A new and alarming TLS/SSL vulnerability was discovered – FREAK. The vulnerability allows for a “man in the middle” attack by tricking the user and the server into accepting a weak version of HTTPS encryption.
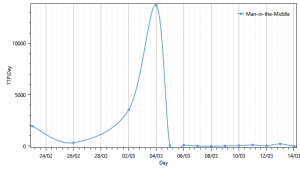
It is interesting to see the impact the vulnerability publication had on different attack methods, MitM included, and attacker behavior.
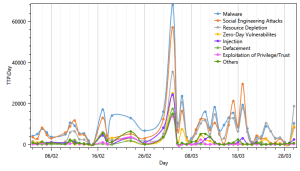
The sudden spike in activity for most attack methods can be explained by claiming that attackers often choose to test their capabilities and take advantage of the panic and shift in focus of security teams during the publication of such major vulnerabilities. As such, security teams should be aware of this pattern and better allocate their defenses for future vulnerability publications, not only against the new discovered vulnerability.
Effect on all attack methods
Effect on MitM
About Cytegic
Cy-te-gic /pronounced: sʌɪ-ˈtē-jik/ adjective: A plan of action or strategy designed to achieve a long-term and overall successful Cyber Security Posture Optimization – “That firm made a wise Cytegic decision”.Cytegic develops a full suite of cyber management and decision-support products that enable to monitor, measure and manage organizational cyber-security resources. Cytegic helps organization to identify threat trends, assess organizational readiness, and optimize resource allocation to mitigate risk for business assets.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.