When we conceptualize of “the Internet,” we imagine it’s teeming with people from every corner of the globe, all offering opinions, information, content, and ideas – but this isn’t true. The silent majority of the Internet is actually comprised of bots: automated programs that run simple tasks numbering in the trillions. Every day, billions of bots are working to shape our Web experience by influencing the way we learn, trade, work, and interact with each other online.
Free eBook: Modern Retail Security Risk – Get your copy now.
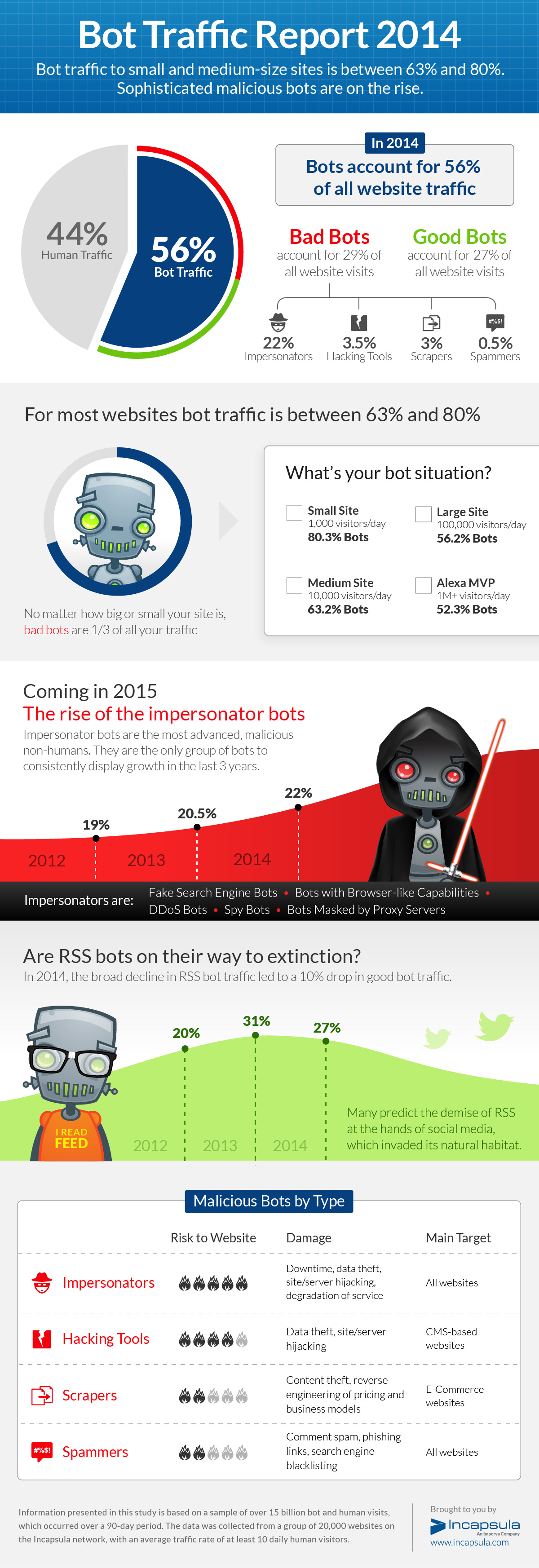
Every year, Incapsula researchers analyze bots in the annual Bot Traffic Report, a study that measures the amount of Internet traffic produced by both humans and bots. This year’s findings concluded that bots remain the majority of visitors to websites of all sizes at 56 percent. What is interesting, however, is that while bot traffic to larger websites is at 50 percent, smaller and medium websites—which represent the bulk of the Internet—are actually serving two to four bot sessions for every human visitor. In fact, Incapsula’s researchers found that bot traffic approaches 80 percent of traffic to small websites, with less than 1,000 daily visitors.
Most alarming is the 10 percent increase in malicious bot activity, which now accounts for almost 30 percent of all Internet traffic, regardless of website size. In absolute terms, Incapsula can state that malicious bot traffic grows in an almost exact proportion to a site’s human traffic.
Bots continue to evolve within the rapidly evolving Internet landscape, and we can expect them to become smarter and harder to detect in the coming year.
Enjoy the infographic below in which we summarize some of the findings from this year’s Bot Traffic Report.
 Incapsula’s cloud-based Application Delivery service enables businesses to simplify their IT operations and reduce costs by consolidating multiple appliances and services into a single cloud solution. Enterprises get best-of-breed security, load balancing, failover and a global CDN, without having to deploy, manage and integrate separate products.
Incapsula’s cloud-based Application Delivery service enables businesses to simplify their IT operations and reduce costs by consolidating multiple appliances and services into a single cloud solution. Enterprises get best-of-breed security, load balancing, failover and a global CDN, without having to deploy, manage and integrate separate products.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.