GlobalSign recently hosted a webinar discussing how to make access to sensitive data more secure. They surveyed attendees on the topic of multi-factor authentication, the level of security their organisation currently uses, as well as information surrounding their infrastructure setup. Their answers provided valuable insight into how today’s enterprises react to the current security threat landscape. Below is a summary of the findings.
Risky Single-factor Authentication Still Proves Popular
49% of participants only used username and passwords to access their organisation’s applications and online services. This result is somewhat of a concern given the vulnerability of the process. This also proved to be costly for the organisation and a burden for IT departments. Two-factor authentication (commonly provided through “something you have” and “something you know”) is definitely becoming the primary replacement.

Digital Identities are On The Rise
From the 51% of respondents already using two-factor authentication, the use of Digital Certificates was the most preferred option. Other methods have their own advantages, e.g. for Biometrics, “who you are” can’t be left or forgotten like a token, and one-time passwords are not vulnerable to replay attacks. Digital Certificates, however, prove to be the simplest and most cost effective method to secure enterprise infrastructures and are highly scalable and maintainable with the right certificate management platform.
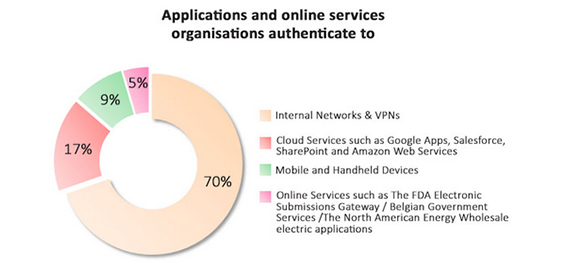
Organisations Authenticate to Internal Networks and VPNs as standard
Unsurprisingly, results showed that 70% of organisations authenticated to Internal Networks and VPNs, no doubt driven by the growing adoption of BYOD and Cloud solutions which each alter the effectiveness of traditional methods in securing information assets.
Depsite the Costs, Organisations prefer to Be in Charge
The most important question here is: Which infrastructure to choose when implementing a security solution?
GlobalSign has formerly referred to the fact that internal PKI solutions can be expensive, complex and risky and that poor key management can lead to costly outages. Nonetheless, internal CAs seem to take a lot of space in the marketplace, with 75% of respondents managing their own CAs, 22% of which also use a Trusted Root solution for external trust use cases. During the webinar, Amar Singh disagreed with this as best practice and recommended using an expert third-party CA. “From an organisational point of view and a security point of view, Internal CAs are not the way to go”. Indeed, using a third-party SaaS CA for PKI implementation proposes many benefits, enabling internal IT departments to focus on their core competencies, whilst reducing risk and maintaining flexibility.
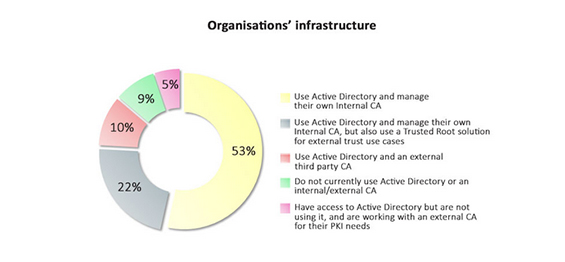
So is it better to be managing your own CA, paying extra and putting added pressures and burdens on internal IT and PKI specialists, or choose an external solution with experts who keep up to date more easily with the current threat landscape? It seems clear to GlobalSign at least, that external solutions are the way to go.
Topics covered included:
– Two-factor authentication methods
– Digital Certificates – The benefits and how they work
– Securing access to internal networks, cloud services and mobile device
You can view the webinar here.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.