According to the study ‘Financial cyber threats in 2013’ conducted by Kaspersky Lab, cybercriminals are increasingly trying to gain access to the online accounts of users. Last year, the number of cyber attacks involving financial malware increased to 28.4 million – 27.6 per cent more than 2012.
Programs designed to steal financial information include banking Trojans, keyloggers and two relatively new classes of malware – one that steals from Bitcoin wallets and another that downloads software to generate the crypto-currency. The combined activity of programs targeting Bitcoin became one of the main drivers behind the growth in financial cyber attacks in 2013. Another factor was the discovery of a number of dangerous vulnerabilities used by criminals to conduct cyber attacks via the popular Java platform.
In 2013, Kaspersky Lab security solutions protected 3.8 million users from financial attacks (an increase of 18.6 per cent year on year). Banking Trojans, including the notorious Zbot, Carberp and SpyEye programs, accounted for two-thirds of financial malware. However, compared with 2012 the share of this type of malware has fallen due to an increase in activity by malicious programs targeting Bitcoin. The proportion of keyloggers – malicious programs that intercept keystrokes – also saw a gradual decline as cybercriminals switch from these highly specialised programs to Trojans with a wide range of functions.
The proportion of financial cybercrime is greatest in Afghanistan, Bolivia, Cameroon, Mongolia, Myanmar, Peru, Turkey and Ethiopia, where this type of threat accounted for more than 12 per cent of all malware incidents.
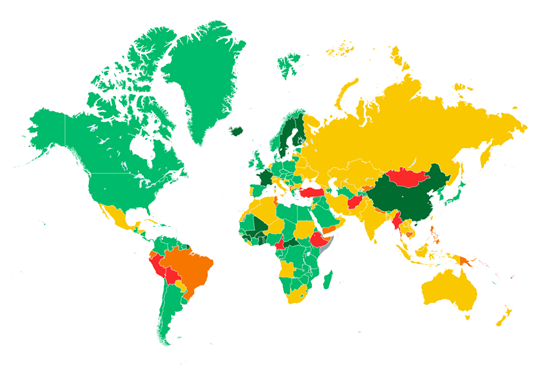
![]()
Percentage of users who encountered financial malware among the total number of users attacked by malware in 2013
There was also a lot of activity in the mobile malware segment, with 2013 seeing explosive growth in the number of mobile apps capable of stealing money from users’ bank accounts. The number of these types of threats in Kaspersky Lab’s collection grew almost 20 times throughout the year. The vast majority of attacks targeted the owners of Android smartphones.
“Last year saw a significant increase in the proportion of financial cyber threats, with malware designed to steal money playing a key role. The popularity of banking Trojans and other programs targeting financial data is due to the fact cybercriminals can use them to make money quickly. The current situation has forced users and financial institutions to take active measures against online threats, while security software vendors have to develop new protection solutions,” commented Sergey Lozhkin, Senior Security Researcher at Kaspersky Lab.
To counter financial cyber threats, Kaspersky Lab solutions for home users and small businesses integrate Safe Money technology that protects user data during online banking and online payment sessions.
Companies that provide financial online services to their clients may benefit from Kaspersky Lab’s comprehensive Kaspersky Fraud Prevention platform. It was developed to deliver rigorous, multi-layered security for online transactions: a server solution to check customer transactions as well as applications to protect users’ computers and mobile devices.
Malware is not the only method used by criminals to steal money online; phishing, or creating fake copies of sites to obtain confidential user data, is also popular. In 2013, Kaspersky Lab protection solutions blocked more than 330 million phishing attacks, of which 31.45 per cent were performed using the names of banks, online payment systems or online stores.
The ‘Financial cyber threats in 2013’ report used data obtained voluntarily from Kaspersky Security Network participants. Kaspersky Security Network is a globally distributed cloud-based infrastructure designed to quickly process depersonalised data about threats which users of Kaspersky Lab’s products encounter.
You can view the full report here: http://media.kaspersky.com/en/Kaspersky-Lab-KSN-report-Financial-cyber-threats-in-2013-eng-final.pdf
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



