuable. To avoid this, the best approach is to prevent these types of malware from being able to grab hold of your systems by using intelligent defenses such as a next-generation firewall or next-generation antivirus.
While the NHS no doubt has taken these and other precautions, the complexity of their security environments may be leaving gaps where attackers can find a way in. Therefore, managing all those security technologies becomes vitally important.
Another tip is to have a backup plan to ensure the data on these systems is always backed up. If it is, and you are hit with such an attack, you can simply restore and be back up and running in no time. Some backups solutions are better than others, so ensure it’s near-real time for these to be viable options.”
Terry Ray, Chief Strategist at Imperva:
 We’ve seen the warning signs over the last few years – risks due to massive denial of service attacks, loss of service due to ransomware, and attacks against infrastructure with the stakes getting continually higher and now directly effecting people in potentially devastating ways.
We’ve seen the warning signs over the last few years – risks due to massive denial of service attacks, loss of service due to ransomware, and attacks against infrastructure with the stakes getting continually higher and now directly effecting people in potentially devastating ways.
Ransomware works because itis delivered in various forms of email messages, either containing infected files or linking to infected pages, or files. Email messages take various forms, some more simple while other more subtle and sophisticated. These email messages are delivered through massive phishing campaigns to millions of individuals, some of which will fall prey despite all precautions, and this is likely the case here.
Imperva research titled, Phishing Trip to Brazil, (https://www.imperva.com/docs/HII_Phishing_Brazil_report.pdf) shows that most infections, any type of infection, on end points happen during work hours, hence it is not uncommon to see an enterprise end station hit by ransomware. The most important thing to notice in such incidents – clearly demonstrated in this case is ransomware usually incurs operational damages that cannot be recovered or avoided by paying a ransom.”
Mounir Hahad, Ph.D., Senior Director at CyphortLabs:
 “This seems to be a very large scale attack, with earlier reports of infections in Russia, Ukraine, Taiwan as well as all over Europe. There is cause for alarm in the US as well given the speed at which this attack has spread and the fact that it seems to know no border.
“This seems to be a very large scale attack, with earlier reports of infections in Russia, Ukraine, Taiwan as well as all over Europe. There is cause for alarm in the US as well given the speed at which this attack has spread and the fact that it seems to know no border.
This ransomware seems to exploit a vulnerability in the Windows file sharing protocol SMBv1 that was patched by Microsoft 2 months ago. We know of several organizations that have taken steps to completely eradicate this protocol from their networks, and yet, so many PCs worldwide remain unpatched and vulnerable.
This shows how quickly criminals are able to adopt newly exposed vulnerabilities and how slow the rest of us are to patch.”
Philip Lieberman, President at Lieberman Software:
 “This is an example of the systemic failure of government and commercial firms to implement security, resiliency and appropriate privacy policies.
“This is an example of the systemic failure of government and commercial firms to implement security, resiliency and appropriate privacy policies.
Once again, the immaturity of security ecosystems and fantasy privacy policies continue to endanger and kill EU citizens. When the privacy of criminals has primacy over the safety and commercial interests of legitimate businesses, this is the only outcome: death, theft, and commercial failure which seem acceptable costs to the EU leadership.
US technology exists to minimize these attacks and their consequences, but their usage is considered criminal activity by the EU.
The other trends that add to this tragedy are the lack of a significant UK IT security culture, poor budgets for security tools, and rampant outsourcing.
All that has happened in cyber attacks was predicted and plenty more is on the way till the EU governments wake up and change their priorities as they apply to privacy and security.”
Mike Pittenger, Vice President Security Strategy at Black Duck Software:
 “As well as NHS services, this attack is hitting a lot of people, including Telefonica, the Russian Interior Ministry, FedEx and others. Speculation today is that it appears to be exploiting a vulnerability in Windows through an NSA exploit leaked by The Shadow Brokers last month.”
“As well as NHS services, this attack is hitting a lot of people, including Telefonica, the Russian Interior Ministry, FedEx and others. Speculation today is that it appears to be exploiting a vulnerability in Windows through an NSA exploit leaked by The Shadow Brokers last month.”
“The problem seems not to have been the vulnerability, but that a patch supplied on March 14th by Microsoft likely wasn’t applied by these organisations. This clearly demonstrates the importance of having an incident response plan, and the need to understand both remediation and mitigation controls. Once a vulnerability is disclosed, it’s a race between attackers and defenders. It seems as though the victim organisations did not install the available patch, and now they are suffering the consequences.”
“This is a good demonstration of “why” attackers value vulnerabilities in open source code as well. Microsoft “pushed” a patch to organisations that have licensed the affected software, and yet it is still a “target rich” environment of vulnerable systems. With open source, that service level agreement (SLA) typically does not exist. Organisations need to monitor the open source they use for updates and patches, and then “pull” those into their code base.”
Mike Cotton, Vice President, Research & Development at Digital Defense, Inc.:
 “According to Black Duck’s 2017 Open Source Security and Risk Analysis study, organisations are likely unaware that they are even using open source software that’s vulnerable, much less monitoring hundreds of such projects for security updates. We found that over 7% of 1000+ applications we audited were vulnerable to well publicised vulnerabilities like Heartbleed, Poodle, Freak and Drown years after some of these were first disclosed.”
“According to Black Duck’s 2017 Open Source Security and Risk Analysis study, organisations are likely unaware that they are even using open source software that’s vulnerable, much less monitoring hundreds of such projects for security updates. We found that over 7% of 1000+ applications we audited were vulnerable to well publicised vulnerabilities like Heartbleed, Poodle, Freak and Drown years after some of these were first disclosed.”
“The latest Shadowbroker’s release was probably the most high-impact exploit drop we’ve seen in the last several years. While earlier leaks from the Shadowbrokers focused on less common device services and third-party software, the exploit drop released in the April targeted core Windows operating system services and were likely among the crown jewels of the NSA toolkits.
The ETERNALBLUE exploit in particular allows for reliable remote compromise of a wide variety of Windows server and client systems using nothing but network access as a precondition. It will remain one of the most heavily used exploits in attacker toolkits for years to come.”
Nik Whitfield, CEO at Panaseer:
 “The chaos faced today by the NHS is a direct result of poor cyber hygiene. The bigger the organisation, the more challenging it is to maintain ‘basics’, which include being clear on hardware assets, monitoring vulnerabilities and (crucially in this case) applying priority software patches.
“The chaos faced today by the NHS is a direct result of poor cyber hygiene. The bigger the organisation, the more challenging it is to maintain ‘basics’, which include being clear on hardware assets, monitoring vulnerabilities and (crucially in this case) applying priority software patches.
“The underlying issue with cybercrime is that the relationship between cybercriminals and organisations is asymmetric – the criminals only need to succeed once, whereas defenders have to get it right every single time. It is becomingly increasingly impossible for organisations to be 100% secure – the key is ensuring that they are ‘secure enough’. In a complex technology environment, like the NHS, cyber hygiene can a huge challenge but the risk of neglecting it means that it was only a matter of time before an attack was successful.”
Kevin Cunningham, Managing Director at SQS Group
 The news that the NHS England has been hit by a large-scale ‘cyber-attack’ holding trusts across London, Blackburn, Nottingham, Cumbria and Hertfordshire to ransom, outlining the clear need to protect vulnerable people from vulnerable IT. Causing GPs and medical staff to resort to pen and paper, with phone and IT systems down. Several trusts have even had to request those in need of care not to come to A&E unless it’s urgent.
The news that the NHS England has been hit by a large-scale ‘cyber-attack’ holding trusts across London, Blackburn, Nottingham, Cumbria and Hertfordshire to ransom, outlining the clear need to protect vulnerable people from vulnerable IT. Causing GPs and medical staff to resort to pen and paper, with phone and IT systems down. Several trusts have even had to request those in need of care not to come to A&E unless it’s urgent.
With the British political landscape currently facing turbulent times, the NHS has been placed under pressure to cut costs and embrace digital methods to improve services, forcing many to outsource IT contracts. However, in doing so, data integrity and patient records have been put at risk, highlighting a link impact of cost cutting. To mitigate risk and avoid further data being compromised in the health sector, independent assurance is vital to ensure the necessary safeguards are in place to protect patients before and after outsourcing IT.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



