Kaspersky Lab researchers have detected a new malware spreading through the Pirate Bay – one of the most popular torrent trackers. The malware aims to infect users’ PCs with adware and tools for additional malware installation. It has multilayered structure and due to its hidden, seemingly endless stack of functionality, the threat has been named PirateMatryoshka, after the classic Russian stacking doll.
Torrent services are mainly used for the distribution of “pirated” content that is illegal in most countries as it can infringe intellectual property rights, yet they remain easily accessible online. They are a popular target for cybercriminals looking to distribute malicious code, not least because users in search of illegal content often disconnect their online security solutions or ignore system notifications in order to install the downloaded content.
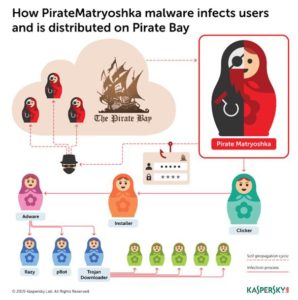
The newly discovered PirateMatryoshka malware carries a Trojan-downloader (malware that downloads malicious installers) disguised as a hacked version of legitimate software used in everyday PC activity.
The malware uses a sophisticated method of self-propagation from the social engineering point of view. While the vast majority of malicious code discovered on torrent websites is usually spread through newly set up user accounts (seeders), PirateMatryoshka malware is spread using established seeders with no known history of malicious activity. The latter makes an effective distribution process, because due to the good reputation of the seeder, potential victims have no reason to doubt that the file to be downloaded is safe.
Once a user clicks on the installer, PirateMatryoshka’s infection process begins. First, it shows the victim a copy of The Pirate Bay page that is in fact a phishing page, asking them to enter their credentials to continue the installation. Later this malware uses these credentials to create new seeders distributing more of PirateMatryoshka. The research shows that so far, the phishing link has been accessed around 10,000 times.
We can’t paste this image from the Clipboard, but you can save it to your computer and insert it from there.
Pirate Matryoshka’s scheme of infection and distribution on Pirate Bay
The infection process continues even if user credentials are not entered, with the malware unpacking further malicious modules. These include a malicious clicker that, among other things can check the ‘agree’ box that triggers the adware installer, flooding a victim’s device with unsolicited software. About 70% of installed programs are adware such as pBot, and 10% are detected as malware that can bring other malware onto the PC, such as another Trojan downloader.
PirateMatryoshka, therefore, combines sophisticated, multi-functional malware with effective distribution functionality for its own and other malicious code.
“Multi-layered malware is a very common occurrence, and we have found many cases of malicious installers who are installing more than one program on a person’s device.
“When it comes to PirateMatryoshka, however, this process is much more sophisticated. The malware that reaches a victim’s computer can then introduce additional installers, which in turn spreads even more malware. This is a very advanced type of malware, considering it is an untargeted, mass attack that carries a phishing component for wider onward distribution”, says David Emm, principal security researcher at Kaspersky Lab UK.
Kaspersky lab detects this malware as:
Trojan-Downloader.Win32.PirateMatryoshka
Trojan.Win32.InstClick
In order to protect your devices, Kaspersky Lab advises the following:
– Use only legitimate software, downloaded from official webpages.
– Pay extra attention to the website’s authenticity. Do not visit websites until you are sure that they are legitimate.
– Install reliable security solutions that securely auto-fills login credentials and provides comprehensive protection from a wide range of threats, such as Kaspersky Password Manager and Kaspersky Security Cloud
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



