The year is 2019, and I doubt anyone attending Infosecurity Show 2019 would challenge the statement ‘We live in times of Insecurity’. With a backdrop covering a spectrum of Cyber Attacks, by example, with Yahoo suffering a 3 billion record compromise back in 2013, through to the Marriott Hack circa 2014 – 2018 which exposed 500 million data assets and of course end-users. And not overlooking the Equifax debacle which exposed 145+ million customers. To top those numbers of insecurity off, consider the report made by the researcher Bob Diachenko who in May 2019 discovered an exposure associated with the Amazon AWS hosted Mongo DB database, which exposed no less than 275, 256,298 PII (Personally Identifiable Information)records of Indian Citizens – located by leverage of OSINT tools the likes of Shodan and other such freely available applications which may be employed by anyone with a moderate level of skill to discover, what are all too common Cloud insecurities leading to the acquisition and compromise of hosted golden nuggets of sensitive information assets.
When calculation is performed of the known security exposures and compromises, and then taking statistical input from the public knowns, and those unknowns that have not thus far been reported (and trust me, there are many) the numerical output is in the billions. However, what often gets overlooked with such compromises which expose PII is the forgotten potential of the Continuance of Criminal Abuse, and the illicit proffering and trading of such valuable information assets through open criminal markets, and the shady logical high-street outlets trading on the DarkWeb, which by inference gives extended life to such stolen and compromised data objects from say back in 2013 and beyond.
Based on historical facts, and my own personal research for articles and media and interviews on the BBC which have led to the discovery that there is a very high probability that end-users are not always made aware of the fact their data has been compromised, and that as such they are personally exposed through PII – for example, where the main compromised organisation is associated, supporting or hosted with other organisations who were impacted by the core hack or exposure. Or say like the WhatsApp security issue of May 2019, which was public, and yet many end users who are not blessed with being security savvy were completely unaware of the security implications, and the need to urgently update their applications – for these people their exposure continues.
Thus in a nutshell, be it a Personal User, SME (Small Medium Business) or a Corporate there is a ‘prima facie’ case for taking the dangers posed by cyber-attacks very seriously indeed, which dictates the utilisation of security platforms and tools which accommodate a robust protective layer to safeguard PII, and all other sensitive data assets – say your Bitcoin Wallet for example. In my personal case, and many others across the spectrum of data-owners, I utilise robust hand-held security platforms in the form of an iStorage encrypted drive, supporting such robust security. For example I put my trust in their FIPS 140-2 Level 3, NCSC CPA, NLNCSA BSPA and NATO Restricted Level diskAshur PRO² hosting onboard AES-XTS 256-bit hardware based encryption which may be used to secure NATO RESTRICTED Level data assets, as well as very adequate and trusted, worthy protection to remove the storage nightmare for GDPR tagged information assets. I also use the heavier desktop security solution provided by the diskAshur DT² which offers the same high-level security functionality of the diskAshur PRO², but in this case supports a storage capacity up to 14 TB of storage. OK, so that takes care of all my in-hand security needs, but there are also occasions when I need to consider my own approach with transglobal activities when visiting far flung places, or for those occasions when on vacation where I didn’t have access to my secured drives – which is why I was so very excited to hear that iStorage were releasing their proven and excellent security capabilities into the world of Cloud to enable hardware secured, managed capabilities that will bridge the conversation gap when it comes to those two disparate conversational areas of ‘Cloud’ and ‘Security’ actually fitting into the same paragraph!
The Next Generation – cloudAshur
On the 17 May 2019 I was privileged to be given a personal sneak preview by iStorage CEO – John Michael, of what was being launched at Infosecurity 2019 in London on 4th June 2019. Like all conversations that consider the concept of any secure Cloud offering, I sat down at John’s desk with my what-if hat on – and then John, who was clearly excited with what he was about to show me (and, he was excited with just cause) pulled out of his draw a very robust Thumb Drive which was hosting a 12 Key pad (See Fig 1 below). This was the start of my introduction into their new iStorage Flagship product to secure the Cloud branded as cloudAshur – a product based on their proven hardware based hard drive systems, but in this case its application was cloud centric, and turns what are, potentially insecure Cloud environments into secure and manageable trusted storage facilities.
I was introduced to cloudAshur as the perfect solution for anyone wanting to securely store, share, manage and monitor data in the cloud, where cloudAshur is designed to eliminate the security vulnerabilities that exist with cloud platforms, such as lack of control and unauthorized access, and hackers using sophisticated methods to target innocent and vulnerable users.
Looking at the actual iStorage cloudAshur Module shown below at Fig 1. The first thing you notice about this FIPS Level 3 compliant tamper proof & evident waterproofed design, is the attention to detail and quality which has been applied to the build of the component. However, it goes well beyond aesthetics as this little device is supporting real-time military grade AES-XTS or AES-ECB 256-bit Hardware Encryption with the FIPS PUB 197 certified USB 3.0 encryption controller, all of which are encased within a super tough epoxy resin to mitigate the opportunity of tampering with the onboard security components, such as its EAL4+ ready secure microprocessor. Link all this to the other inbuilt security features by design with its dedicated hardware for protection against SPA (Simple Power Analysis), DPA (Digital Power Analysis), SEMA (Simple Electromagnetic Analysis) and DEMA (Differential Electromagnetic Analysis) attacks and a host of other features, and you start to get the message that a lot of security imagination has gone into this product during its three year development cycle. But for me the absolute bottom line is, with so many rich security features, this little security tool really does feel comfortable when sitting in the palm of the hand seeking to secure their Cloud based assets.
Fig 1 – The iStorage cloudAshur Module

The real beauty of the iStorage cloudAshur Module and associated service is, you enter the Next Generation of securing the Cloud with no less than five levels of robust, conjoined security – for example:
- Something you Have – the Physical cloudAshur Module with the onboard Encryption Keys
- Something you Know – the Complex Pin which gives Logical access to the Physical cloudAshur Module and its stored Encryption Keys
- Something (else) you Know – The Login Credentials to the iStorage cloudAshur application
- Something (else) you Know – the Cloud Provider Service of choice
- Something (else) you Know – The Login Credentials for the associated Cloud Service
It could also go to another level of 6 for the very paranoid, with the additional use of a Something you Have in the form of say, a Physical Yubikey or DUO associated with a Cell Phone to give that extra level of paranoid assurance when using the common agnostic cloud.
Another great factor about this unique iStorage cloudAshur environment is, as I said, it is agnostic to the Cloud provider of choice – in other words, no matter the provider, the result is the same – secured data facilitated using Hardware Based Encryption to secure the remote data objects (the information) under the provisioned security of a robust algorithm to protect the selected personal, business or sensitive data asset.
What’s truly revolutionary about the cloudAshur is that aside from it being an ultra-secure PIN authenticated, hardware encrypted and collaborative cloud encryption module that encrypts all data in transit and at rest using a hardware-based AES-XTS 256-bit encryption key, it also comes with two applications which can help the user share and manage their data with others securely.
First up, we have the iStorage KeyWriter App (patent pending), which makes sharing of data in the cloud, via email and file transfer services (e.g. WeTransfer) between authorised users a breeze with ultimate security and peace of mind, allowing users to securely share data with one another, in real-time, regardless of their location. The iStorage KeyWriter copies all critical security parameters including the randomly generated encryption key and all PINs between the Master cloudAshur device and as many secondary cloudAshur devices as required, allowing authorised users to securely share data with one another, in real-time, regardless of their location.
OK, but after delivering all of this, what is the worst than can happen – well some passer by hacker or criminal could find a hole in some lackluster choice of Cloud, and then as if by magic they have also got access to your data – right? Wrong! What they have actually achieved is to get access to data objects which have not only been encrypted with a military grade algorithm which has turned the meaningful content into unreadable gibberish, but more is the point here, the actual keys which were used to cloak such data assets are stored and locked away on a hardware based module – hence zero compromise has taken place.
cloudAshur is also rich with many other security features and high-end security functionalities, particularly with their Remote Management console which gives the Administrator the power to apply proximity policies, granting the authorized user the rights to only operate within approved locations, countries – these policies also allow the restriction by time when an authorized user may access the protected data assets, and of course allows the cloudAshur Administrator to revoke access at the touch of a button – See Fig 2 below for the cloudAshur Remote Management console’s Dashboard.
Fig 2 – iStorage cloudAshur Dashboard
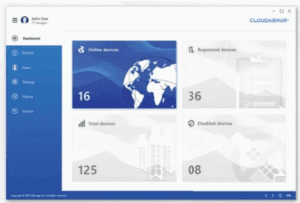
cloudAshur is clearly an enterprise-based solution – but nevertheless makes it possible for even the smallest of SME’s to enjoy serious security capabilities that were once believed to be beyond their budget. With the ability to manage remote working and connections through the cloudAshur Remote Management console, the Administrator can instantly visualise how many devices are connected and see other meaningful security information such as how many devices have been disabled (revoked).
Conclusion
In the wake of multiple security breaches, and exposures, and of course not forgetting the mandated security expectations that fall under Data Protection, the consequence of GDPR financial implications, and the impact of Adverse Press, the word Cloud does set off much debate, and associated fear. However, with the proven track record of robust, certified products, this iStorage cloudAshur creation has just delivered a real game changer, enabling the Next Generation of Personal and Business Users, with the Next Generation of Robust Security which was once considered impossible. And given this is the first release of the cloudAshur, based on the past achievements of the iStorage Team, one may only expect this new delivery to go sky-high and onward, and upward.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.


