Many equate DDoS with only one type of attack vector – volumetric. It is not surprising, as these high bandwidth consuming attacks seem to frequent the headlines most often. Volumetric DDoS attacks are easier to identify, and defend against with on-premises or cloud anti-DDoS solutions, or a combination of both.
But DDoS attacks are not always volumetric. Recently, Corero Network Security identified a change in the way attackers are using DDoS as a mechanism to target corporate enterprises, hosting providers, and Internet service providers: not only are they using brute force multi-vector DDoS attacks, but they have also started to implement more adaptive methods to profile the nature of the target network’s security defenses, subsequently selecting a second or third attack designed to circumvent the layered protection the target has in place.
Featured Download: Social media access at work. Do your employees know the rules?
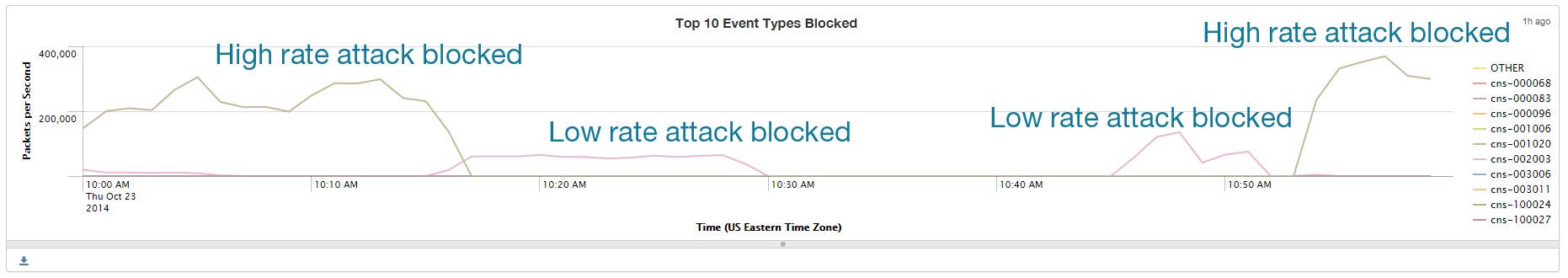
Outlined below is an example of an actual attack intruders are using. The charts show an initial SYN flood attack (IP addresses have been removed to protect the organization concerned). This attack is easily blocked by the Corero SmartWall® Threat Defense System (TDS). The initial attack lasts approximately 15-20 minutes and is a very high capacity attack. After 20 minutes, the attacker backs off the volumetric attack and initiates a second attack at a much lower threshold. Eventually, many security platforms would allow the traffic through because it looks more like normal threshold TCP traffic. However, the SmartWall TDS recognizes and blocks this second attack by utilizing intelligent and flexible filtering and behavioral techniques to understand the nature of the attack pattern.
These partial saturation attacks have sufficient capacity to take down Firewalls, IPS’s, Web Application Servers and back-end infrastructure without saturating the pipe. To achieve a level of intelligence and real-time mitigation against this type of DDoS attacks, networks need a Corero First Line of Defense solution in place. Without it, the victim organisation would have to constantly monitor and create filters and signatures on the fly with the help of a human security analyst. Indeed, detecting these attacks utilising a cloud-based model is an expensive proposition, not to mention all the effective delays in actually mitigating the attack the victim would incur.
Organisations must arm themselves with next generation DDoS defense platforms that incorporate both intelligent and automated filtering and detailed security forensics to effectively defeat these new advanced evasion threats.
By Bipin Mistry, Vice President of Product Management, Corero Network Security
About Corero Network Security
![]() Corero Network Security is dedicated to improving the security of the Internet through the deployment of its innovative First Line of Defense® solutions. Corero products and services provide our customers with protection against a continuously evolving spectrum of DDoS attacks and cyber threats that have the potential to impact any Internet connected business. Corero provides the opportunity to enhance defense-in-depth security architectures with an important additional layer of security capable of inspecting traffic arriving from the Internet in real time and applying access policies designed to match the needs of the business.
Corero Network Security is dedicated to improving the security of the Internet through the deployment of its innovative First Line of Defense® solutions. Corero products and services provide our customers with protection against a continuously evolving spectrum of DDoS attacks and cyber threats that have the potential to impact any Internet connected business. Corero provides the opportunity to enhance defense-in-depth security architectures with an important additional layer of security capable of inspecting traffic arriving from the Internet in real time and applying access policies designed to match the needs of the business.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.