As of April 15, the Chinese cyber community had begun to investigate the most recent release of malware from the Shadow Brokers group. Security researchers and cyber actors reversed several of the tools and were particularly interested in the exploit framework (named FUZZBUNCH), the SMB malware (ETERNALBLUE), and the privilege escalation tool (ETERNALROMANCE).
Chinese-speaking actors additionally focused on the unique malware trigger point and some claimed that the patches for CVE-2017-0143 through -0148 were insufficient because they did not address the base code weaknesses.
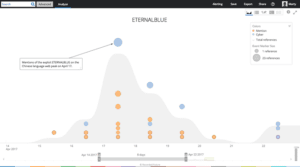
Mentions of one of the tools, ETERNALBLUE, on the Chinese language web over time.
 Mentions of Shadow Brokers-released malware on the Chinese language web and from Recorded Future sources.
Mentions of Shadow Brokers-released malware on the Chinese language web and from Recorded Future sources.
The surprising recent release has also stirred up great interest among Russian-speaking cyber criminals. Only three days after the data was leaked, a well-respected member of the top-tier dark-web community provided a detailed setup tutorial of weaponizing the ETERNALBLUE exploit as well as the DOUBLEPULSAR kernel payload.
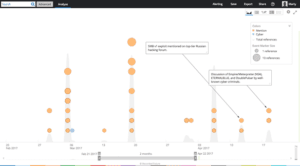 Mentions of one of the tools, ETERNALBLUE and DOUBLEPULSAR, on the Russian language web over time.
Mentions of one of the tools, ETERNALBLUE and DOUBLEPULSAR, on the Russian language web over time.
In a separate thread, another member of the community, solicited help from other members in utilizing a proper exploit for a vulnerable Server Message Block version 1 (SMBv1), identified at the time of scanning a victim’s environment. Several members recommended using the recently released ETERNALBLUE exploit and admired its usefulness.
Background
Shadow Brokers is probably a hacker group that first came to public awareness in August 2016. While membership of the Shadow Brokers group remains unknown, it has both advertised for sale and publicly released hacker tools and exploits which the group claims were written and used by the U.S. National Security Agency (NSA).
Impact
Discussions in the Chinese and Russian cyber communities indicate that there is broad interest in these capabilities released by Shadow Brokers. Chinese users are particularly interested in the unique malware triggers and many feel the underlying vulnerability exploited by these toolsets has not been completely mitigated by the patches.
Further, Chinese APT groups have demonstrated an ability to quickly weaponize zero-day vulnerabilities, in as little as three days after public release in one instance. These three factors combine to increase the risk that malicious Chinese actors may reuse or repurpose this malware.
Recorded Future customers should set up alerts on these tools and the corresponding vulnerabilities, patch critical systems immediately, and remain vigilant to unique variations on these exploitation techniques.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



