It’s tax time and the IRS is ready to receive your small business’ information from the past year. Can you guess who else is waiting for you to file, probably even more eagerly than the federal and state governments?
Tax time is a busy and lucrative time for identity thieves. In 2014, over 100 million tax returns were filed electronically (efile.com). Considering 1 in 5 computers are not properly protected against cyber attacks, there will be about 20 million easy targets out there this tax season for hackers looking to make some easy money. In addition, there were almost 800 data breaches in 2014 in which confidential customer data was stolen from businesses across the U.S. by means of malware, phishing scams and even lost or stolen flash drives and other storage devices.
It is important for you to be aware of potential dangers whether filing through your internal accountant, or through a tax professional. Here are some ways to ensure you aren’t an easy target for tax time cyber crime.
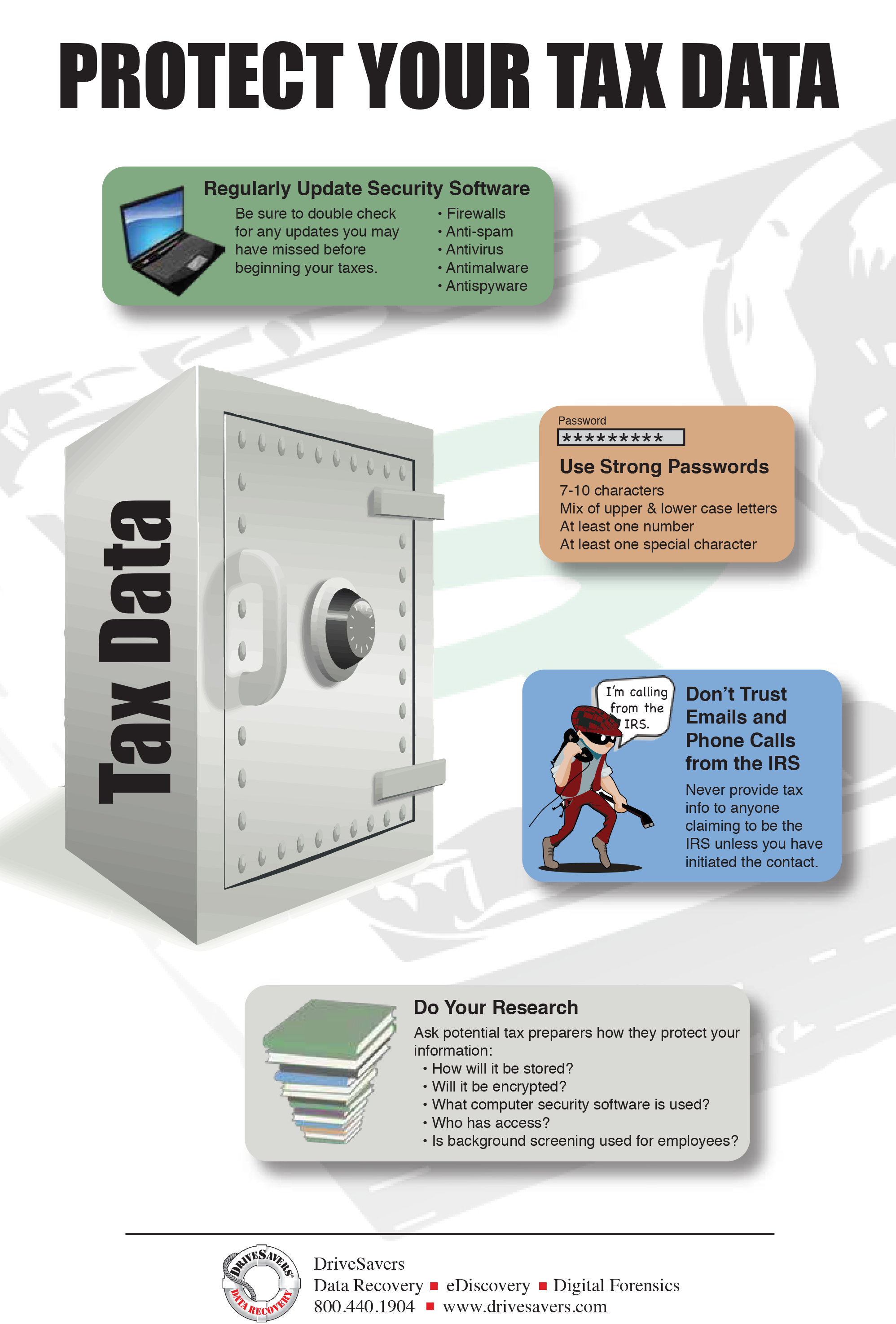
Regularly Update Security Software
Hackers are always exploring computer security measures to find weaknesses and develop ways in. In reaction, security software manufacturers are constantly developing patches and software updates to eliminate threats as they are discovered. If you don’t keep up with software and operating system updates, these known weaknesses remain like open doors inviting criminals into your computer.
Identify what firewalls, anti-spam, antivirus, anti-malware and anti-spyware software you have installed and always install updates, as they are made available. In addition, be sure to double check for any updates you may have missed before beginning your taxes.
Use Strong Passwords
Weak passwords are an easy way for someone to access your personal data. Here are some good tips to follow when creating passwords:
- Passwords should be at least 7-10 characters long
- Don’t use a number series like 1234 or 4321
- Don’t use the names of children or pets
- Don’t use birthdays
- Include a mix of upper and lower case letters
- Include at least 1 number
- Include at least 1 special character
- Don’t use single dictionary words (spelled forward or backward)
- Don’t use character substitution for dictionary words (like p@$$worD)
- Use a string of 3 words “smushed” together that are meaningful to you so you can easily remember your password without having to write it down and refer to it
- Good password example: 3wOrdSmushedTo{gether
- Bad password example: P@ssword123
It’s vital to use different passwords for each account and change them every few months. Otherwise, a hacker only needs to crack one to have access to everything. A good password manager program can keep this from being overwhelming.
Don’t Trust Emails and Phone Calls from the IRS
Don’t ever provide your personal information to anyone claiming to be the IRS unless you have initiated the contact. As stated on the IRS website, “The IRS doesn’t initiate contact with taxpayers by email, text messages or social media channels to request personal or financial information.”
Be sure to report any unsolicited email or phone calls claiming to be from the IRS to phishing@irs.gov.
Do Your Research
Research your tax preparer or the tax-preparation software you choose to use.
Don’t ever download any software without visiting trusted review sites and researching its legitimacy. Otherwise, you may accidentally download software designed for the purpose of stealing your personal information or damaging your computer.
Ask potential tax preparers how they protect your information:
- How will it be stored?
- Will it be encrypted?
- What computer security software is used?
- Who has access?
- Is background screening used for employees?
Additional Tips
- When filing your own taxes, use your own computer—do not use a public or work computer.
- Never file taxes on a computer that other staff has access to and may unknowingly download malicious software.
- Never file taxes over public Wi-Fi networks—only use secure networks.
- Once your return has been filed, burn the file to a CD and remove the personal info from your hard drive. Store the CD in a lock box or safe.
By Michael Hall, CISO and Director of eDiscovery and Digital Forensics,DriveSavers
 Bio: As Chief Information Security Officer (CISO) and Director of eDiscovery and Digital Forensics, Michael Hall directs and implements policies and procedures concerning the privacy and security of all data received at DriveSavers, including highly critical data from government agencies, major corporations and research laboratories. Hall was instrumental in helping NIST, FDIC, OTS and BITS identify the risks of improper screening of data recovery providers.
Bio: As Chief Information Security Officer (CISO) and Director of eDiscovery and Digital Forensics, Michael Hall directs and implements policies and procedures concerning the privacy and security of all data received at DriveSavers, including highly critical data from government agencies, major corporations and research laboratories. Hall was instrumental in helping NIST, FDIC, OTS and BITS identify the risks of improper screening of data recovery providers.
In his previous role as Director of PC Engineering, Michael developed security protocols to handle critical and encrypted data for corporate and government accounts. He also developed and managed the ISO Class 5 certified Cleanroom, the largest and most technologically advanced in the data recovery industry. Hall has over 17 years experience in data recovery technology, focusing on high-end arrays, and has successfully recovered data from over 15,000 storage devices. Michael Hall has been trained and certified by the leading encryption vendors and is a certified eDiscovery and forensic investigator. Prior to joining DriveSavers in 1995, Hall was a Data System Engineer for the U.S. Navy. His responsibilities included computer hardware and software support for Intelligence Gathering Platforms.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.