High Frequency, Long Duration, Repetitive Attacks from DDoS-for-Rent Tools Becoming More Common; Cost of Mounting Attacks Drops as a Result
Imperva, Inc. (NYSE: IMPV), committed to protecting business-critical data and applications in the cloud and on-premises, today released its Q2 2015 Global DDoS Trends Report. The report findings, based on over 3,000 mitigated DDoS attacks and 60 million blocked bot sessions across all sites which were protected using Imperva Incapsula, show a high frequency and long duration of DDoS attacks against organizations during the period from March 1 through May 7, 2015.
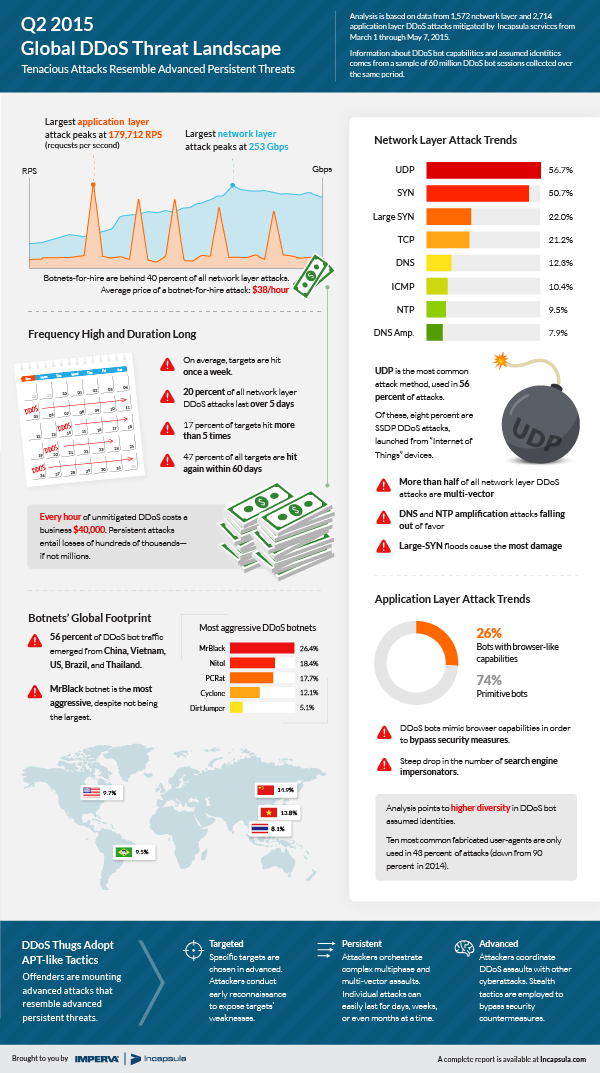
The report also details DDoS attacks that are beginning to resemble advanced persistent threats, evidenced by long durations, repetition and changing attack vectors aimed at evading simple, signature-based defense systems. At the other end of the spectrum, there is increased evidence that inexpensive botnet-for-hire services are being used to perpetrate attacks. With these tools costing as little as $19.99 per month, and available for online purchase using Bitcoin, the barrier to mounting attacks has dropped significantly.
Key report findings include:
- Some companies face advanced, persistent DDoS. The longest attack seen during the research period was 64 days, with many other sustained attempts to bring down sites observed. The researchers also noted a shift in DDoS bot populations, with more and more impersonator bots assuming non-generic identities, in an effort to bypass rudimentary signature-based security solutions. The long durations and advanced, signature evading methods suggest DDoS is beginning to resemble advanced persistent threats, also known as APTs.
- Companies that are attacked will likely be attacked again. Once targeted by an application layer attack, a website will likely be attacked again once every 10 days on average, with 17 percent of sites attacked more than five times, 10 percent attacked more than 10 times, and several sites that were attacked every day, during the 72-day research period.
- DDoS attacks may continue for a sustained period. During the research period, seventy-one percent of all network layer attacks lasted under three hours, and over 20 percent last over five days.
- Cheap ”botnet-for-hire” services endanger a growing percent of the Internet ecosystem. Short, single-vector attacks associated with botnet-for-hire services accounted for approximately 40 percent of all network layer attacks during the research period.
“Compared to just a few years ago, the frequency, sophistication and duration of attacks have noticeably increased based on our findings in the Q2 2015 Global DDoS Trends Report,” said Marc Gaffan, general manager for the Incapsula service at Imperva. “Professional hackers are mounting advanced attacks that are now resembling advanced persistent threats. We believe that this increased sophistication is due to attackers studying how DDoS mitigation solutions detect and block attacks and implementing new techniques to attempt to bypass them. As a result, it’s important for enterprises of all sizes to understand the risks DDoS attacks pose and create a readiness plan.”
Download Full report here.
[su_box title=”About Imperva” style=”noise” box_color=”#0e0d0d”]
Imperva (NYSE: IMPV), is a leading provider of cyber security solutions that protect business-critical data and applications. The company’sSecureSphere, Incapsula and Skyfence product lines enable organizations to discover assets and risks, protect information wherever it lives – in the cloud and on-premises – and comply with regulations. The Imperva Application Defense Center, a research team comprised of some of the world’s leading experts in data and application security, continually enhances Imperva products with up-to-the minute threat intelligence, and publishes reports that provide insight and guidance on the latest threats and how to mitigate them. Imperva is headquartered in Redwood Shores, California. For more information visit here www.imperva.com[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.