Wolfgang Kandek CTO of Qualys has posted his commentary on June’s Patch Tuesday
Halfway through the year and this month we have eight bulletins bringing the total count for the year to 63. Four of the bulletins address Remote Code Execution (RCE) vulnerabilities and one covers a publicly disclosed kernel vulnerability that has not seen any exploits yet. Weirdly enough there is a “hole” in Microsoft’s lineup and one bulletin, MS15-058 is apparently not ready to be released yet.
Internet Explorer (IE) is in the top spot of our recommendations this year as it has been for the last 12 months with the occasional exception of more urgent 0-days in Microsoft and Adobe products. The reason is that security researchers continue to report a large number of vulnerabilities in IE – on average over 20 per month:
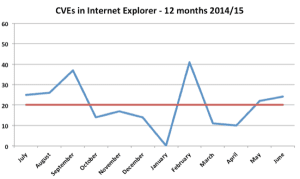 Attackers can reverse engineer these vulnerabilities by comparing before and after images of the browser and then develop exploits for the most promising (most stable) ones. One thing you can do to defend yourself against these type of exploits is to patch quickly – we recommend to apply IE bulletins within a week to be ahead of the attackers. For details on how attackers rollout exploits take a look at Microsoft latest SIR report which analyzes development and deployment timelines for MS14-064 from late last year.
Attackers can reverse engineer these vulnerabilities by comparing before and after images of the browser and then develop exploits for the most promising (most stable) ones. One thing you can do to defend yourself against these type of exploits is to patch quickly – we recommend to apply IE bulletins within a week to be ahead of the attackers. For details on how attackers rollout exploits take a look at Microsoft latest SIR report which analyzes development and deployment timelines for MS14-064 from late last year.
 But back to 2015: MS15-056 is this month’s cumulative update for Internet Explorer (IE) and it fixes 24 vulnerabilities. This including 20 critical flaws that can lead to RCE which an attacker would trigger through a malicious webpage. All versions of IE and Windows are affected. Patch this first and fast.
But back to 2015: MS15-056 is this month’s cumulative update for Internet Explorer (IE) and it fixes 24 vulnerabilities. This including 20 critical flaws that can lead to RCE which an attacker would trigger through a malicious webpage. All versions of IE and Windows are affected. Patch this first and fast.
Our second priority is MS15-059 for Microsoft Office that affect all current versions 2007, 2010 and 2013. The attacker needs to trick the target into opening a malicious file with Word or any other Office tool and can then take control of the target’s computer. Microsoft rates this bulletin as “important” but nevertheless we make it one of our higher priority patches. The fact that one can achieve RCE, plus the ease with with an attacker can convince the target to open an attached file through social engineering make this a high risk vulnerability.
On the third spot is Adobe Flash. This month’s patch addresses 13 vulnerabilities, four of them rated critical. Again Adobe Flash is often abused by attacker’s due to its flexibility and programming power, so make this patch APSB15-11 a high priority to fix. If you run Google Chrome or IE10/11 you have a bit less work as these browsers take care of the Flash patching for you. For other browsers such as Firefox or Opera or Safari on the Mac install the Flash patch by hand.
The next bulletins to address are MS15-057 and MS15-060. Both are rated critical and can be used to take control of the target system. MS15-057 addresses a vulnerability in Windows Media Player, which an attacker can use by serving a malicious media file to the target. Playing that file which can happen through the web or as an attachment causes the exploit code to run and gives full control to the attacker. MS15-060 is a vulnerability in the common controls of windows which is accessible through Internet Explorer Developer Menu. An attack needs to trigger this menu to be successful. Turning off developer mode in Internet Explorer (why is it on by default?) is a listed work-around and is a good defense in depth measure that you should take a look at for your machines.
The remaining vulnerabilities cover local Kernel problems in Windows in MS15-061 and MS15-063 and server side problems in MS15-062 which provides a fix for ADFS and MS15-064 which addresses flaws in Microsoft Exchange Server, all located in the Outlook Web Access component.
As always patch quickly, overall in less than two weeks if you can. Next month prepare for more work as you will get Oracle patches in addition to your normal fare of Microsoft and Adobe.
[su_box title=”Wolfgang Kandek, CTO, Qualys” style=”noise” box_color=”#0e0d0d”]
Qualys, Inc. (NASDAQ: QLYS) is a pioneer and leading provider of cloud security and compliance solutions with over 7,700 customers in more than 100 countries, including a majority of each of the Forbes Global 100 and Fortune 100. The Qualys Cloud Platform and integrated suite of solutions help organizations simplify security operations and lower the cost of compliance by delivering critical security intelligence on demand and automating the full spectrum of auditing, compliance and protection for IT systems and web applications. Founded in 1999, Qualys has established strategic partnerships with leading managed service providers and consulting organizations including Accenture, Accuvant, BT, Cognizant Technology Solutions, Dell SecureWorks, Fujitsu, HCL Comnet, InfoSys, NTT, Tata Communications, Verizon and Wipro. The company is also a founding member of the Cloud Security Alliance (CSA).[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



