Basically, you need to reverse engineer an app or a feature when you do not have source code, but still need to know how it works. If it sounds a bit suspicious to you, here are some all-legal business situations when reversing comes at hand:
- Researching and fixing complicated software issues
- Improvement of the interaction between a software system and the platform
- Advanced software system compatibility with third-party solutions
- Research of various types of malware.
Thus, being a rather complicated practice, iOS reverse engineering is very interesting and useful for a broad range of tasks. A large set of tools is available to help with this process.
Architectures
First, a couple of words about the internal architectures as it dictates tools selection and general reversing approaches.
iOS mobile devices are built using armv7, armv7s and arm64 CPUs. The corresponding reversing algorithms require researcher to be familiar with the instruction sets, calling conventions, and some things specific for arm (such as thumb mode or opcodes format)
As for the cache, system frameworks and dylibs are merged into a single file called shared cache, which can be found at /System/Library/Caches/com.apple.dyld/.
iOS Reversing Tools
Apple provides several standard command-line tools for iOS app research out-of-the-box:
- lldb. Quite feature rich default debugger in Xcode. It can be a useful C++, Objective-C and C code reverse engineering tool supporting debugging of the corresponding code on the desktop and iOS devices and simulators. It is based on the larger LLVM project re-using libraries such as its dissembler and others. See details: https://lldb.llvm.org/;
- otool. Complete console solution for exploring and in-place editing Intel and ARM binaries.
- nm. Console tool to browse names and symbols in mach-o executables. Get details here:
- codesign. A tool to get information as well as create and manipulate with code signatures. Get details here:
Besides standard tools for reverse engineering provided by the vendor, there are several very useful third-party utilities:
- IDA (Interactive DisAssembler). It is probably the most wide-known and popular disassembler. Being almost a reversing standard for complex tasks, this system should be mentioned among the best iOS reverse engineering software products. Get details here: https://www.hex-rays.com/products/ida;
- Hopper. Another interactive reverse engineering tool, native MacOS disassembler. It is a shareware with limited demo version. Get details here http://www.hopperapp.com/;
- MachOView. An alternative to otool and nm but with GUI, which enables mach-o file structure visualization. It is a freeware tool. Get details here https://sourceforge.net/projects/machoview/;
- class-dump. This tool allows dumping classes declarations from executable headers. Get it here https://github.com/nygard/class-dump;
- dsc_extractor – This tool can be used to extract libs and frameworks from dyld_shared_cache. When extracting, it saves locations and original names of all object that being extracted. It is provided by Apple as an open source software
IDA
IDA provides an ultimate feature set for an effective reverse engineering
As stated on the official website: “IDA is a Windows, Linux or Mac OS X hosted multi-processor disassembler and debugger that offers so many features it is hard to describe them all.”
IDA Pro includes such features, as:
- same interface for dozen of different processors
- multitarget debugger (supports different types of OSes)
- large and flexible plugin architecture
- great interactivity
- Intel & ARM x32 and x64 pseudocode generator
- Finally, IDA 6.9 (latest version at this time) supports pseudocode generation for ARM 64 binaries
In general, IDA has too many great features that it would require a separate large article to cover them all.
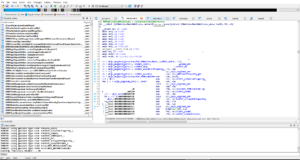
Hopper
Hopper is the macOS / iOS oriented disassembler. It is designed for macOS and Linux.
Using Hopper you can also perform reversing of any macOS / iOS binaries.
Some of Hoppers benefits:
- oriented to work with objective-C: specialized on retrieving obj-C specific information from the binary
- uses lldb or gdb as debugger
- most functions can be accessed from the python scripts
- displaying assembly, pseudocode CFG (Control flow graph) at the same time. That makes reversing more effective
- support of Swift names
- customizations: create own types, semantic coloration, user comments
All of the listed above makes reversing iOS applications with Hopper more effectively and comfortable.
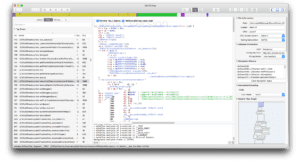
Using Tools to Reverse Engineer
The simplest reverse engineering task is to research ipa or app executable. The executable itself can be easily obtained: no problem at all for an app, and for an ipa, which is a zip archive, it can be found in the Payload/*.app subdirectory. Then any reversing tool from the list above can be used to work on this executable.
The more complicated task is to reverse engineer a part of iOS. It usually requires a jailbroken device, but even without it, you can try to get the file using the Document Interaction functionality.
If you cannot get an executable from the device, you can try the iOS simulator. The fact is that the simulator is based on the x86 architecture and thus its code differs from the one on a real iOS device. Nevertheless, daemons and frameworks interfaces correspond to those on iOS devices.
Reversing kernel extensions (.kext)
Sometimes it’s necessary to perform reversing on kernel extensions (also known as drivers on Windows). macOS kernel extensions are simple folders with .kext extension. They have bundle-like structure. The target file for reversing is the file with the same .kext name, located in /Contents/MacOS subfolder.
Reversing of kernel extensions is the same as reversing usual application. But be warned that majority of kexts are written partially with C++.
Conclusion
The process of reverse engineering on a closed platform like iOS can require significant time and efforts as well as a set of specific skills. Nevertheless, there are a set of iOS reverse engineering tools and approaches developed to facilitate this task.
[su_box title=”About Dennis Turpitka” style=”noise” box_color=”#336588″][short_info id=’101642′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



