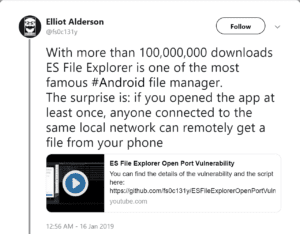
A serious vulnerability in a popular Android file has been discovered and exposes all the user’s data to attackers on the same network. In essence, the victim would only need to open the app once. This bug was found by researching Elliot Alderson, who posted about it on Twitter.
Expert Comments below:
Craig Young, Security Researcher at Tripwire:
 “The ES File Explorer ‘Open Port’ vulnerability is far more serious than originally reported. The truth is that attackers do not need to be on the same network as the victim phone thanks to DNS rebinding. With this attack model, a web site loaded on the phone or by any user on the same network can directly interact with the vulnerable HTTP server. This enables a remote attacker to harvest files and system information from vulnerable devices. An attack could be launched through hacked web pages, malicious advertising, or even a tweeted video.”
“The ES File Explorer ‘Open Port’ vulnerability is far more serious than originally reported. The truth is that attackers do not need to be on the same network as the victim phone thanks to DNS rebinding. With this attack model, a web site loaded on the phone or by any user on the same network can directly interact with the vulnerable HTTP server. This enables a remote attacker to harvest files and system information from vulnerable devices. An attack could be launched through hacked web pages, malicious advertising, or even a tweeted video.”
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.


