Recently, InfoSecBuzz posted a blog post dedicated to some of the consequences of social engineering. It’s no secret that social engineers have been using various devious methods to fool people for a long time. In fact, social engineering is advancing with the times and becoming increasingly reliant on the technology that has become an integral part of our lives. Social engineering attacks against mobile devices (i.e smartphones and tablets) are a perfect example of this.
Social engineering can have a vast range of implications on mobile security (Android & iOS) both in enterprise and personal surroundings. In a series of detailed articles, we present examples different methods of mobile social engineering attacks and discuss the various implications they’ve had on targeted organizations.
As a start, let’s take a look at Ransomware – staking its claim as one of the major attack trends. Ransomware is a type of malware that either locks the victim out of their device and/or holds data hostage, until the attacker receives a ransom fee. Several variations of ransomware exist (whether for mobile or PC)- from popups that take over the victim’s screen, to more advanced malware that actually encrypts the victim’s data. Both demand payment from victims in order to release the device.
During the month of May, two major ransomware campaigns began spreading:
Koler – a strain of malware that targets mobile users viewing pornography on their Android devices. It tries to scare its victims into paying the $300 ransom by claiming the victim has viewed “illegal pornography” and posts a threatening message from a fake law enforcement agency (that cleverly changes depending on the victim’s location). 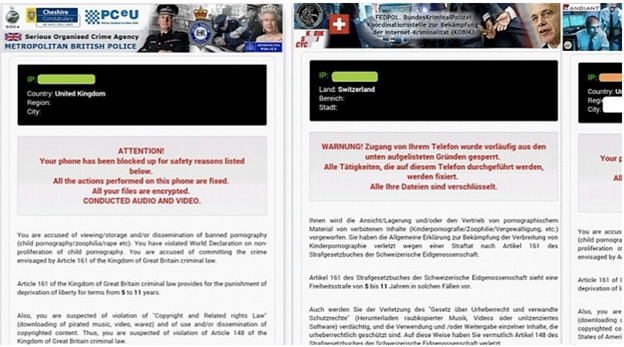 SimplLocker – scans the SD card for certain file types, encrypts them, and demands a ransom in order to decrypt the files. The victims receives this alarming message in Russian, while their files are being encrypted.
SimplLocker – scans the SD card for certain file types, encrypts them, and demands a ransom in order to decrypt the files. The victims receives this alarming message in Russian, while their files are being encrypted.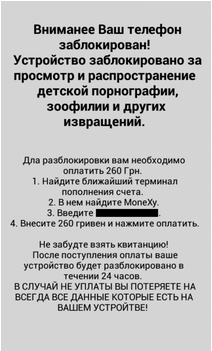
Although both attacks are relatively simple to mitigate and far from the most advanced threat enterprises face – the point is that they work. A significant percentage of mobile user fall for these attacks. Whether it’s ransomware attacks like these, or other types of social engineering like fake apps, malicious ads and rogue wifi hotspots – they will fool your average user.
For an organization, this means that prevention of social engineering is not 100% possible – there’ll always be that one single employee who accidently fell for one of the scams. As a result, organizations are left to mitigate the results of a compromised device on their network. Making sure your enterprise is prepared for social engineering attacks is probably the most important thing.
Our CTO, Ohad Bobrov recently released a series of articles on the different categories of mobile social engineering attacks. The series touches all the major types of attack – explaining how they work, as well as providing relevant examples of each, and most importantly, how to mitigate.
The first post in the series can be found here: Social Engineering – Why mobile users are their own worst enemy
I also recommend reading Ohad’s post on how enterprises can mitigate the effects of a social engineering attack in the final post of the series.
Yonni Shelmerdine, Lacoon
 Yonni is the lead Mobile Security Trends Analyst at Lacoon. Yonni brings 5 years of experience in Datacom & GSM network security analysis from an elite unit in Israel’s Intelligence Corps. Yonni heads the analysis of mobile attack trends wherehe researches new attack vectors and identifies major mobile malware attack patterns. Juggling university, work and football isn’t easy, but Yonni is a master in multi-tasking.
Yonni is the lead Mobile Security Trends Analyst at Lacoon. Yonni brings 5 years of experience in Datacom & GSM network security analysis from an elite unit in Israel’s Intelligence Corps. Yonni heads the analysis of mobile attack trends wherehe researches new attack vectors and identifies major mobile malware attack patterns. Juggling university, work and football isn’t easy, but Yonni is a master in multi-tasking.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.