This year as the world went crazy for World Cup soccer action, cybercriminals kicked up their game an extra notch to exploit fan enthusiasm through social engineering attacks for financial gain. Even as the tournament closed in mid-July, phishing attacks were still in full swing and ready to take advantage of fans until the very end. Russia alone was reported to be targeted for over 25 million cyberattacks during the duration of the cup. But, there’s lessons to be learned from this so we can be more prepared for next time in 2022.
The World Cup phishing problem may seem like it only targeted fans as end-users, but in reality it threatened countless organizations since employees viewed the matches on business-issued computers and phones, or personal devices over the company network. Even before the tournament began, scammers were unleashing World Cup-themed phishing pages, spam email attachments and increasingly realistic “special offers” including fake notifications of lottery winnings, spam advertisements, and even fraudulent ticket sales to lure unwary fans. In addition, the scammers became more active by installing malicious browser extensions on streaming sites which feature the soccer matches and tournament standings.
For example, during the World Cup our research team discovered numerous extensions to Google Chrome that attracted viewers by offering various options including live feeds, news updates and match highlights. In some of the more sophisticated attacks, the hackers give users an enhanced search experience that turns their browsers into TV media centers.
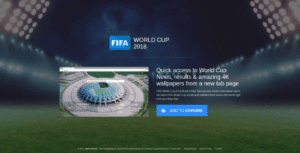
Figure 1: Screenshot of a realistic “World Cup 2018” phishing browser extension with an offer for
“Quick access to World Cup News, results & amazing 4K wallpapers from a new tab page.”
Once the user installed the malicious extension, the machine behaves as a powerful botnet used to perform distributed denial-of-service (DDoS) attacks, steal user’s data, send spam emails, or in some cases even allow the attacker to access the device.
Another malware campaign was based on click-fraud to attract downloads by promising real-time updates on all the games. Once the user clicks on “Add to Chrome,” the malicious extension was installed but users remain unaware they have ceded control for the extension to read and change their data, replace pages when opening new tabs, read their browser history and even make changes to privacy-related settings. This specific attack received over 5,000 downloads when it was live on the Chrome store, just going to show how realistic it appears to be.
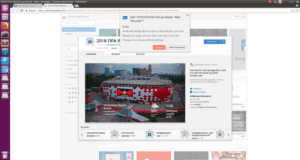
Figure 2: Phony browser extension for “2018 FIFA World Cup” news, scores and highlights.
Social engineering attacks are designed to elude software protections by deceiving employees into offering up personal credentials and/or visiting malicious web pages that compromise their machines. Such attacks rely on human fallibility to bypass existing defenses including firewalls, anti-virus protections and secure email gateways.
All these types of cyber defenses, along with email phishing training, have helped companies get better at blocking phishing emails in recent years, so the hackers have reacted by dreaming up ever-more sophisticated attacks through other vectors. Hence the proliferation of these new World Cup phishing scams.
Such “scam-in-the-browser” attacks can be used to simply commit click-fraud. However, the principal business risk involves third-parties who pay the owners of the soccer plugins for a redirect to another phishing site that dupes unsuspecting users into clicking on a link that downloads yet more malicious malware. Such partnerships enable the scammers to steal personal data or to enlist user machines in a botnet, or even more unfortunate consequences.
Many security professionals are recognizing this risk, but their organizations lack any defenses to effectively guard against such phishing attacks, so they remain vulnerable to this new wave of socially engineered attacks stemming from employee enthusiasm for the World Cup. There is only one solution to this growing problem – detecting and blocking phishing attacks before the user can reach the page behind the link and start the kill chain from which bad things happen.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



