Recently, the Norse DarkWolf Labs noted that the IP address 218.77.79.43 had jumped into the top quadrant for malicious activity. Investigation into the activity and the IP itself highlights the many challenges in accurately attributing such events to known actors, as illustrated in this article.
The IP – assigned to the CHINANET-HN-HY CHINANET-HN Hengyang node network, Hunan Telecom on ASN 4134 for China Telecom – had been seen targeting multiple ports and protocols over several months, and had been increasing activity in the last week of August.
Featured Download: CISO Data Breach Guide
From June 11, 2014 to August 26, 2014 the Norse threat intelligence platform observed over 706,000 events from this IP, with between 7,200 and 10,600 unique events each day. There had been minimal variance in the number of observed events from Thursdays through Mondays, and the total number for Tuesdays and Wednesdays were significantly less by comparison during that time frame.
The number of events gradually increased over the following weeks, with over 70,200 during one week alone:
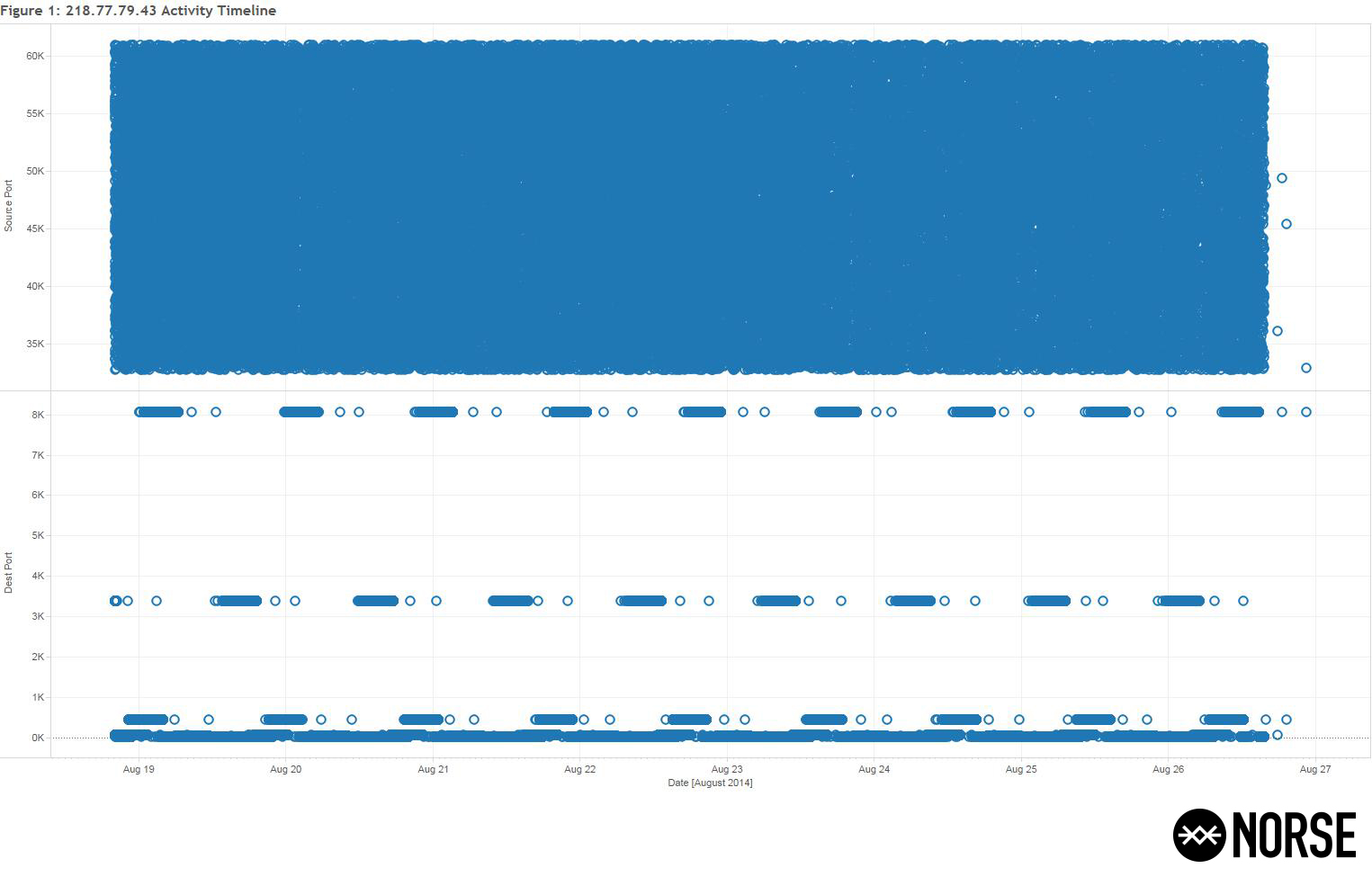 Figure One (1): 218.77.79.43 activity timeline, August 2014
Figure One (1): 218.77.79.43 activity timeline, August 2014
The source port selection is in the 32,000 to 62,000 range for this activity, with the destination having a consistent pattern targeting nine distinct ports (21, 22, 23, 25, 53, 80, 443, 3389, and 8080) as displayed in Figure Two (2). Note the number of events targeting each port are relatively equivalent:
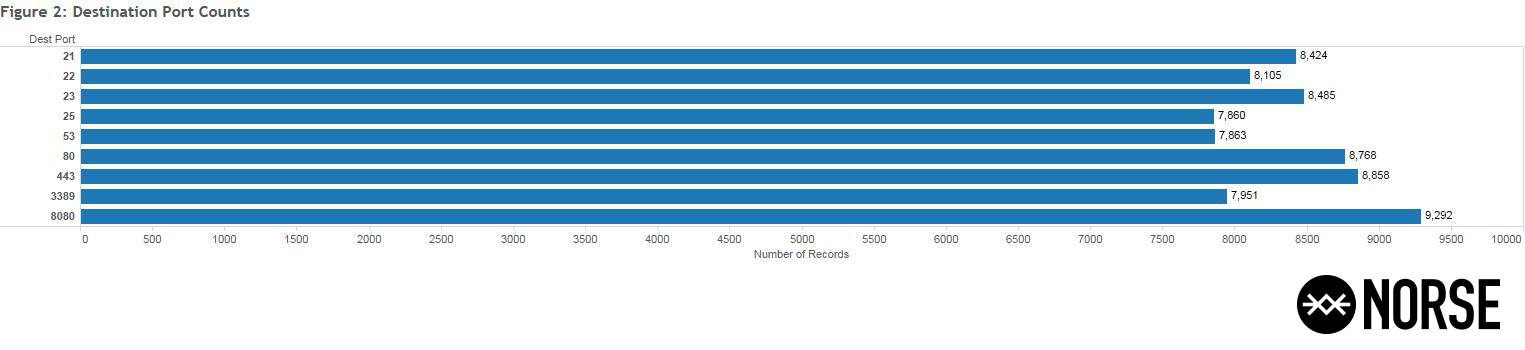 Figure Two (2): 218.77.79.43 destination port breakdown, August 2014
Figure Two (2): 218.77.79.43 destination port breakdown, August 2014
The activity observed indicates multiple timed and ongoing scans were occurring, with overlapping activity on the other targeted ports. The scans occurred over a six-hour interval with subsequent bursts detected a few hours later.
Figure Three (3) shows a detailed view of the targeted destination ports below 1024, which display distinct patterns:
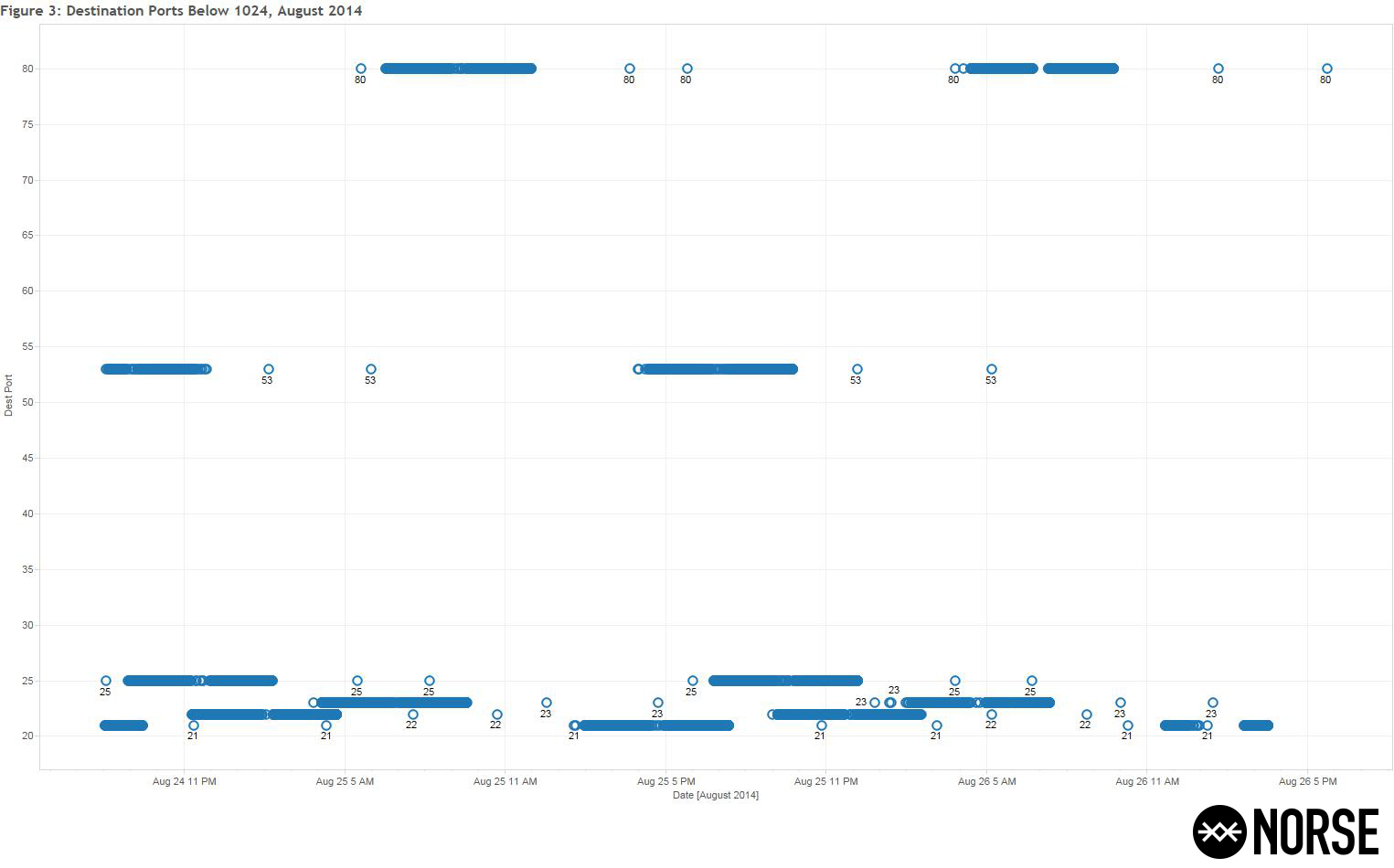 Figure Three (3): Destination Ports below 1024, August 2014
Figure Three (3): Destination Ports below 1024, August 2014
Further investigation revealed that the IP 218.77.79.43 creating this activity had been the subject of quite a bit of chatter and documentation across the Web. Researching the IP might leave one with the impression that this was merely a Linux system with only SSH open – as was seen when it was scanned by another researcher on August 14th. This appears to be an older and not updated Linux system, considering OpenSSH 5.3 was released on October 1, 2009.
The IP in question had been submitted forty-three times to URLQuery since June 17th, 2014, with many instances showing IDS hits for being on the DShield Block Listed Source group. DShield shows similar activity starting around the same time in mid-June of 2014. The IP is also listed on ips.backscatterer.org as well as on blockedservers.com and badips.com.
This is not the first time our researchers have found a system with no public facing resources or protocols that was scanning the rest of the Internet in a systematic fashion – nor will this be the last. There are few barriers to prevent an individual or organization from setting up a system and using open source toolsets to systematically scan and attack the rest of the Internet, as long as they have an “understanding” hosting provider.
Considering the sudden increase activity has been ongoing since mid-June, it is a good assumption that the Hengyang node network of Hunan Telecom on ASN 4134 for China Telecom is being quite lenient about this customer’s activities.
Following our first examination of this malicious IP, Norse DarkWolf Labs noted that 218.77.79.43 continued to hold the top spot for malicious activity, with over 66,550 events between August 26 and September 2.
Though the total events observed during this period reflected a slight decrease in observed activity from the previous week, this IP was most certainly continuing to target multiple ports and protocols, as it had been doing over the last few months.
Figure Four (4) focuses on the destination port timeline and frequency, showing the intervals of activity targeting the respective ports and protocols over this second sample period:
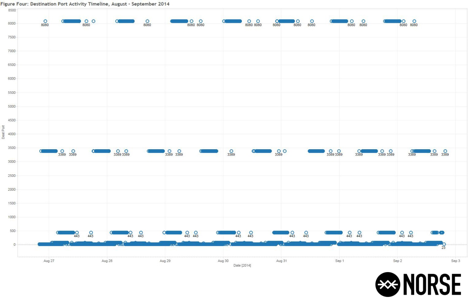 Figure Four (4): Destination Port Activity Timeline, August – September 2014.
Figure Four (4): Destination Port Activity Timeline, August – September 2014.
In one of the subsequent online conversations regarding our early analysis, one security professional expressed concern regarding all traffic from this ISP, and considering CHINANET is the sole ISP for the entire country, it makes any subjective analysis quite problematic.
DarkWolf Labs found that limiting the analysis to the specific Autonomous System (AS) Number 4134 proved quite interesting, with 2,981,300 events observed from over 213,500 different IP addresses in just six months. Note that AS 4134 is not limited to Hunan Telecom or the Hunan providence, as there are hundreds of organizations and subsidiary ISPs of CHINANET using this AS Number for routing.
For comparison, Figure Five (5) breaks down the top twenty organizations for observed activity between January and August, 2014, for AS 4134. The CHINANET HUNAN PROVINCE NETWORK was clear down at number 11 in the rankings, with other providences surpassing its suspect activity:
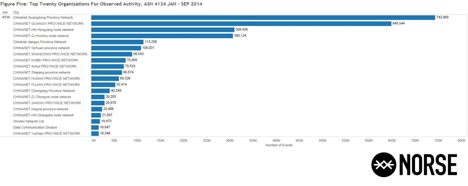 Figure Five (5): Top Twenty (20) Organizations For Observed Activity, January – August 2014.
Figure Five (5): Top Twenty (20) Organizations For Observed Activity, January – August 2014.
In an effort to better understand the activity from Hunan province, Figure Six (6) plots out the locations and amount of activity detected for the province. Note the overwhelming amount of activity from around Changsha (28°10’44.4″N 113° 06’50.4″E), far surpassing any of the other observed activity for this region.
This reveals geolocation coordinates similar to those derived from the Regional Internet Registry (RIR) information for the IP address in question (218.77.79.43), and they are located either in or very near what appears to be a major waterway, the Liuyang River:
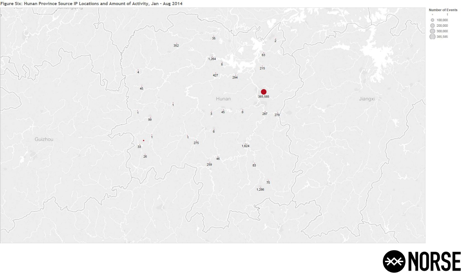 Figure Six (6): Hunan Province Source IP Locations and amount of Activity, Jan – Aug 2014.
Figure Six (6): Hunan Province Source IP Locations and amount of Activity, Jan – Aug 2014.
In an attempt to provide attribution, by using Google Translate the DarkWolf Labs took “people’s liberation army + Changsha” and obtained the Chinese translation. Searching for these terms in Google comes up with the National University of Defense Technology (NUDT), just a short distance away from the coordinates provided by the RIR:
 Figure Seven (7): Satellite View of National University of Defense Technology (NUDT) From Google Earth
Figure Seven (7): Satellite View of National University of Defense Technology (NUDT) From Google Earth
The main entrance of the campus is at the northern most point, as depicted in the following image posted on Panoramio.com by zxpsectrum16k:
 Figure Eight (8): Photo of Campus Entrance
Figure Eight (8): Photo of Campus Entrance
The following week, it came as no surprise that the IP address 218.77.79.43 remained in the top aggressor list for suspect activity, with over 55,180 unique events detected between the 3rd and 8th of September, 2014.
After some more initial analysis was released, one of our readers reached out to the team inquiring as to the attribution of this IP address, sharing with us the Network Threat Blacklist System web site of the Northeastern University Network Center in Shenyang City, Liaoning Province. The System shows 218.77.79.43 as being part of Hengyang Telecom ADSL, which had been seen hitting their systems repeatedly as well.
Figure Nine (9) below shows a screenshot from the Northeastern University Network Center Network Threat Blacklist System web site enumerating the most current “top ten” threats, with 218.77.79.43 ranking at eighth:
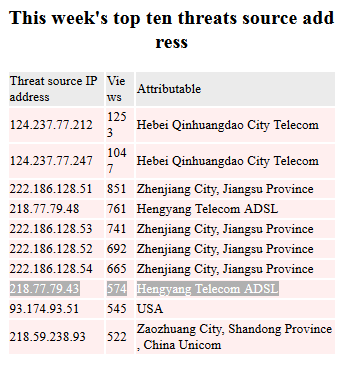 Figure Nine (9): Screenshot from Northeastern University Network Center Network Threat Blacklist System web site
Figure Nine (9): Screenshot from Northeastern University Network Center Network Threat Blacklist System web site
This raises the question as to who or what this IP address is really assigned to. The Northeastern University Network Center attributes this IP as Hengyang Telecom ADSL, but the information we receive from the Regional Internet Registry (RIR) regarding this IP is not nearly as concise.
As the screenshot in Figure Ten (10) indicates, there is no mention of Hengyang Telecom ADSL. The RIR provides the city as Changsha with a latitude and longitude nearby, and the ISP as CHINANET HUNAN PROVINCE NETWORK with the AS Name & Number as CHINANET-BACKBONE. Hengyang province is a considerable distance from Hunan province and the city of Changsha:
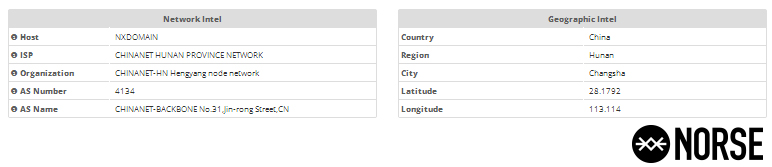 Figure Ten (10): Screenshot from Norse DarkViking regarding IP 218.77.79.43
Figure Ten (10): Screenshot from Norse DarkViking regarding IP 218.77.79.43
With the operators failing to provide truthful information regarding IP ownership and routing, the RIRs also cannot provide accurate information, and any attribution analysis can only as accurate as the information provided.
It is interesting to note that internal to China, the information seems to be more accurate than what is available from the RIRs – perhaps because it was purposefully being skewed at the RIR. Considering CHINANET is the ISP for the entire country, if ownership and routing information is not accurate or is falsified, it makes subjective analysis extremely problematic at best.
Clearly this IP is being a nuisance by scanning both internal and external hosts, and there should be concern regarding all traffic from this ISP – and potentially from this country in general – if activity of this nature continues to be tolerated.
With the activity observed from this province being just number eleven in the rankings, the members of DarkWolf Labs are curious to know what we will find in the activity from the other provinces and will continue monitoring this activity to provide analysis and additional information to help others recognize and defend against this malicious activity.
Mitigations
From a technical perspective, having a multi-layered defense is key to detecting and stopping malicious activity early, which also helps with overall detection rates, thus minimizing the impact to an organization when defenses fail.
A good methodology to start with for any organization would be the Council on CyberSecurity‘s 20 Critical Security Controls, which are geared towards addressing the key threats confronting networks today, as they are continuously being reviewed and updated.
An additional measure in your multi-layered defense is ensuring network and system monitoring and detection is in place through your IDS/IPS, with the alerts being fed into your log management/SIEM solution for review, analysis, and potential action.
Furthermore, organizations can take proactive action regarding suspect actors conducting scanning/reconnaissance of your infrastructure by using host based tools such as DenyHosts, FailToBan, or a Windows platform equivalent.
A more robust, supportable solution and force multiplier would be leveraging a robust threat intelligence (TI) platform, enabling you to block these miscreants and associated activity at your network boundaries, and clearly identify them in your log management/SIEM solution for review, analysis, and potential action according to your specific security policies and acceptable level of risk.
By Tim O’Brien, Director, Security Threat Intelligence & DarkWolf Labs, Norse Corporation
 Bio: Tim O’Brien is Director of Security Threat Intelligence & DarkWolf Labs at Norse Corporation. As a 15-year information security professional, O’Brien is a subject matter expert in risk and incident management, intrusion and data analysis, secure architecture design, and systems management. O’Brien is well versed in developing technical solutions, determining the best options for the business and its goals, and creating comprehensive implementation plans that minimize risk for the organization. His excellent analytical and problem solving skills, with emphasis on understanding relationships among technical problems, result in sound and effective business solutions while reducing risk. He enjoys mentoring others and helping them develop their skills through supervisory positions, coursework development, mentoring, presenting at and helping run information security conferences, as well as instructional positions. Tim can be reached online at to@norse-corp.com or at his company website .
Bio: Tim O’Brien is Director of Security Threat Intelligence & DarkWolf Labs at Norse Corporation. As a 15-year information security professional, O’Brien is a subject matter expert in risk and incident management, intrusion and data analysis, secure architecture design, and systems management. O’Brien is well versed in developing technical solutions, determining the best options for the business and its goals, and creating comprehensive implementation plans that minimize risk for the organization. His excellent analytical and problem solving skills, with emphasis on understanding relationships among technical problems, result in sound and effective business solutions while reducing risk. He enjoys mentoring others and helping them develop their skills through supervisory positions, coursework development, mentoring, presenting at and helping run information security conferences, as well as instructional positions. Tim can be reached online at to@norse-corp.com or at his company website .
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.