Summary
In an earlier article we briefly referred to Expanded Password System (EPS) that accepts both images and texts as the shared secrets.
The proposition of EPS is now acknowledged as a ‘Draft Proposal’ for OASIS Open Projects that OASIS has recently launched as a new standardization program. We have publicized an EPS draft specification there.
The EPS is also among the topics to be discussed in Seattle (19-21/September) and Amsterdam (29-31/October) at KuppingerCole’s Consumer Identity World 2018, Besides talking about the EPS as a speaker, the writer will also take part in panel discussions about biometrics and multi-factor authentications.
With these developments as the backdrop, we came up with a motto of ‘Identity Assurance by Our Own Volition and Memory’ for our enterprise. This motto could stand especially well for the emerging concept of ‘Self-Sovereign Identity’.
What is Expanded Password System?
Passwords need to be remembered and recalled; a password written on a memo is no more than ‘what we possess’, definitely not ‘what we know or remember’, say, not the shared secrets.
The Expanded Password System that we advocate, which offers a choice of making use of episodic image memory in addition to textual memory, can be viewed as an enhanced successor to text-only password systems on its own. Furthermore, the EPS will enable us to see truly powerful multi-factor authentications with a strong unique password being used as one of the factors for all different accounts, whether indoor or outdoor.
With the EPS used as a rescue-password in case of false rejection, biometric solutions will offer good convenience without sacrificing the confidentiality too much. We would also be able to see truly reliable decentralized ID federations with a strong unique password being used as the master-password for each of single-sign-on services and password management tools. The outcome will be the most highly assured identity achieved through the most reliable “shared secrets”
Identity verification which has been represented by seals and handwritten signatures in the past is not just one of the many factors for information security, but is the very foundation of the social infrastructure without which no social life can exist. This relation between the society and the identity verification will not change so long as humans live social lives. EPS will be a legitimate successor to the time-honored seals and handwritten signatures.
* Feature 1: The idea of using pictures for passwords is not new. It has been around for more than two decades but the simple forms of pictorial passwords were not as useful as had been expected. UNKNOWN pictures that we manage to remember afresh are still easy to forget or get confused, if not as badly as random alphanumeric characters.
EPS is new in that it offers a choice to make good use of KNOWN images that are associated with our autobiographic/episodic memories. Since these images are the least subject to the interference of memory, it enables us to manage dozens of unique strong passwords without reusing the same password across many accounts or carrying around a memo with passwords on it. Furthermore, we no longer need to manage to remember the relations between accounts and passwords because each account shows its own unique picture matrix.
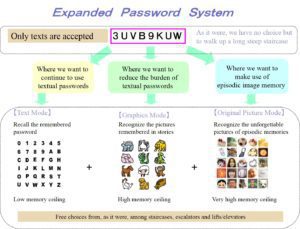
EPS is inclusive of textual as well as non-textual passwords. Users can retain the textual passwords as before while they expand their password memory to include the non-textual passwords without being impeded by the cognitive effect of “interference of memory”. It is extremely difficult to imagine the users who would suffer disadvantage or inconvenience by adopting EPS..
As for our episodic memory as the cognitive core of our personal identity, you could refer to the following sites.
– Episodic Memories and Your Experiences
https://www.verywellmind.com/what-is-episodic-memory-2795173
– The Cognitive Underpinnings of Continuous Identity
Feature 2: It is known that episodic memories are easily changeable. What we remember as our experience may have been morphed and not objectively factual. But it would not matter for EPS.
What we subjectively remember as our episodic memory could suffice. From confidentiality’s point of view, it could be even better than objectively factual memories since no clues are given to attackers.
* Feature 3: High-entropy passwords generated from low-entropy passwords
Generally speaking, hard-to-break passwords are hard-to-remember. But it is not the fate of what we remember. It would be easily possible to safely manage many of high-entropy passwords with EPS that handles characters as images.
Each image/character is identified by the image identifier data which can be any length. Assume that your password is “CBA123” and that the image ‘C’ is identified as X4s&, eI0w, and so on. When you input CBA123, the authentication data that the server receives is not the easy-to-break “CBA123”, but something like “X4s&eIwdoex7RVb%9Ub3mJvk”, which could be automatically altered periodically or at each access if required.
When such high-entropy data are hashed, it would be next to impossible to quickly crack the hashed data back to the original password. Give different sets of identifier data to “CBA123” and the different servers will receive all different high-entropy authentication data. Brute-force attacking of “CBA123” and other similarly silly passwords would perhaps take less than a few seconds with automatic attack programs with clever dictionaries but it could be an exhausting job when criminals have to manually touch/click on the display with their fingers. This function of managing strong passwords by weak text passwords is one of the secondary merits of EPS.
* Feature 4: Passwords & Corresponding Accounts
Being able to recall strong passwords is one thing. Being able to recall the relations between accounts and the corresponding passwords is another. When unique matrices of images are allocated to different accounts with EPS, those unique matrices of images will be telling you what images you should pick up as your passwords.

The Expanded Password System thus frees us from the burden of managing the relations between accounts and the corresponding passwords.
* Feature 5: What will we gain and what will we lose with EPS?
When we deploy a new solution, we often lose something while we gain something else. Does it also apply to Expanded Password System that accepts images as well as characters?
– People who enjoy handling images will gain better security and convenience. The only extra effort required is to get these images registered; but users already do that across social media platforms and seem to love it.
– People who do not love to handle images will be able to opt to keep using characters. They will not lose anything.
– People who use password management tools and single-on-sign services will gain a better security by having a more reliable master password.
– People who use multi-factor authentication for better security will gain an even better security by having a more reliable password as one of the factors.
– People who use biometrics operated together with a fallback password, which provide the level of security lower than the password alone in return for better convenience, will gain a less bad security by having a more reliable fallback password.
– Employers who have to bear the password-reset costs for their employees’ forgotten passwords will see the costs cut back drastically as the employees will now have to ask for the password-reset much less frequently.
– Employees who are held responsible for the damages when criminals grab their passwords will see the much fewer risks as the result of their not using silly passwords, not writing their passwords on paper or not re-using the same passwords across business and personal accounts.
Identity Assurance by Our Own Volition and Memory
We believe that the reliable identity assurance must be built on three prerequisite principles as follows.
- Volition of the User – with Self-Determination,
Identity authentication with no confirmation of the user’s volition would lead to a world where criminals and tyrants dominate citizens.
(2) Practicability of the Means – for Use by Homo sapiens
Mathematical strength of a security means makes sense so long as the means is practicable for us Homo sapiens.
(3) Confidentiality of the Credentials – by ‘Secret’ as against ‘Unique’.
Being ‘unique’ is different from being ‘secret’. ‘Password’ must not be displaced by ‘User ID’.
These prerequisites are especially important for Self-Sovereign Identity. Any one of them missing, it does not qualify as a valid identity authentication means. Claiming otherwise ends up with spreading a false sense of safety.
The emphasis on volition also indicates that our proposition of EPS presupposes the societies where people respect democratic values and is in return expected to support the democratic values
Identity Assurance in Emergency
How can we login reliably in a panicky situation?
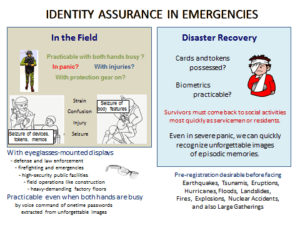
It is the obligation of the democratic societies to provide the citizens with identity authentication measures that are practicable in these emergencies. Using unforgettable images will help.
Scope of Enterprise
Multi-factor authentications and ID federations (single-sign-on services and password management tools) are operated with the password. The password is also indispensable for the biometric products operated in cyber space as a fallback means against false rejection. And yet, passwords have been hard to manage.
With billions of people suffering the same big digital headache, the problem to be addressed by our solution is huge, Substantial market opportunity is anticipated for the most practicable solutions to the issue of shared secrets for reliable identity assurance.
Specifically, without the reliable digital identity assurance, such emerging industries and critical infrastructures as below would be infeasible.
– Self-Sovereign Identity
– Electronic Healthcare
– Pandemic-resistant Teleworking
– ICT-assisted Disaster Prevention, Rescue & Recovery
– Hands-Free Operation of Wearable Computing
– Hands-Free Payment & Empty-Handed Shopping
– Humanoid Robots
– Internet of Things
And, needless to say, Cyber Defense & Law Enforcement
Readers might hopefully keep an eye on what is going on at OASIS.
Hitoshi Kokumai
President, Mnemonic Security, Inc.
About Author
Hitoshi Kokuman is the inventor of Expanded Password System that enables people to make use of episodic image memories for intuitive and secure identity authentication. He has kept raising the issue of wrong usage of biometrics with passwords and the false sense of security it brings for 16 years.
Mnemonic Security Inc. was founded in 2001 by Hitoshi Kokumai for promoting Expanded Password System. Following the pilotscale operations in Japan, it is seeking to set up the global headquarters.
Appendix – Some more topics related to identity assurance
Recent Development in Biometrics
Half year ago we felt a big shockwave to have heard a mind-boggling report of unnecessary deaths presumably brought by biometrics misunderstood from India where the biometrics; is mandatory for its Aadhaar-based Public Distribution System. There have since been intriguing new findings.
According to a report from India, actual False Acceptance Rates turned out to be 6% for fingerprints and 8.5% for iris scans in the large-scale use case of Aadhaar, which may look far higher than you have heard. And, a follow-up report says that a lock function has been introduced for the biometrics data.
By the way, the reports refer to ‘failure’ or ‘glitch’ of biometrics, but it is not necessarily correct. ‘False Rejection’ as against ‘False Acceptance’ is inherent in biometrics; there is no biometrics that is free from False Rejection. Let us explain this point closely.
A graph (*1) below shows the False Acceptance Rates (FAR) and False Rejection Rates (FRR) of two biometrics products – one relatively more accurate and the other less accurate.
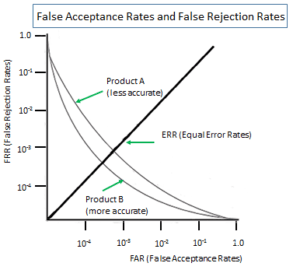
What this graph indicates is, firstly, that FAR and FRR are not the variables that are independent from each other, but are dependent on each other.
A FAR could be fixed only against a certain FRR, i.e., both variables can be positioned only at the same single point on the same single curve. In other words, the couple of a FAR and a FRR can exist only in a certain combination.
Secondly, it also indicates that the lower a FAR is, the higher the corresponding FRR is. The lower a FRR, the higher the corresponding FAR. That is, FAR and FRR are not just mutually dependent but are in a trade-off relation
The level of a FAR that rejects a twin would have to bring the level of a FRR that rejects the registered user very frequently. The level of a FRR that eliminates the need of a fallback means would have to bring the level of a FAR that accepts nearly anyone.
Thirdly, also indicated is that the more accurate the biometrics sensor becomes (the lower the Equal Error Rate becomes), the curve goes downwards/leftwards in this graph. But, when a FAR is 0 (zero), the corresponding FRR still remains close to 1 (one). When a FRR is 0 (zero), the corresponding FAR remains close to 1 (one).
Another graph (*2) helps us to grasp how FAR and FRR are mutually dependent and also in a trade-off relation.
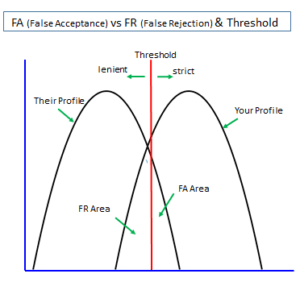
Move the threshold to the right (more strict) and we would see the combination of a lower FAR and a higher FRR. Moving it to the left (more lenient), the outcome would be the combination of a higher FAR and a lower FRR.
The presence of False Rejection, however close to 0 (zero) the rate might be, would require a fallback means against the False Rejection.
If the officials responsible for the Aadhaar-based PDS had been informed of the above, they must have provided a fallback means in case of the false rejection. Then this kind of misery could have been avoided. We have to wonder how it was possible that these people were not advised of the issue of false rejection.
The touted merits of biometrics were (a) security higher than passwords and (b) convenience better than passwords. We have been trying to demystify (a) and the actual case of Aadhaar and the like will hopefully be demystifying (b).
Thought Experiment in Two-Factor Authentication
A very strong passwords supposed to not be remembered and written down on a memo should be viewed as ‘what we have’, definitely not ‘what we remember’, so it could be used as one of the two factors along with a remembered password.
Although it may not be able to compete with a 2-factor scheme involving a PKI and OTP-based authenticator, a ‘boring legacy password system’ can be a two-factor authentication system made of ‘what we remember’ and ‘what we have’ just by verifying two passwords per access.
The merit of this plan is that the two-factor effects could be somehow achieved straightaway WITHOUT involving any costs of delivering and certifying the hardware tokens.
This kind of simple no-cost 2-factor schemes could have long been in broad use but it did not happen. We are wondering what prevented it from becoming popular. (Good security solutions come with a big price tag in many cases, so we might have taken it for granted that a solution coming with no big price tag cannot be a good solution. Was it?)
This could be viewed just as a thought experiment or could be considered for practical application between a single factor authentication and a costly heavily-armored 2-factor scheme.
What is needed in Brain-Machine-Interface
As for Man-Machine-Interface for EPS that accepts images in addition to characters, we already can rely on
– clicking and tapping on the images randomly positioned
– typing the characters randomly allocated to images
We will easily be able to rely on
– eye-tracking the images randomly positioned
– voice-recognizing the characters randomly allocated to images
– voiceless-voice-recognizing the same
– tapping secret signals on a pad when hearing the sounds that the users had registered (for the blind people)
– tapping signals when feeling the tactile sensation that the users had registered (for the blind & deaf people)
All the above can be achieved by deploying the off-the-shelf technologies. The next task is the interfaces for the people who cannot rely on any of the above. Here enters the possibility of BMI/BCI.
A simple brain-monitoring of the user’s eye-tracking has a problem in terms of security. The data, if wiretapped by criminals, can be replayed for impersonation straight away. Therefore the data should be randomized as the disposable onetime ones.
One idea is that the authentication system allocates random characters to the images. The users focus their attention on the characters given to the registered images. The monitoring system will collect the brain-generated onetime signal/data responding to these characters. If intercepting successfully, criminals would be unable to impersonate the users because the bugged data are onetime and disposable.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.


