It has been reported that a coin-mining malware infection previously only seen on Arm-powered IoT devices has made the jump to Intel systems. Akamai senior security researcher Larry Cashdollar says one of his honeypot systems recently turned up what appears to be an IoT malware that targets Intel machines running Linux. It is fine-tuned for intel processors by establishing a SSH (port 22) connection and deliver it as a gzip archive. It creates three different directories with different versions of the same files. Each directory contains a variation of the XMrig v2.14.1 cryptocurrency miner in either x86 32bit or 64bit format and some of the binaries are named after popular UNIX utilities such as ps to make it harder to detect.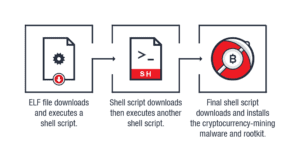
ThreatsHub Cybersecurity News | Coin-mining malware jumps from ARM IoT gear to Intel servers – https://t.co/YPYW0Gj8bV #CyberSecurity #Coudsecurity #ThreatIntelligent #Databreach #Deeplearning #OSINT #CyberCrime #Infosec #Blog #News pic.twitter.com/65olxvDkif
— ThreatsHub (@threatshub) August 31, 2019
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



