SOC/NOC Integration Breeds Increased Efficiency and Effectiveness
SOCs (security operations centers) and NOCs (network operations centers) both serve vital functions in your network. And while each serves a different function, significant overlaps exist that can be leveraged to create more efficiency and effectiveness in your organization.
SOC staff must assess and respond to security events quickly to resolve cybersecurity issues before they can negatively impact the business, while NOC staff are responsible for making sure your network maximizes uptime and ensuring that bandwidth and demand can be managed properly.
Your SOC and NOC have demanding work that they need to deal with on a constant basis, but their goals are different. When your network has both types of operations centers, can they work together? Are there redundancies that can be dropped?
Maximize Focus: Identify and Eliminate SOC/NOC Redundancies
Redundancy is great when it comes to how many network appliances, servers and data storage devices you have. You should have some extra infrastructure, so you can continue to address network demands when a component fails, or to adequately manage through periods of high network demand.
But, when it comes to your SOC and NOC repeating tasks and functions, redundancy can be inefficient and costly for your organization. What if you integrated your SOC and NOC? Are there benefits?
Let’s say a network anomaly is discovered. A device stops working, for example. Someone who thinks like a SOC analyst will consider if the device was subject to a cyberattack. Someone who thinks like a NOC analyst will consider if the device failed for some non-cybersecurity related reason. If the SOC can’t find indications of a cyberattack, then they move on. If the device is malfunctioning because of a cyberattack, the NOC might not be equipped to recognize it.
In this case – and a myriad of others that occur daily in SOCs and NOCs around the globe – it would be much more efficient if the SOC and the NOC joined forces instead of duplicating efforts. Separately, security operations and network operations may fall prey to the problems of one hand not knowing what the other hand is doing. Together, an enterprise can save significantly on labor costs by combining the centers and improve its overall effectiveness.
Bringing Your NOC and SOC Together
Both NOCs and SOCs have incident and response teams, call centers and monitoring. Both centers work hard to assure the integrity and availability of your IT assets and can work well together, yet few enterprises truly integrate these functions.
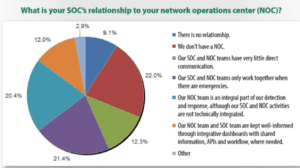
Source: Crowley/SANS 2017
Of course, how you go about bringing the two teams together determines your level of success.
A properly integrated SOC/NOC, otherwise known as an Integrated Operations Center (IOC), converges on three different levels:
- Organizational level: entails cross-correlating, pattern identification from shared NOC/SOC monitoring tools, triaging and collaboration.
- System level: entails standard operating procedures, process integration and service level agreements (SLAs.)
- Asset level: entails the shared use of a common information aggregator that collects all of the pertinent network monitoring data and logs and distributes it through integrated tools and dashboards.
The potential for improved incident response and overall network efficiency should be obvious already. Let’s look at what it means for the various levels in the NOC and SOC.
The most integration can be done at tier one. This level has similar functions in both SOCs and NOCs – alert monitoring, alert triaging and monitoring the health of both network and security sensors.
Tiers two and three are where we start to see greater variation.
| SOC | NOC | |
| Tier 2/Level 2 | Security incident analysis, remediation advice and support for new methods of threat detection. | Coordination with network and infrastructure vendors, support for fault management and change execution. |
| Tier 3/Level 3 | Incident hunting, developing new threat detection analytics, threat intelligence, forensics and malware reverse engineering | Problem management, change validation and performance monitoring and reporting. |
Even with these distinct functions at the higher levels, it is possible to create a cohesive integrated operations center through the use of a security orchestration platform that acts as a unifying fabric for the NOC and SOC. Applying security orchestration this way brings together the various technologies and processes used by both sides of the house to streamline day-to-day activities, resolve incidents faster and centralize collaboration.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



