Cyber criminals frequently move their infrastructure. Domains stay online for a few days or hours, which makes it challenging for defenders to leverage security tools that rely on blacklists and other known-bad indicators. Damballa’s Threat Discovery Center has been monitoring Pony for eight months, and has captured all instances. We’re releasing statistics that show the evolution, strategy and tactics of how criminals keep their infrastructure on the move.
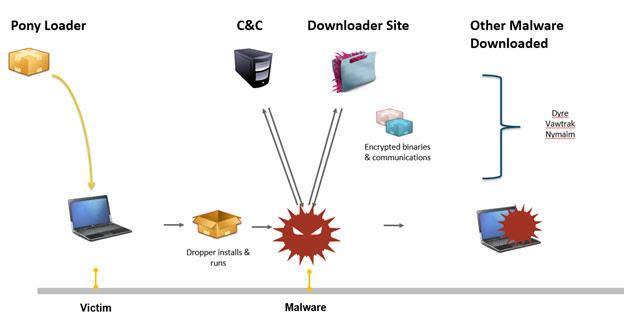
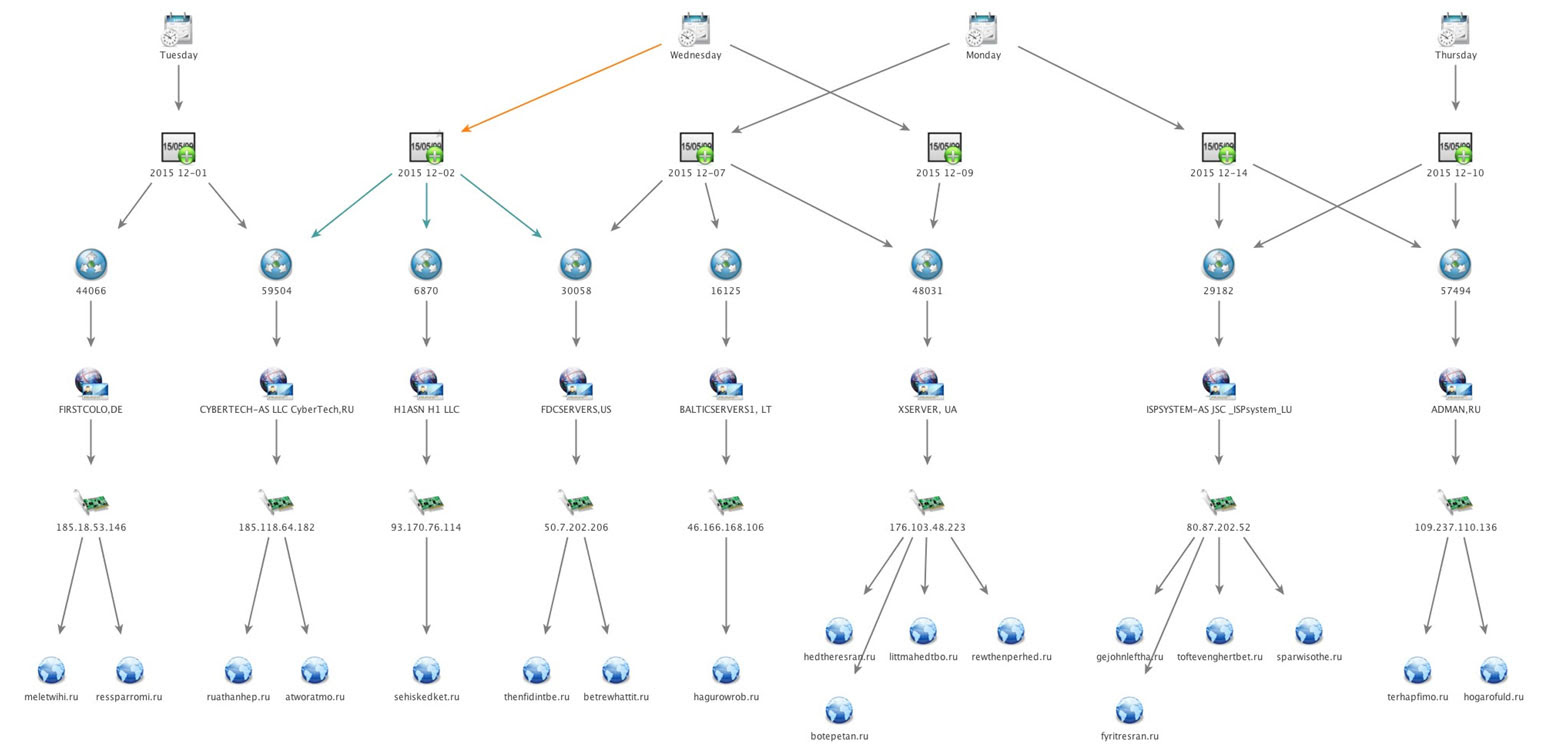
The multi-stage Pony infection chain is as follows:
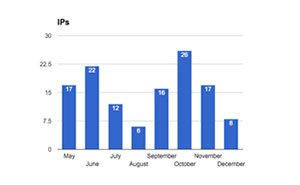
 Since we began tracking Pony, the criminals have used 281 domains and more than 120 IPs hosted on over 100 different ISPs.
Since we began tracking Pony, the criminals have used 281 domains and more than 120 IPs hosted on over 100 different ISPs.
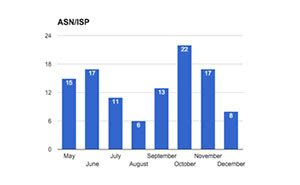
A review of domains per month shows a slow start in May followed by a peak in July, with 45 domains. In July and August, although the number of IPs decreased, the number of domains rose significantly compared to the previous months.
Even Criminals Take Vacation
The decrease of IPs in July and August is likely explained by something as common as summer vacation in Europe – yes, even criminals take some time off. The rest of the crew were heavily using the few IPs they had while waiting for their cohorts to return. In September, the behavior gains momentum with more IPs used with several different ISPs.
Criminals use only a few IPs per provider to stay under the radar and limit their chance of getting caught.
May – June 2015
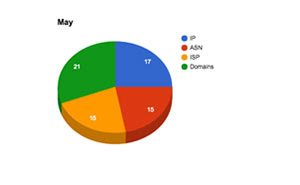
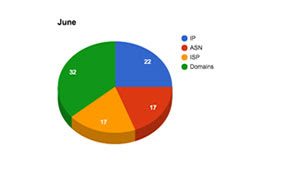
Here is a more detailed breakdown for May and June. In this early stage, the criminals establish their infrastructure and process for Pony campaigns.
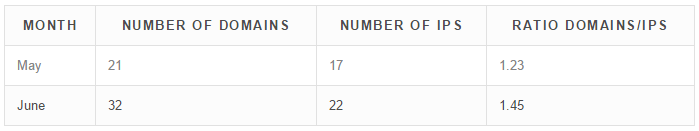 A breakdown of July, August and September shows interesting behavior. We assume that in July and August criminals had less resources to take care of the infrastructure, which involves getting new IPs and preparing new servers on different ISPs. There were 45 domains in July and 39 in August. The domains were divided over 12 IPs in July and over 6 IPs in August. This gives us a ratio of 6.5 domains per IP in August, twice as much as July.
A breakdown of July, August and September shows interesting behavior. We assume that in July and August criminals had less resources to take care of the infrastructure, which involves getting new IPs and preparing new servers on different ISPs. There were 45 domains in July and 39 in August. The domains were divided over 12 IPs in July and over 6 IPs in August. This gives us a ratio of 6.5 domains per IP in August, twice as much as July.
July and August are summer vacation season in Europe so could explain why the number of IPs is so low. Looking ahead to September, we see the number of IPs rise. In September, the criminals used 45 domains over 16 IPs, a ratio of 2.81 domains per IP.
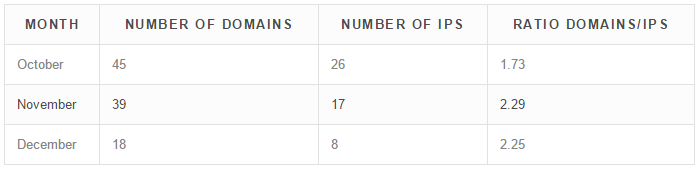
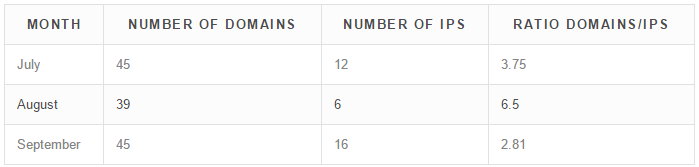 October – November – December
October – November – December
October also has very high numbers, 45 domains divided over 26 IPs, a ratio of 1.36 domains per IP. Note also the number of ISPs used is almost a 1 for 1 with the number of IPs. This is the highest number of IPs we tracked so far. In November, criminals created 39 domains divided over 17 IPs, a ratio of 2.29 domains per IP. The action is slowing down in December; we show 18 domains for 8 IPs. This could be due to vacation season or some switch in personnel. If they keep consistent, we should observe around 36 domains and 16 IPs by the end of December.
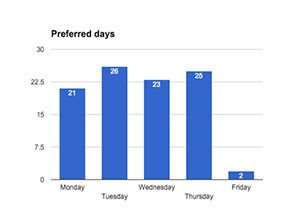
 Days and Ratio
Days and Ratio
Below is a graphic of the most used days and ratio. Why do we mention days? Because the pattern shows that criminals release Pony on certain days only; typically not Fridays. Our assumption is they use Friday to prepare for the following week or to have a three-day weekend. They’ve missed a few Mondays but generally, activity is consistent Tuesday-Thursday. Also consistent is the ratio domains versus IPs over the past eight months. The red line shows the average ratio of domains versus IPs.
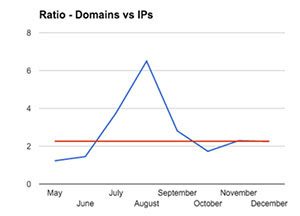
Interesting notes
We noticed some interesting points within the Pony campaign data. In May, they started to configure the Pony malware to download Dyre, a banking trojan. On September 17, they switched to Vawtrak, another banking trojan. On December 14, they turned to Nymain, a form of ransomware. Here are chronological events:
- September 17th switched to Vawtrak instead of Dyre
- December 2nd switched to Nymaim, instead of Vawtrak
- December 14th switched to Vawtrak instead of Nymaim
Besides criminals switching malware here and there, they have re-used 2 IPs that were used months ago. This tells us that they kept some IPs they had and are re-using when needed.
Conclusion
This particular criminal group is very organized and have their procedures well set up to be consistent for several months. They are able to propagate widely and remain under the radar through a structured routine that includes consistently creating several new domains and establishing new infrastructure, thus making sure their new Pony malware is undetectable by most of security products.Their use of several bulletproof hosters, or providers located in non-cooperative countries, gives them an advantage to remain online long enough to switch to different providers.
We strongly believe that in order to be able to use different Pony CnC so frequently, the criminals have a back-end infrastructure they use to combine all the information stolen with Pony. This infrastructure gives them the flexibility to move around their Pony network without any downtime. Even criminals have to make sure not to become a victim of data loss. Finally, it appears that the Pony gang typically works a four-day work week: a work-life balance appears to be important to this organization.
[su_box title=”About Damballa” style=”noise” box_color=”#336588″] As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
As a leader in automated breach defence, Damballa delivers advanced threat protection and containment for active threats that bypass all security prevention layers. Born for breach defence, Damballa rapidly discovers infections with certainty, pinpointing the compromised devices that represent the highest risk to a business, and enabling prioritized response and refocusing of security experts to the areas of greatest risk to an enterprise. Our patented solutions leverage Big Data from one-third of the worlds Internet traffic, combined with machine learning, to automatically discover and terminate criminal activity, stop data theft, minimize business disruption, and reduce the time to response and remediation. Damballa protects any device or OS including PCs, Macs, Unix, iOS, Android, and embedded systems. Damballa protects more than 400 million endpoints globally at enterprises in every major market and for the world’s largest ISP and telecommunications providers.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.


